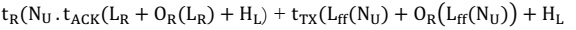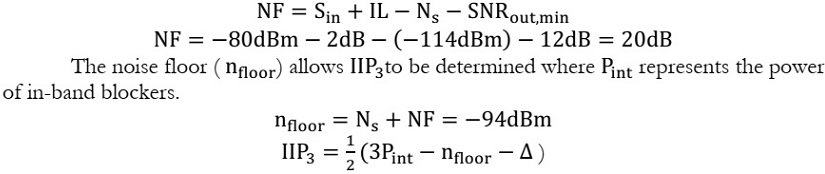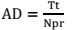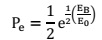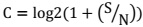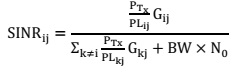The Internet of things describes devices with sensors, processing ability, software and
other technologies that connect and exchange data with other devices and systems over the
Internet over other communications networks [1][2]. IoT could have a couple of potential
benefits that offers seamless connectivity. The connectivity technology that is utilized in IoT
has less strength consumption, low bandwidth, low processing strength, and seamless
conversation with devices in its surroundings because the concept of IoT is processing for
anyone, everywhere and for any community. The utility of IoT to domestic appliances e.g.,
vehicles and others consist of the supply of smart objects which are capable to sense different
gadgets and are able to speak and interact with anyone without human interference or
intervention [3].

