In the contemporary digital era, cloud computing includes servers, storage, databases, networks, and software, delivering vital services via the Internet. Its scalability, adaptable resources, and expedited migration capabilities provide customers with substantial economies of scale. This enables them to store data more economically than conventional approaches. The cloud-based solution ensures that customers and colleagues are informed, offering security and accessibility from any place via any mobile device. The advent of cloud computing and the growing acceptance of the Storage as a Service (STaaS) model have resulted from the revolution in data storage brought about by distributed storage systems. This revolution is bringing unmatched scale, flexibility, and ease of use to data management, storing, and access for organizations and individuals. Cloud storage has become a foundational technology in the era of big data, making it easier to store and retrieve data through web services and networks.
Today, every organization must figure out where exactly Cloud Computing (CC) is needed in their business to gain competitive advantage in their business. A distinctive characteristic of cloud computing is the pay-per-use model, wherein users are charged solely for the services they utilize [1]. It includes a variety of services including Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). These services include Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), IBM Cloud, and more. It is offered by both large companies and small retailers. It is worth billions of dollars and is expected to continue growing. Factors such as the business environment, the rise of decision-making information, the Internet of Things, the rise of intelligence, and the need for technical education are driving growth from these models. The global cloud computing industry was valued at USD 480 billion in 2022 and is projected to attain USD 2.29737 trillion by 2032, exhibiting a compound annual growth rate (CAGR) of 17% from 2023 to 2032 (Figure 1) [1].
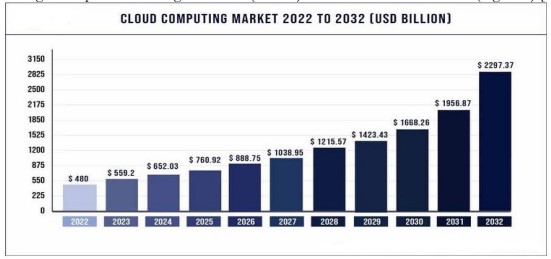
Figure 1. Cloud Computing Industry Market Size Worldwide, 2022 – 2032 [1]
The cloud computing market in the United States is projected to attain US$97.44 billion in 2022 and is anticipated to develop to US$458.45 billion by 2032, exhibiting an annual growth rate of 16.80% from 2023 to 2032 (Figure 2) [2].
Over the past decade, the internet and web-based services have experienced significant growth and are utilized by all companies. However, the rising costs of data storage and energy consumption are prompting large companies to invest in research aimed at reducing expenses. They are focusing on optimizing the use of existing resources and developing solutions to address these challenges through innovative studies. Cloud computing represents an innovative approach to resource utilization and optimization. It offers a fresh solution for effectively leveraging resources to their fullest potential. This technology addresses a wide range of hardware and software requirements, making it an invaluable tool in today’s digital landscape. The unique features of cloud computing have significantly enhanced its utility across various applications [3].
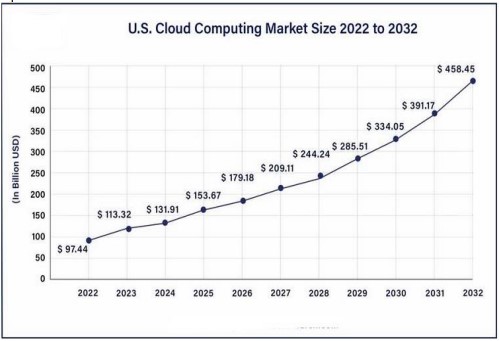
Figure 2. US Cloud Computing Market Size, 2022 – 2032 [2].
In this research paper, we discussed related work to highlight the contributions of various researchers in emphasizing the importance of cloud computing. We compared the findings and methodologies of different studies to provide a comprehensive overview of the advancements in this field. In our proposed methodology, we elaborated the specific strategies and technologies we employed, underscoring our unique contributions to cloud computing. Our approach offers several advantages and innovations that enhance current practices. In the implementation section, we thoroughly described our research process and the practical applications of our cloud computing study.
Go Drive Net has become a major player in the cloud storage industry by offering large storage capacity and producing solutions to meet the diverse needs of users. By examining the interface and identified requirements within the current documentation, we offer methods to enhance the organization of cloud storage services by emphasizing interactive communication to improve collaboration and interaction among users. Through this survey, we point to contribute to the current wrangle about on cloud capacity and make recommendations for future advancements in imperative regions of cloud computing. Through Go Drive Net, users may effortlessly connect with one another utilizing search functionalities to circumvent data storage restrictions. Additionally, powerful features such as data storage and connectivity enhance productivity, allowing users to collaborate more effectively and access information seamlessly. Go Drive Net provides an innovative viewpoint on demand and expenses. Every user on the site possesses a customized profile replete with comprehensive information, cultivating a feeling of community and enhancing collaboration among users. Users can search for others based on specific criteria and easily start conversations, improve communication and share information. This feature not only improves the user experience but also encourages collaboration between people with similar interests or skills. This technology advancement offers prospects for innovation, improved information storage, and the potential to redefine cooperation boundaries. In the digital domain, information basically pertains to human interaction with it. Information in the digital world is about how people interact with it. Based on secure cloud storage and powerful network connectivity, Go Drive Net goes beyond traditional storage facilities by integrating data management and instant messaging. This new approach is very important in terms of user experience and efficiency by meeting the needs of different customers in every field, personal or professional. Combining secure cloud storage with rich communications with end-to-end encryption, it not only facilitates effective communication but also provides a secure environment for the exchange of sensitive data. In an era when data privacy and security are important, Go Drive Net is a beacon of trust and ensures that users' data is safe from prying eyes.
In the section on related work, the research conducted on cloud computing explains the studies, provides references, and presents a brief comparison of these studies based on important factors. In the proposed methodology section, the research describes the system overview, system design, and software architecture. The hardware and its functionality are outlined, demonstrating how this research improves existing methods. A major contribution of this work is the integration of a file-sharing and friend management system, allowing users to move files seamlessly and share cloud data across other users. Additionally, personalized user profiles enhance the experience, offering tailored cloud storage solutions. The data flow is explained, and the database model is presented, followed by a detailed description of the implementation process that showcases the software's appearance and functionality. Finally, the findings are summarized, and suggestions for future improvements are offered.
Related Work
In recent years, the intersection of cloud storage and communication technology has attracted researchers and professionals. This section provides an overview of existing literature and studies on the integration of these projects. Google Drive [4], Dropbox [5], One Drive [6], iCloud [7], Elephant Drive [8] and Go file [9] are the most widely used platforms in personal and professional environments. These platforms allow users to store, connect and share data across various devices and locations. Data Security and Privacy Protection for Cloud Storage [10] is important. This study, however, does not include collaborative elements. Go file offers a variety of solutions for storing, distributing, and managing files. The provided alternatives accommodate various needs, whether for long-term data storage, team collaboration, audience distribution, or application storage systems. [9]
Drago et al. [11] proposed a method to compare five popular cloud services, including Dropbox, SkyDrive, Google Drive, Wuala, and Amazon Cloud Drive, to reveal their differences in architecture and performance metrics to measure their differences and working ability. The cloud storage service features they identified include sharing, packaging, client-side deduplication, incremental encoding, and data compression. They examine the prospective advantages for clients utilizing cloud storage services, concentrating on elements such as synchronous launches, completion durations, and overall efficacy.
Bock et al. [12] describe three cloud storage services: Dropbox, Google Drive, and OneDrive. They look at connection frequency (meaning the ratio of the size of a given TCP stream to the time stream), user productivity, data usage (when data is stronger), and delivery. They reported that Dropbox and Google Drive users download more content than they usually do, while OneDrive users see a different pattern. Other studies [13][14] focus on digital forensic analysis of cloud storage services by analyzing all artifacts created by various devices. Botha et al. [15] observed that applications surged in popularity primarily due to the swift proliferation of mobile phones and the Internet, and secondarily due to the decrease in conventional text messaging, especially with dating applications promoting enhanced long-distance communication. Telegram (Telegram, 2019) informed its users about the necessity for safe digital communication following the Snowden disclosures. It provides client-server encryption for chat and secret conversations to prevent privacy violations [16].
Signal was developed by Open Whisper Systems, and Edward Snowden asserted: "Anything that utilizes Open Whisper Systems". Signal uses military-grade end-to-end encryption. Signal is powered by an open platform that is monitored and analyzed for additional security. It is the preferred application among employees and security professionals (Signal, 2019) [17]. As a descriptor, "social networking" refers to various personal cloud computing platforms and the ability to chat online. "Cloud computing" refers to the use of web-based applications to process user data. In other words, the program and the data, information, or files created by the program are not located on the user's hard drive, but on the host computer's remote network server.