Figure 1:Architecture of Cellular Networks (COAI, 2019)
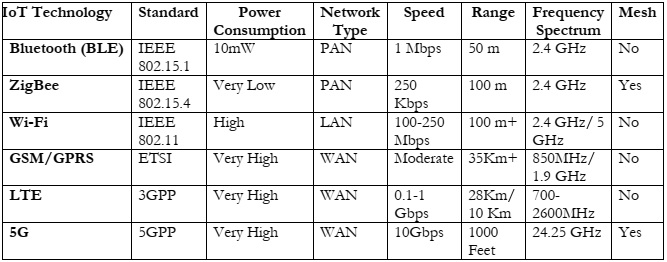
Communication Technologies Used for IoT:
Wi-Fi, NFC, RFID, Bluetooth Low Energy (BLE), ZigBee, and other diverse GSM
generations like 1G, 2G, 3G, 4G, and 5G are distinctive IoT technologies based on the size
of the network [4].
Table 1:Different Generations of Cellular Networks
All of those may be used to relate the shape and the value of the network, whether it’s
personal, widespread, or neighborhood [5].
Source: Odinma, A.C. 2006. “Next Generation Networks: Whence, Where, and
Whither”. Pacific Journal of Science and Technology. 7(1):23-30.
D2D Communication:
D2D communication is characterized as direct communication between two mobile
users without crossing the Base Station (BS) or core network, in cellular networks [6] and
cellular communication is accounted as D2D communication [7]. In a traditional cellular
network, all communications should be carried out via the BS, even if the contact parties are
beyond the limits of proximity-based D2D communication. BS networking is ideal for
traditional low-speed mobile networks like voice calls and text messages, where users are rarely
close enough for direct contact [8]. D2D communication benefits go beyond spectral
efficiency; potentially, it is possible to improve performance, energy efficiency, delay, and
fairness. In cellular networks, the figure below indicates D2D Communication [9]. The Cloud
Radio Access Network (CRAN) reinforces an adaptable operational framework for 5G
networks. A cautious storing technique in D2D correspondence that can enormously upgrade
the Quality of Experience (QoE) [10].
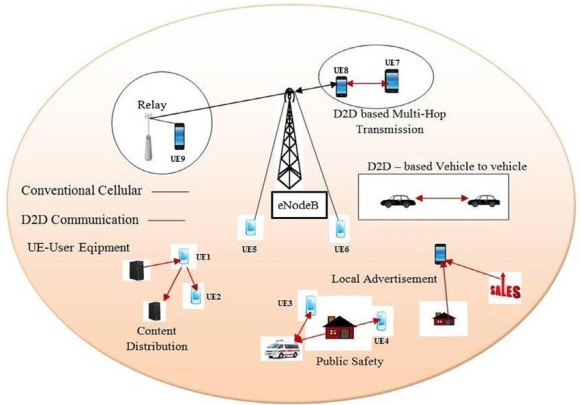
Figure 2:Framework of D2D Communication
Source: Valiveti, H. B., & Polipalli, T. R. (2019). Performance analysis of SLTC-D2D is a
mechanism in software-defined networks as per International Journal of Computers and
Applications, 41(4), 245-254.
D2D communication permits ultralow dormancy among gadgets and clients that can
be taken as an advancing innovation to support the future and an increase in exhibition of the
range [11]. The trading of information gatherings by D2D communication associated with all
the while under the umbrella of cellular networks is introduced and called the web of things
[12]. It takes a shot at both authorized and unlicensed ranges. The most important reason for
D2D correspondence is to flexibly a genuine time reaction in IoT [13]. Cell phones and gadgets
are developing quickly to shroud the day-by-day human necessities. Huge loads of
organizations and enterprises around the planet produce gadgets with various programming
and equipment frameworks, and to encourage the correspondence between these gadgets,
more examination, and recommendations of the most recent conventions may require giving
full similarity between different gadgets during a customary cellular organization. Gadgets
inside the endorsed cell range aren't permitted to talk straightforwardly with each other, and
each correspondence happen through the base stations [14].
D2D Communication in IoT Using 5G Networks:
In a standard cellular system, the permitted cellular bandwidth and all
devices are not
permitted to communicate directly with one another via the base stations [15]. Device terminal
relaying allows computers in a network to support each other as transmission relays and to
implement an immense ad hoc mesh network [16]. A two-tier 5G Cellular network with two
tiers of macrocell and device tiers is envisioned in this article [17]. Two-tier cellular networks
are given which includes a macrocell tier and a device tier. Four standard sorts of Tier
correspondence are portrayed in this article that include 1) Devices moving with managercontrolled association establishment (DR-OC), 2)
Direct D2D correspondence with overseercontrolled association establishment (DC-OC), 3) Device giving off with device-controlled
association establishment (DR-DC), and 4) Direct D2D correspondence with device
controlled association establishment (DC-DC) [18].
A few attributes of device communications that are utilized as a component for the
up-and-coming 5G networks in IoT are given in this article with High Data Rate or Low
Latency, Aggregation, and Coverage Extension, Low Energy Consumption Communication,
sight and sound IoT, and Multicast [19]. The vicinity-based administrations are the greatest
security hazard for D2D Communication. Future work for sheltered device communication is
to present some better safety efforts for the protected correspondence between gadgets
associated with 5G organizations [20].
Mobility Management in D2DCommunication Using 5G:
Like various remote communications systems, D2D communication
mobility
management is a critical test that can still not seem to be thoroughly investigated [21]. A
proposed model is likewise introduced to comprehend the issue of mobility management in
D2D communication [22]. Mobility management in gadget-to-gadget correspondence is a key
test that is yet to be developed [23]. The principle thought depends on TDD Configuration
from the recently distributed paper [24]. For the legitimacy of the proposed model the
reproduction results are given in this paper without versatility. Portability Management of any
remote correspondences was viewed as a high-need [25].
Intelligent D2D Communication:
To accomplish intelligent D2D communication in the environment of IoT, various
communication algorithms or protocols have been introduced [26]. These algorithms include
(a) Probabilistic Algorithm, (b) Bioinspired Algorithm, (c) Hierarchal Algorithm, and (d)
Context-aware Aware Algorithm. The principal reason for this investigation is the means by
which Intelligent D2D communication ought to be accomplished by utilizing diverse cuttingedge directing calculations [27]. These frameworks
can work exclusively and coordinate the
assortment, trade, and transmission of data in a multipurpose way without unified control.
Specialized gadgets are expanding each day, so by increment in the number of gadgets
correspond to slacks are likewise to happen like the speed of the correspondence, memory
being utilized and battery utilization [28].
Devices in D2D communication:
Several devices and technologies have are a part of D2D communication. Here are some
examples:
Smartphones:
Smartphones are commonly used for D2D communication, especially in scenarios like
file sharing, messaging, and collaborative applications. For example, features like Bluetooth,
Wi-Fi Direct, and Near Field Communication (NFC) allow smartphones to communicate
directly with other nearby devices.
IoT Devices:
Internet of Things (IoT) devices, such as smart home devices (smart
thermostats, smart speakers, etc.), wearables (smartwatches, fitness trackers), and industrial
sensors, can engage in D2D communication for local data exchange and coordination.
Vehicular Communication:
Vehicles equipped with vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I)
communication technologies can participate in D2D communication for improved road
safety, traffic management and coordination.
Wireless Ad Hoc Networks:
In wireless ad hoc networks, devices can form temporary networks and communicate
directly with each other without the need for a fixed infrastructure. This is often used in
military, disaster recovery, and other scenarios where a traditional network is unavailable.
Mesh Networks:
Mesh networks consist of interconnected devices that relay data, enabling D2D
communication within the network. This approach is useful in scenarios where coverage needs
to be extended or where traditional network infrastructure is limited.
P2P File Sharing:
Peer-to-peer (P2P) file-sharing applications enable devices to share files directly with
each other over the internet without going through a centralized server. Examples include
BitTorrent and various decentralized file-sharing protocols.
Proximity-based Services
Devices can communicate directly when they are in close proximity to each other. This
is used in location-based services, interactive marketing, and other context-aware applications.
Emergency Communication:
In disaster-stricken areas or situations where traditional communication networks are
compromised, D2D communication can be used to establish local communication between
devices.
Drones and Robotics:
Drones and robotic devices can communicate with each other directly for
collaborative tasks, swarm behavior, and coordinated actions. It's important to note that the
list above is not exhaustive and is continually evolving with new devices and technologies
being developed. The specific devices that participate in D2D communication can vary
depending on the use case and technological advancements.
Analysis of Different Communication Technologies:
IoT links a variety of devices to a network that exchanges
information easily,
exchanging data that allows humans and machines to communicate with each other freely [29].
It combines Bluetooth wireless networking, Wi-Fi, 5 G networks, and wired links such as
Ethernet cables. So, IoT devices are installed with a wide range of capabilities. CoAP, DTLS,
and MQTT, among others, provide communications protocols. IPv6, LPWAN, Zigbee,
Bluetooth Low Energy, Z-Wave, RFID, and NFC are wireless protocols [30]. This study uses
qualitative analysis design to analyze the quality of connected IoT devices using 5G [31].
D2Dcommunication has two main applications in licensed and unlicensed spectrums. In IoT,
various devices communicate through different communication technologies like NFC, RFID,
WiMAX, Bluetooth, Zigbee, or other communication technologies. By connecting these
devices various issues occur like signal attenuation, delay, and bandwidth issues [32]. In the
present study, communication technologies i.e. Bluetooth, Zigbee, and RFID in the
environment of IoT connected through 5 G analyzed and compared, on the basis of their
architecture and various parameters like SNR (Signal to Noise Ratio), Signal Attenuation,
Throughput and Delay, using mathematical modeling [33].
Bluetooth:
Bluetooth technology is a de-facto Wireless Personal Area Network (WPAN)
standard. The WPAN is an ad-hoc network of linked devices within a radius of 10 m.
Bluetooth Special Interest Group (SIG) published Bluetooth. IEEE 802.15 characteristics.
Bluetooth was developed for mobile devices, laptops, tablets, and others to be used as phones,
headers, and wearable devices (like smart Watches, and smart Shoes) [32].
Architecture of the Bluetooth is based on two types of networks 1) PICONET and
the 2) other is SCATERNET [34]. The fundamental architecture of the Bluetooth is shown in
the figure.
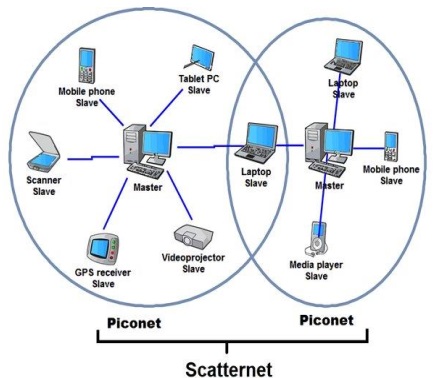
Figure 3:Bluetooth SCATTERNET Architecture
Source: Zanaj, E., Caso, G., De Nardis, L., Mohammad pour, A., Alay, Ö, & Di Benedetto,
M. G. (2021). Energy efficiency in short and wide-area IoT technologies—A survey.
Technologies, 9(1), 22.
The Efficient Cycle Algorithm for Bluetooth:
The set of rules for the Efficient Double Cycle (EDC) is based
primarily on essential
ideas: first, it is essential to avoid NULL transmissions closer to and from the slaves; secondly,
the normal equity of a Round Robin scheme should be maintained. These objectives will be
achieved if the selection of the slave to be polled takes into account the master's expertise of
occupancy of quarters queues [35]. Algorithms for multipath routing.