Figure 3. General Diagram or a Proposed System.
The most popular examples of social networking and cloud computing are sites such as Myspace, Facebook, Flickr, YouTube, Twitter, and Delicious. All of these platforms provide a variety of user controls that allow for the creation of personal connections, such as the ability to "add friends," "subscribe" to a channel or feed, "follow" other users, and the option to subscribe to content in a "feed" to "read." They also provide sub-platforms for blogging on Myspace pages, sending direct messages to users via the web interface or via mobile-enabled SMS (Simple Messaging System) texts, and uploading various digital content such as videos, photos, and tweets [18].
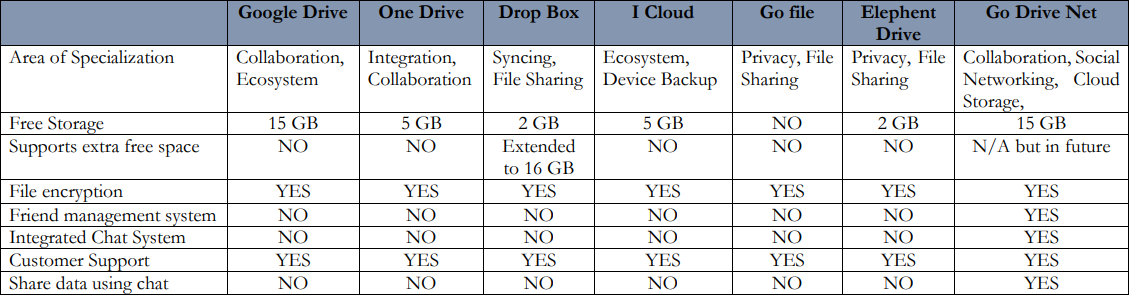
Nowadays, social networks and cloud computing are often used in tandem across various applications [19]. The two prominent approaches involve either integrating cloud computing with social media platforms or utilizing social media to enhance cloud-based services. In social cloud computing, cloud-based applications use social networks to provide personalized service and user control. Most organizations use cloud computing to complete their work mostly through social media [20]. However, these companies face many challenges in protecting their customers' datasets and other sensitive information. [21] Based on important criteria including area of expertise, free storage, file encryption, and special features like friend management and integrated chat systems, this table summarizes the primary distinctions between the most widely used cloud storage services.
Table 1. Difference Table among Important Factors.
Proposed Methodology
The performance analysis of Go Drive Net was conducted to evaluate its effectiveness in delivering a seamless and efficient user experience. The analysis encompassed various key aspects essential for assessing the platform's performance. The current study prioritizes user experience and efficiency, focusing on creating intuitive interfaces and utilizing the latest technology for seamless connectivity. The development phase focuses on selecting the appropriate technology and creating a structure that can provide stability and security. Prototyping and retesting allow us to incorporate feedback from stakeholders to improve the system. The authors provided comprehensive user support after deployment and continue to collect feedback for further development. With this step, we aim to use Go Drive Net as a revolutionary system that allows users to access the digital space easily, efficiently and securely with additional functionality. Here, we briefly present the architecture of our proposed system (Figure 3).
System Overview
For this study, the authors developed a web application designed to fulfill various user needs. This multifunctional platform offers real-time chatting, free cloud storage for users data, and connectivity features to engage with friends, all within a personalized profile environment. Users can save and access their data ubiquitously, without incurring any charges. This integration not only enhances the user experience but also encourages collaboration and cooperation between students and teachers.
System Design
The Go Drive Net is a client-server approach and follows specific hardware and software architecture. It is designed to be lightweight and accessible across various devices with web browsers (Figure 3).
Software Architecture
The main functions of the application are the following.
Frontend
HTML is applied to embody the frontend GUI, CSS to style the GUI and JavaScript for making the interface dynamic. They are implemented by using several AJAX (asynchronous JavaScript and XML) calls which provide the ability to update only certain components, rather than the whole page as needed (for example, new chat messages changes to a profile picture). App interface (UX) design by iterative testing with users.
Backend
On the back end, PHP deals with ordinary form submissions, as well as AJAX calls to pull new content from the servers.
Database
SQL commands intended for either the retrieval or conservation of data in a MySQL database.