Zigbee Network:
Zigbee is the latest Wireless Personal Area Network (WPAN) standard established
based on IEEE 802.15.4 which is low cost, low power consumption, self-operation, short
distance, low complexity, and many more are the primary features of the Zigbee network.
Zigbee is usually used in the construction of automatic control, automation of industry, and
other fields such as households and hospitals. Devices from Zigbee create divergent networks.
These networks are (a) star topology, (b) cluster tree topology, and (c) mesh networks.[36].

Figure 4:Zigbee Network Topology
Source: Salih, M. A. A. A. M. (2012). Design and performance analysis of building monitoring
system with wireless sensor networks. Iraqi Journal of Science, 53(4), 1097-1102.
Cluster Tree Zigbee Algorithm:
In a cluster tree algorithm, each packet node evaluates the next jump related to the
node
address. The subsequent address for the routing node is denoted as A, and the depth is
represented by d, following the specified formula.
A < D < A + Cskip(d − 1)
Where Cskip(d) is a calculation function?
If the selected node is the successor of the receiver node, the further jump address is N:
N = D
If there is a terminal

Else

If the selected node is not the successor of the receiver node, the father node receives
the packet node.
AODVjr Algorithm:
This algorithm also deletes routing errors. It can prevent circulation problems and
invalid RREP packets. Hello packets are also deleted to get rid of the transmission types.

Figure 5:Pattern for AODVjr Algorithm for Searching And Communicating
Source: Li, J., Zhu, X., Tang, N., & Sui, J. (2010, July). Study on ZigBee network architecture
and routing algorithm. In 2010 2nd International Conference on Signal Processing Systems.
WIFI Network:
The structure of the WiFi community includes a hard and fast of APs (Access Point)
or includes one or more APs and one or more clients. One patron is without delay connected
to the only AP. The AP communicates with the patron through disseminate the Service Set
Identifier ( SSID) or community call via way of means of packets called beacons.

Figure 6:WiFi Network Architecture
Source: Khan, M. A., Cherif, W., Filali, F., & Hamila, R. (2017). Wi-Fi direct research‐current
status and future perspectives. Journal of Network and Computer Applications, 93, 245-258.
For connectivity or use in internet services, the WiFi network utilizes radio signals to
provide access to the internet or the mobile operator network. It only offers services up to the
level of the connection layer and therefore relies on the wired IP network for end-to-end
connectivity. The NAPT Gateway provides access to other IP-based networks as seen in the
figure, while the AAA server proxy manages access and authentication of mobile terminals.
WiFi employs a Remote Authentication Dial (RADIUS) protocol along with an Extensible
Authentication Protocol (EAP) to authenticate a terminal attempting to connect to the
network. Each Access Point (AP) in a WiFi network has a limited range that connects the
client to it. The actual distance varies depending on the environment, whether the client is
situated indoors or outdoors.
Table 2:Different Standards of IEEE 802.11

Source: http://bucarotechelp.com/networking/standards/81090201.asp
RFID Architecture:
RFID is an automated non-contact detection technology for accessing relevant data
through automatic target recognition of the RF signal. Until RFID is completely perceived, it
is imperative to see how radio frequency correspondence happens. By creating a special
electromagnetic wave impact at the source, the beneficiary can be seen a long way from the
source, which at that point distinguishes it and thus the data. The RFID label comprises a
receiving wire, a remote transducer, and an epitomizing film. A radio wire, handset, and
decoder is an RFID peruser that conveys occasional signs to ask about any close by tag. RFID
frameworks can likewise be recognized based on the recurrence range they use. The standard
ranges are low frequency (LF: 125-134.2 kHz and 140-148.5 kHz), high frequency (HF: 13.56
MHz), and ultra-high frequency (UHF: 868 MHz-928 MHz), suggesting that the architecture
is based on one of the other types of auto-ID systems, such as auto-ID optical barcode
systems. Barcodes supply product information through bars of varying width and space
between them. Using a barcode reader, also called a scanner, the barcode of the product is
captured to interpret the data for a specific product. In this instance, the reader is directly
linked to the cash register.

Figure 7:RFID Architecture
Source: Kolarovszki, P., & Vaculík, J. (2014). Intelligent storage system based on automatic
identification. Transport and Telecommunication Journal, 15(3), 185-195.
Network Architecture of D2D Communication:
The architectural design of D2D network include components which are
divided into
local network, network management, and D2D applications. The local D2D network contains
a wide variety of devices and communicates through direct contact. After they have been
integrated into the network architecture, aggregators collect information from all D2D devices
and link it to the main network. This information will be sent to the gateway which connects
to the access network. The linking of network may be thorough wired or wireless.
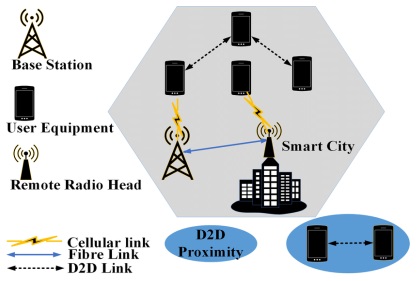
Figure 8: 5G Enabled D2D Communication Network Architecture
Source: Edris, E. K. K., Aiash, M., & Loo, J. (2019, August). Investigating network services
abstraction in 5G enabled D2D communications.
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI) (pp. 1660-1665). IEEE
D2D Communication Types:
On the basis of spectrum allocation D2D communication is further categorized into
2 types 1) Inband and 2) outband.
In band D2D Communication:
Mobile communication and D2D communication are licensed by the same set of
mobile operators. For D2D and cellular contact respectively (overlay), the licensed spectrum
may be divided into non-overlapping portions or may not be subdivided at all (underlay). It is
simpler to enforce the overlay scheme, but the underlay scheme leads to an opportunistic and
therefore more efficient use of spectrum and improved operator income.
Out band D2D Communication:
D2D communication uses unlicensed spectrum where cellular communication does
not occur (e.g. the free 2.4 GHz ISM band or the GHz mm-Wave band). Although
interference from other electronic devices (such as Bluetooth and Wi-Fi) operating in this
band is still present, this helps to minimize interference between D2D and cellular users. When
using a licensed spectrum, operators can control interference, but this is not feasible for the
outbound scheme.
5G Network Architecture:
The All-IP-based stage for Wireless and Mobile Network Interface Networking is
found in the organization design proposed by a structure model for portable 5 G
organizations. The PC consists of a client terminal (which assumes a basic part in the new
engineering) and various free, independent advancements for radio access. Every innovation
for radio access is utilized as an IP association with Internet's outside world. In any scenario,
there will be independent radio interfaces for each Remote Access Technology (RAT) in the
portable terminal e.g., we need admittance to four unique RATs, to make these engineering
practices, we have to give four distinctive access interfaces in the versatile terminal and have
them all dynamic. Radio access developments with basically QoS maintain parts that give
Internet access and are portrayed in the underlying two levels of OSI (data interface level and
real level) which is dependant upon the establishment of radio access (for instance 3 G and
WiMAX have strong QoS maintenance, yet WLAN doesn't). The association layer is over the
OSI-1 and OSI-2 layers, and in the current frameworks organization world, either IPv4 or
IPv6, paying little brain to radio access propels, this layer is IP (Internet Protocol). Bundle
guiding should be finished according to set-up customer methodologies. The action of the immaculate stages inside the current show stack,
which shape the proposed design, is
presented in Figure 10:

Figure 9:Mobile Network Architecture of 5G
Source: Tudzarov, A., & Janevski, T. (2011). Design for 5G mobile network architecture.
International Journal of Communication Networks and Information Security, 3(2), 112-123.
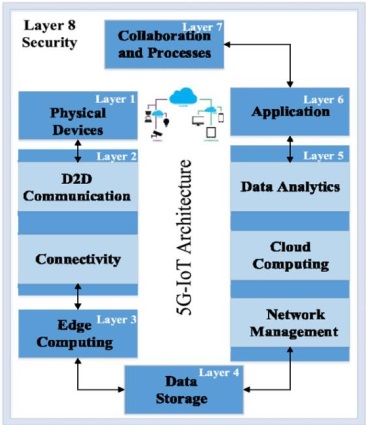
Figure 10:Protocol Layout for the Proposed Architecture
Source: Meenal G. Kachhavay et al, International Journal of Computer Science and Mobile
Computing, Vol.3 Issue.3, March- 2014, pg. 1080-1087.
5 G-based IoT Architecture:
The 5 G-based IoT Architecture is expected to provide applications with all of the
wireless, reconfigurable, and social interfaces available on demand in real-time. 5 G-based IoT
Architecture provides the following:
• Provide logically separate networks to fulfill the needs of submissions
• Using cloud-based radio access network (Cloud RAN) to restore Radio Access
Network (RAN) to have huge multiple connections standards and enforce RAN
functions on-demand 5 G Needed.
• Simplify main network architecture to enforce network feature configuration
on demand.
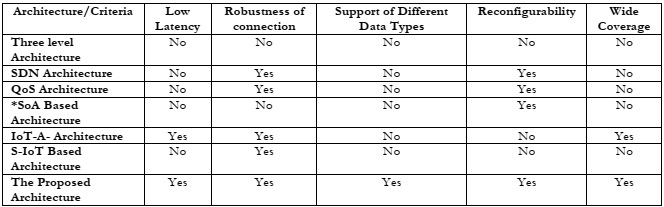
Table 3:A Descriptive Comparison of Different IoT Architecture
Source: Al Harbi, S., Halabi, T., & Bellaiche, M. (2020, December). Fog computing
security assessment for device authentication in the Internet of things.

Figure 11:5G IoT Architecture
Source: Rahimi, H., Zibaeenejad, A., & Safavi, A. A. (2018, November). A novel IoT
architecture based on 5G-IoT and next-generation technologies.
Analyzing the quality of smart devices in D2D communication involves
assessing
various performance metrics to ensure reliable and efficient communication. Here are some
algorithms and techniques commonly used for this purpose:
Signal Strength and Link Quality Analysis:
Received Signal Strength Indicator (RSSI):
Measures the strength of the received signal
to estimate the distance between devices.Signal-to-Noise Ratio (SNR): Compares the strength of the received signal to the background
noise, indicating the quality of the communication link.
Bit Error Rate (BER): Calculates the ratio of incorrectly received bits to the total transmitted
bits, providing insight into data transmission accuracy.
Packet Loss and Latency Analysis:
Round-Trip Time (RTT): Measures the time taken for a packet to travel from the
source device to the destination device and back. Elevated RTT indicates latency in the
communication. Packet Loss Rate: Measures the proportion of packets lost during
transmission, highlighting communication reliability issues. Jitter Analysis: Assesses the
variability in packet arrival times, which can impact the consistency of communication.
Network Topology and Routing Algorithms:
Distance Vector Routing: Calculates routes based on the distances between
devices,
helping to optimize communication paths. Link-State Routing: Uses comprehensive
knowledge of the network's current state to determine the best paths for communication.
Dynamic Source Routing (DSR): Establishes routes based on information collected from
previous communications between devices.
Congestion Control and Load Balancing:
Quality of Service (QoS) Algorithms: Prioritizes specific traffic types to
ensure reliable
and timely delivery of critical data. Load Balancing: Distributes communication traffic evenly
across available paths, preventing network congestion and enhancing overall performance.
Energy Efficiency Algorithms:
Sleep Scheduling: Determines when devices can enter sleep mode to conserve energy
while maintaining communication capabilities. Power Control: Adjusts transmission power
levels based on the proximity of devices, minimizing energy consumption.
Channel Allocation Algorithms:
Frequency Hopping Spread Spectrum (FHSS): Distributes communication across multiple
frequency channels to reduce interference and improve reliability. Time Division Multiple
Access (TDMA): Divides communication time into time slots for different devices,
minimizing collisions and improving efficiency.
Security and Authentication:
Public Key Infrastructure (PKI): Uses asymmetric cryptography for secure device
identification and communication. Authentication Protocols: Verify the identity of devices
before allowing communication to prevent unauthorized access.
Machine Learning Algorithms:
Anomaly Detection:
Uses machine learning models to identify unusual patterns in
communication behavior, indicating potential issues or threats. Predictive Analytics: Utilizes
historical data to predict communication quality and identify potential future problems. These
algorithms and techniques collectively help in assessing the quality of D2D communication in
smart devices, ensuring smooth and reliable operation in various applications such as the IoT
and smart homes.
D2D Performance:
Applying D2D technology to 5G can enhance signal/data transfer efficiency in a
number of ways. A device cannot communicate using the base station if the Signal Interference
plus Noise Ratio (SINR) is low and the device is outside the range of the base station.
However, this can be resolved by relaying signals from devices that still receive signals from
the base station, in accordance with the D2D working principle.
Bluetooth BLE:
Bluetooth BLE works at the speed of 1Mbps within a range of 50m having standard
IEEE 802.15.1. The actual power consumption of Bluetooth is 10 mW. Bluetooth works on the spectrum of 2.4GHz having network type PAN
(Personal Area Network). To compute
the time required for sending a specific number of client information bytes, we need to
consider the discontinuity and the bundle overhead added by every convention layer, without
retransmission, this time can be determined as:
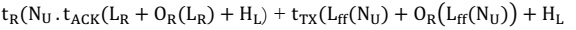