Secure Communication
To secure the application, sensitive user data stored in the database is encrypted with AES-128-CTR (Advanced Encryption Standard in Counter Mode), and the Frontend and backend use HTTP Secure which implements Transport Layer Security (TLS) standard to ensure a secure socket layer secure all communication between the frontend and the backend.
Together these components offer the full-stack infrastructure for giving out the services of the web application to the users using standard technologies secure and dynamically.
Hardware Architecture
The basic requirement for Go Drive Net cloud storage is an Android device or computer that can run the web application. Users will use this platform to store their information and communicate with others, making connections and forming friendships.
Data Flow
When the user engages the Go Drive Net web application, the set from the web application to the server and to the database follow a various set of data flows. From the initial access by a new user to continued use by an existing user, the data is passed between the frontend, backend, and database layers as follows:
Web Application
This Web application collects data from the user, such as their images, videos, files, documents etc. This data is stored remotely on the web app server.
Network Communication
When the user interacts with the app and performs actions like logging in, uploading files, or chatting with users, the app establishes a network connection through the internet.
Data Encryption
To ensure the security of the transmitted data, the app use encryption to save the user's sensitive information before sending it over the network. This ensures that the data cannot be intercepted or accessed by unauthorized parties.
Message Encryption
End-to-end encryption signifies that messages are encrypted during transmission, ensuring the absence of non-confidential copies on the service provider's servers. Messages cannot be viewed by anyone other than the person communicating with them: no third party, not the government, nor the developers of these applications. Communications are sent using encrypted codes rather than clear text [22] shown in (Figure 4).
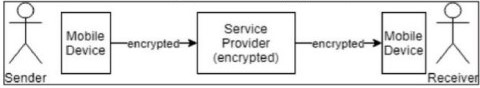
Figure 4. End-to-end encryption
Network Protocols
The app uses network protocols, such as HTTPS (Hyper Text Transfer Protocol Secure), to establish a secure and encrypted connection with the server.
Database
The server communicates with the database to store and retrieve information related to the users, including user details, messages, connections, and other relevant data. The database serves as the repository for all data, facilitating easy retrieval and management of information. The database flowchart of Go Drive Net is shown in (Figure 5).
Data Storage
The database stores the received data securely and ensures its integrity. It can use appropriate database management systems (MYSQL) to handle structured or unstructured data efficiently. Security measures, like encryption, are used throughout this data flow process to safeguard the user’s sensitive data. The confidentiality and integrity of the transferred data are guaranteed at every stage of the process through the use of secure network protocols and adherence to best practice.
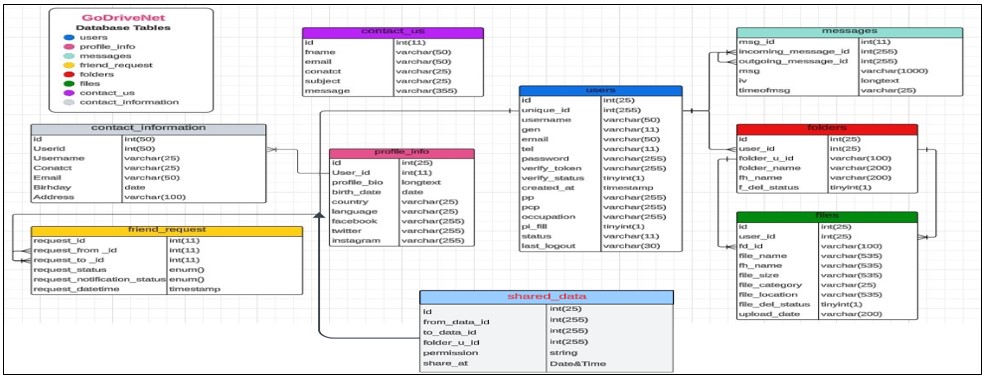
Figure 5. Flowchart of Go Drive Net database structure.
Analysis of Go Drive Net's Unique Features
Here are key points that differentiate Go Drive Net from existing solutions:
Unified Platform for Cloud Storage and Social Networking
Go Drive Net combines the features of cloud storage and social networking platforms to offer their user more comprehensive data storage options and social platform.
Friend Request and Communication Feature
Go Drive Net also supports particular social features that include friend requests and messaging to support enhanced forms of interaction in addition to the basic function of sharing files.
Data Sharing via Messaging
The capability to share any data of Go Drive Net is also as easy as the messaging apps instead of using links or emails like the other platforms.
Copying Data Across Folders
This feature allows users to not only move but also copy files from one directory to another without downloading and then re-uploading.
Enhanced User Engagement
By satisfying more user necessities – storage, upload/download, link up – Go Drive Net promotes more frequent and dynamic platform usage a response to standalone drives.
Implementation
The main difficulty comes from the integration of hardware and software. Given its complexity and interconnectedness, seamless integration of hardware and software poses a significant challenge for the overall functionality of the system.
Home Page
The homepage (Figure 6) functions as the core of the application, allowing users convenient access to all functionalities. It greets users with an engaging overview of the application's features and advantages. The homepage employs captivating imagery and succinct content to facilitate an efficient onboarding process for prospective users. Users may effortlessly sign in and register. The intuitive design guarantees user-friendliness and enhances overall timekeeping efficiency.

Figure 6. Homepage for User's Application
Login Screen
The login screen acts as a gateway to the application and provides secure access to user accounts. The access page is the access point of the website application and is divided into general access to the website and private, user-specific access to website resources. Therefore, access points must be protected with great care.
Profile Page
Profile pages generally refer to web pages designed to display personal information based on a user's information, preferences, and past interactions. It represents information regarding a user's identity.
Friend request System
A friend request is started by the user by choosing another user on the network. Database update: After verifying that the peer requests are legitimate, the server adds the pending peer requests to the database. Accept or decline friend requests (Figure 7)
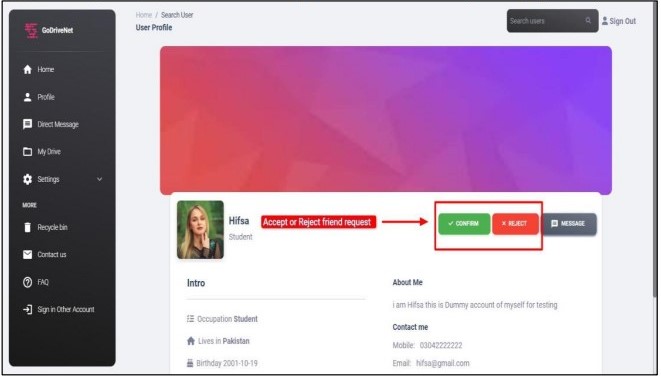
Figure 7. Friend Management System
Direct Message Page
The web app has a direct message page where users can search for other users to chat with. After searching, they can easily initiate a chat with the searched user in the inbox. The messages are end-to-end encrypted (Figure 8).
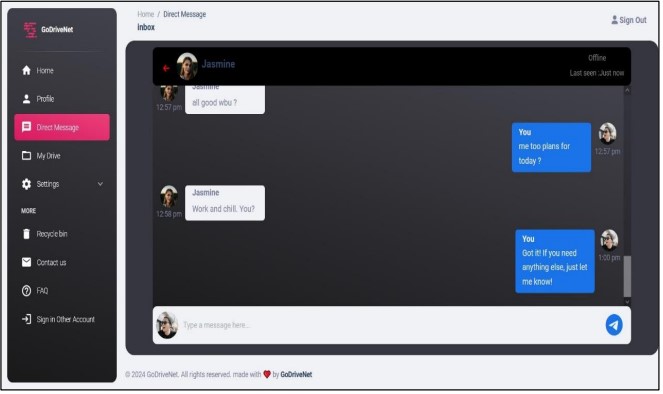
Figure 8. Direct message page for User's Application
Drive Page
On the Drive page, users can create, rename, delete, and move files between folders or within existing folders. The Drives page displays the total usage amount, usage limits, and specific actions for photographs, files, and media files as shown in (Figure 9).
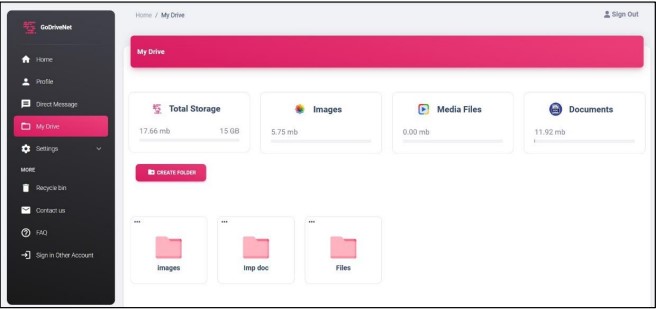
Figure 9. Drive page for User's Application
Share Data
End-to-end encryption protects all data sent over the chat system, guaranteeing anonymity for both sender and recipient. This ensures that your provided information is protected from access by third parties, including the platform itself (Figure 10).