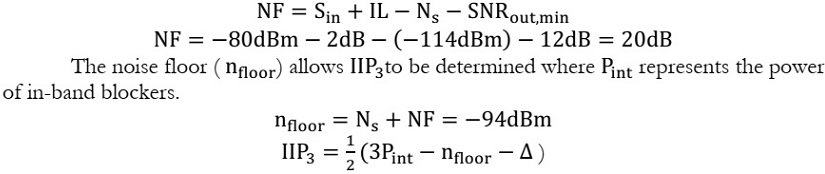
Zigbee Network Performance Metrics:
Zigbee Application within scenario simulation times and is computed as:

The total packet sent, the time the last packet was sent, and the time the first packet
was sent are denoted as Tps, Tlps, and Tfps respectively.
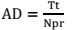
Where the average end-to-end delay, the total transmission delay of all received
packets, and the number of packets received are denoted as AD, Tt, and Npr.
Tdp = Tpr − Tpt
Where the transmission delay of a packet occurs, the time packet received at the
destination node and the time packet transmitted at the source node is referred to as the time
packet received at the destination node Tdp, Tpr, and Tpt respectively.
\
RFID
The bit error probability (Pe) for noncoherent ASK demodulation is:
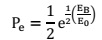
For a UHF backscatter device, the maximal achievable bit rate is:

This is the same as the noise figure which is typically specified by dB value from
equation 2.3 and equation (2) the Signal Noise Ratio can be written as :