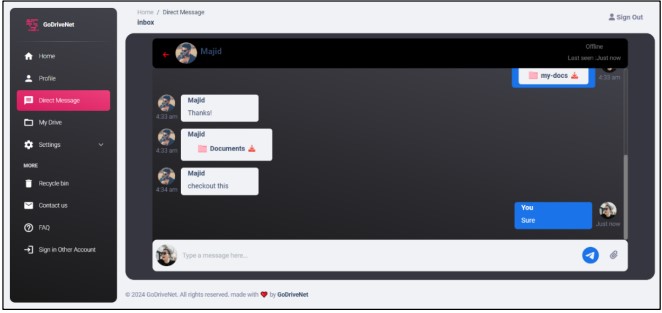
Figure 10. Sharing data using chat system
Settings Page
On the settings page, there are additional options such as updating your personal information, changing and verifying your e-mail address, permanently deleting your account, and easily resetting and changing your password.
Recycle Bin Page
Recycle bin page helps user to recover the accidentally deleted files and folders. User can recover or permanent delete these files easily.
Contact Us
The Contact Us page features a user-friendly form for submitting requests, concerns, and feedback directly to the team. This form establishes a direct communication channel between users and the staff, enabling prompt responses and tailored help. This communication technique aims to ensure consumers feel supported and valued by addressing particular inquiries not included in the FAQ. The acquired contact information facilitates the acquisition of important feedback from visitors, thereby enabling the ongoing enhancement of the website and services in accordance with user input.
FAQ (Frequently Asked Questions) Page
On the FAQ page, the most important questions from users about the website, the organization, and the offerings for free use are addressed. This section provides context for improving the Go Drive Net website and is often organized by topic or relevance to enhance user understanding. User information quickly; this can reduce bounce rate and increase customer satisfaction. It can also be an important tool for solving problems, educating users and increasing participation in the site.
Conclusion
Conclusion & Future Work
It is more crucial than ever for the digital forensic discipline to continue developing since both the public and private sectors are using cloud computing, especially cloud storage services. Determining the provider and user details in regard to data storage through cloud service providers is an essential component of an inquiry. Examiners will be able to locate possible data locations and take prompt action to secure the data as a result. Cloud computing is a revolutionary way to manage and deliver Internet services, providing businesses with significant benefits even in the face of challenges. Choosing the right cloud configuration is critical to service quality and competitiveness. Go Drive Net offers secure cloud storage and powerful communications capabilities to enhance collaboration, productivity, and information security by improving user experience and efficiency. We plan to explore advanced security measures, integrate machine learning for predictive analytics, and develop innovative data management technologies to enhance cloud services. Additionally, we will focus on integrating intelligent Chabot’s to facilitate user interaction and improve the platform's responsiveness to user needs.
Acknowledgement
All authors contributed equally.
Conflict of Interest: There exists no conflict of interest for publishing this manuscript in IJIST.
Project Details
This project was completed in June 2023, and resulted in a web-based application for real estate purposes.
Reference
[1] M. I. Malik, S. H. Wani, and A. Rashid, “CLOUD COMPUTING-TECHNOLOGIES,” Int. J. Adv. Res. Comput. Sci., vol. 9, no. 2, pp. 379–384, Apr. 2018, doi: 10.26483/IJARCS.V9I2.5760.
[2] “Cloud Computing Market Size to Surpass USD 2297.37 Bn by 2032.” Accessed: Sep. 27, 2024. [Online]. Available: https://www.precedenceresearch.com/cloud-computing-market
[3] M. Hashemi, S., Monfaredi, K., Masdari, “Using cloud computing for e-government: challenges and benefits,” Int. J. Comput. Information, Syst. Control Eng., vol. 7, no. 9, pp. 596–603, 2013.
[4] “Google Drive: Share Files Online with Secure Cloud Storage | Google Workspace.” Accessed: Sep. 27, 2024. [Online]. Available: https://workspace.google.com/products/drive/
[5] “Dropbox.com.” Accessed: Sep. 27, 2024. [Online]. Available: https://www.dropbox.com/
[6] “Sign in - Microsoft OneDrive.” Accessed: Sep. 27, 2024. [Online]. Available: https://onedrive.live.com/login/
[7] “iCloud.” Accessed: Sep. 27, 2024. [Online]. Available: https://www.icloud.com/
[8] “Simple, Secure, Affordable Online Storage - ElephantDrive.” Accessed: Sep. 27, 2024. [Online]. Available: https://www.elephantdrive.com/
[9] “Gofile - Your all-in-one storage solution.” Accessed: Sep. 27, 2024. [Online]. Available: https://gofile.io/welcome
[10] P. Yang, N. Xiong, and J. Ren, “Data Security and Privacy Protection for Cloud Storage: A Survey,” IEEE Access, vol. 8, pp. 131723–131740, 2020, doi: 10.1109/ACCESS.2020.3009876.
[11] I. Drago, E. Bocchi, M. Mellia, H. Slatman, and A. Pras, “Benchmarking personal cloud storage,” Proc. ACM SIGCOMM Internet Meas. Conf. IMC, pp. 205–211, 2013, doi: 10.1145/2504730.2504762/SUPPL_FILE/CRIMC092S.PDF.
[12] E. Bocchi, I. Drago, and M. Mellia, “Personal cloud storage: Usage, performance and impact of terminals,” 2015 IEEE 4th Int. Conf. Cloud Networking, CloudNet 2015, pp. 106–111, Nov. 2015, doi: 10.1109/CLOUDNET.2015.7335291.
[13] F. Daryabar, A. Dehghantanha, and K. K. R. Choo, “Cloud storage forensics: MEGA as a case study,” Aust. J. Forensic Sci., vol. 49, no. 3, pp. 344–357, May 2017, doi: 10.1080/00450618.2016.1153714.
[14] F. Daryabar, A. Dehghantanha, B. Eterovic-Soric, and K. K. R. Choo, “Forensic investigation of OneDrive, Box, GoogleDrive and Dropbox applications on Android and iOS devices,” Aust. J. Forensic Sci., vol. 48, no. 6, pp. 615–642, Nov. 2016, doi: 10.1080/00450618.2015.1110620.
[15] J. Botha, C. Van ’t Wout, J. Botha, C. Van ’t Wout, and L. Leenen, “A Comparison of Chat Applications in Terms of Security and Privacy Network Threats View project Ant Colony Induced Decision Trees for Intrusion Detection View project A Comparison of Chat Applications in Terms of Security and Privacy,” 2019, Accessed: Sep. 27, 2024. [Online]. Available: https://www.researchgate.net/publication/334537058
[16] N. Modrzyk, “Building Telegram Bots: Develop Bots in 12 Programming Languages using the Telegram Bot API,” Build. Telegr. Bots Dev. Bots 12 Program. Lang. using Telegr. Bot API, pp. 1–277, Jan. 2018, doi: 10.1007/978-1-4842-4197-4/COVER.
[17] P. Bawane and A. P. Kannu, “Time varying sparse support recovery,” Signal Processing, vol. 161, pp. 214–226, Aug. 2019, doi: 10.1016/J.SIGPRO.2019.04.001.
[18] J. S. Bianco, “Social Networking and Cloud Computing: Precarious Affordances for the ‘Prosumer,’” WSQ Women’s Stud. Q., vol. 37, no. 1, pp. 303–312, Mar. 2009, doi: 10.1353/WSQ.0.0146.
[19] K. Chard, S. Caton, O. Rana, and K. Bubendorfer, “Social Cloud: Cloud computing in social networks,” Proc. - 2010 IEEE 3rd Int. Conf. Cloud Comput. CLOUD 2010, pp. 99–106, 2010, doi: 10.1109/CLOUD.2010.28.
[20] C. C. Aggarwal, “An Introduction to Social Network Data Analytics,” Soc. Netw. Data Anal., pp. 1–15, 2011, doi: 10.1007/978-1-4419-8462-3_1.
[21] “View of Cloud Computing Privacy Concerns in Social Networks.” Accessed: Sep. 27, 2024. [Online]. Available: https://www.ijcjournal.org/index.php/InternationalJournalOfComputer/article/view/673/396
[22] “Best Encrypted Messaging Apps of 2021 And Why You Should Use Them.” Accessed: Sep. 27, 2024. [Online]. Available: https://heimdalsecurity.com/blog/the-best-encrypted-messaging-Apps/