The capacity of the channel is the tight upper limit of the rate at which data can be
transmitted over a communication channel efficiently.
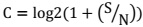
Oxygen, water vapor, fog, cloud and rain attenuation have a major impact on radio
communication that operates in a millimeter frequency range. As a result, the power of the
channel decreases. Compute the Signal to Interference Plus Noise Ratio between the
transmitter and the receiver. Where the transmitter is denoted by i and the reviever is denoted
by j.
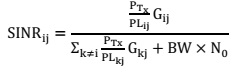
Conclusion
D2D communication
is an exceptionally basic piece of IoT. Numerous industries and
standardization bodies have shown extensive interest in the adoption of the D2D approach
by wireless organizations. The D2D approach makes it easier to operate without the need for
centralizing control to enhance the efficiency of wireless organizations with traffic offloading.
Among networking devices, there is a wide range of IoT development applications. It is
projected that this emerging technology will aid cellular networks in the next decade in
reducing transmission time delays, conserving energy, and extending range. The Internet of
Things (IoT) is introduced and referred to as a means of data exchange between D2D contact
clusters that are simultaneously connected and fall under the jurisdiction of the cell
organization. Architecture is provided with a brief overview of the D2D communication
regarding its use cases. D2D organizing has already demonstrated its pivotal role in achieving
the effective objectives of 5G wireless organizations. Initial systems that utilize D2D
communication are just now beginning to emerge. To enhance IoT, more developments and
industry standards are being established.
Recommendations:
✓ In order to create high-performance IoT applications, it is necessary to abide by the laws
on data gravity.
✓ The frequency range should be underused without impacting the natural environment.
✓ With minimum deviations, location-based D2D resource allocation improvement is still
needed.
✓ To reduce the transfer between base stations and also to enhance congestion
management techniques, a new method is required.
✓ By using uplink and downlink radio networks, Fractional Frequency Reuse (FFR) with
resource allocation under SC-FDMA can be further expanded. This can also be taken
into account under Multicells by the use of link selection techniques.
Author's Contribution:All authors have Contributed
equally
Project details:Nil
Conflict of Interest: The authors declare no conflict of interest in
publishing
this manuscript in IJIST.
Reference
[1] R. P. Pradhan, G. Mallik, and T. P. Bagchi,
Information communication technology (ICT)
infrastructure and economic growth: A causality evinced by cross-country panel data, vol. 30,
no. 1. Elsevier Ltd, 2018. doi: 10.1016/j.iimb.2018.01.001.
[2] M. S. M. Gismalla et al., “Survey on D2D (D2D) Communication for 5GB/6G Networks:
Concept, Applications, Challenges, and Future Directions,” IEEE Access, vol. 10, no. Vlc,
pp. 30792–30821, 2022, doi: 10.1109/ACCESS.2022.3160215.
[3] G. Geraci et al., “What Will the Future of UAV Cellular Communications Be? A Flight from
5G to 6G,” IEEE Commun. Surv. Tutorials, vol. 24, no. 3, pp. 1304–1335, 2022, doi:
10.1109/COMST.2022.3171135.
[4] M. Ikram, K. Sultan, M. F. Lateef, and A. S. M. Alqadami, “A Road towards 6G
Communication—A Review of 5G Antennas, Arrays, and Wearable Devices,” Electron., vol.
11, no. 1, 2022, doi: 10.3390/electronics11010169.
[5] Q. V. Khanh, N. V. Hoai, L. D. Manh, A. N. Le, and G. Jeon, “Wireless Communication
Technologies for IoT in 5G: Vision, Applications, and Challenges,” Wirel. Commun. Mob.
Comput., vol. 2022, 2022, doi: 10.1155/2022/3229294.
[6] P. Sun, Q., Lin, K., Si, C., Xu, Y., Li, S., & Gope, “A secure and anonymous communicate
scheme over the internet of things. ACM Transactions on Sensor Networks (TOSN),” vol.
18, no. 3, pp. 1–21, 2022.
[7] R. Lee, W., & Schober, “Deep learning-based resource allocation for D2Dcommunication.
IEEE Transactions on Wireless Communications,” vol. 21, no. 7, pp. 5235–5250, 2022.
[8] P. E. Chowdhury, R. R., Idris, A. C., & Abas, “A Deep Learning Approach for Classifying
Network Connected IoT Devices Using Communication Traffic Characteristics. Journal of
Network and Systems Management,” vol. 31, no. 1, 2023.
[9] H. P. Saravanan, V., Sreelatha, P., Atyam, N. R., Madiajagan, M., Saravanan, D., & Sultana,
“Design of deep learning model for radio resource allocation in 5G for massive iot device.
Sustainable Energy Technologies and Assessments,” vol. 56, 2023.
[10] D. C. Suman, T., Kaliappan, S., Natrayan, L., & Dobhal, “IoT based Social Device Network
with Cloud Computing Architecture. In 2023 Second International Conference on Electronics
and Renewable Systems (ICEARS),” pp. 502–505, 2023.
[11] T. Barik, D., Sanyal, J., & Samanta, “Denial-of-Service Attack Mitigation in Multi-hop 5G
D2D Wireless Communication Networks Employing Double Auction Game. Journal of
Network and Systems Management,” vol. 31, no. 1, 2023.
[12] A. Arab, S., Ashrafzadeh, H., & Alidadi, “Internet of Things: Communication Technologies,
Features and Challenges,” vol. 6, no. 2, 2018.
[13] S. Zeadally, F. Siddiqui, and Z. Baig, “25 Years of Bluetooth Technology,” Futur. Internet,
vol. 11, no. 9, 2019, doi: 10.3390/fi11090194.
[14] S. Zhang, “An Overview of Network Slicing for 5G,” IEEE Wirel. Commun., vol. 26, no. 3,
pp. 111–117, 2019, doi: 10.1109/MWC.2019.1800234.
[15] M. O. Mwashita, W., & Odhiambo, “Interference management techniques for
D2Dcommunications. In Predictive Intelligence Using Big Data and the Internet of Things .
IGI Global,” pp. 219–245, 2019.
[16] U. N. Kar and D. K. Sanyal, “A Critical Review of 3GPP Standardization of
D2DCommunication in Cellular Networks,” SN Comput. Sci., vol. 1, no. 1, pp. 1–18, 2020,
doi: 10.1007/s42979-019-0045-5.
[17] R. Barua, S., & Braun, “Mobility management of D2D communication for the 5G cellular
network system: a study and result. In 2017 17th International Symposium on
Communications and Information Technologies (ISCIT),” pp. 1–6, 2017.
[18] C. Huang and Y. Lv, “An Internet of Things system based on D2Dcommunication technology
and radio-frequency identification,” Int. J. Online Eng., vol. 14, no. 10, pp. 210–218, 2018,
doi: 10.3991/ijoe.v14i10.9302.
[19] A. M. Lonzetta, P. Cope, J. Campbell, B. J. Mohd, and T. Hayajneh, “Security vulnerabilities
in bluetooth technology as used in IoT,” J. Sens. Actuator Networks, vol. 7, no. 3, pp. 1–26,
2018, doi: 10.3390/jsan7030028.
[20] H. Zemrane, Y. Baddi, and A. Hasbi, “Comparison between IOT protocols,” pp. 1–6, 2018,
doi: 10.1145/3289402.3289522.
[21] F. Nisha, “Implementation of RFID technology at defence science library, DESIDOC: A case
study,” DESIDOC J. Libr. Inf. Technol., vol. 38, no. 1, pp. 27–33, 2018, doi:
10.14429/djlit.38.1.12351.
[22] P. Gandotra, R. Kumar Jha, and S. Jain, “A survey on D2D communication: Architecture and
security issues,” J. Netw. Comput. Appl., vol. 78, pp. 9–29, 2017, doi:10.1016/j.jnca.2016.11.002.
[23] J. Saqlain, “IoT and 5G : History evolution and its architecture their compatibility and future.,”
p. 72, 2018, [Online]. Available: https://www.theseus.fi/handle/10024/143210
[24] E. G. Larsson, “Massive MIMO for 5G: Overview and the road ahead,” pp. 1–1, 2017, doi:
10.1109/ciss.2017.7926182.
[25] M. H. Alsharif and R. Nordin, “Evolution towards fifth generation (5G) wireless networks:
Current trends and challenges in the deployment of millimetre wave, massive MIMO, and
small cells,” Telecommun. Syst., vol. 64, no. 4, pp. 617–637, 2017, doi: 10.1007/s11235-016-
0195-x.
[26] B. Zhou, A. Liu, and V. Lau, “Successive Localization and Beamforming in 5G mmWave
MIMO Communication Systems,” IEEE Trans. Signal Process., vol. 67, no. 6, pp. 1620–1635,
2019, doi: 10.1109/TSP.2019.2894789.
[27] W. Xiang, K. Zheng, and X. S. Shen, 5G mobile communications. 2016. doi: 10.1007/978-3-
319-34208-5.
[28] S. Gokhale, P., Bhat, O., & Bhat, “Introduction to IOT. International Advanced Research
Journal in Science, Engineering and Technology (IARJ SET),” vol. 5, no. 1, 2018.
[29] B. N. Silva, M. Khan, and K. Han, “Internet of Things: A Comprehensive Review of Enabling
Technologies, Architecture, and Challenges,” IETE Tech. Rev. (Institution Electron.
Telecommun. Eng. India), vol. 35, no. 2, pp. 205–220, 2018, doi:
10.1080/02564602.2016.1276416.
[30] P. Sethi and S. R. Sarangi, “Internet of Things: Architectures, Protocols, and Applications,” J.
Electr. Comput. Eng., vol. 2017, 2017, doi: 10.1155/2017/9324035.
[31] M. Stanley, Y. Huang, H. Wang, H. Zhou, A. Alieldin, and S. Joseph, “A novel mm-Wave
phased array antenna with 360° coverage for 5G smartphone applications,” 2017 10th UKEurope-China Work. Millimetre Waves Terahertz Technol.
UCMMT 2017, pp. 22–24, 2017,
doi: 10.1109/UCMMT.2017.8068482.
[32] M. Conti, A. Dehghantanha, K. Franke, and S. Watson, “Internet of Things security and
forensics: Challenges and opportunities,” Futur. Gener. Comput. Syst., vol. 78, pp. 544–546,
2018, doi: 10.1016/j.future.2017.07.060.
[33] H. Rahimi, A. Zibaeenejad, and A. A. Safavi, “A Novel IoT Architecture based on 5G-IoT
and Next Generation Technologies,” 2018 IEEE 9th Annu. Inf. Technol. Electron. Mob.
Commun. Conf. IEMCON 2018, pp. 81–88, 2019, doi: 10.1109/IEMCON.2018.8614777.
[34] M. A. Moridi, Y. Kawamura, M. Sharifzadeh, E. K. Chanda, M. Wagner, and H. Okawa,
“Performance analysis of ZigBee network topologies for underground space monitoring and
communication systems,” Tunn. Undergr. Sp. Technol., vol. 71, no. July 2017, pp. 201–209,
2018, doi: 10.1016/j.tust.2017.08.018.
[35] H. Landaluce, L. Arjona, A. Perallos, L. Bengtsson, and N. Cmiljanic, “A high throughput
anticollision protocol to decrease the energy consumption in a passive RFID system,” Wirel.
Commun. Mob. Comput., vol. 2017, 2017, doi: 10.1155/2017/2135182.
[36] D. Nandi and A. Maitra, “Study of rain attenuation effects for 5G Mm-wave cellular
communication in tropical location,” IET Microwaves, Antennas Propag., vol. 12, no. 9, pp.
1504–1507, 2018, doi: 10.1049/iet-map.2017.1029.