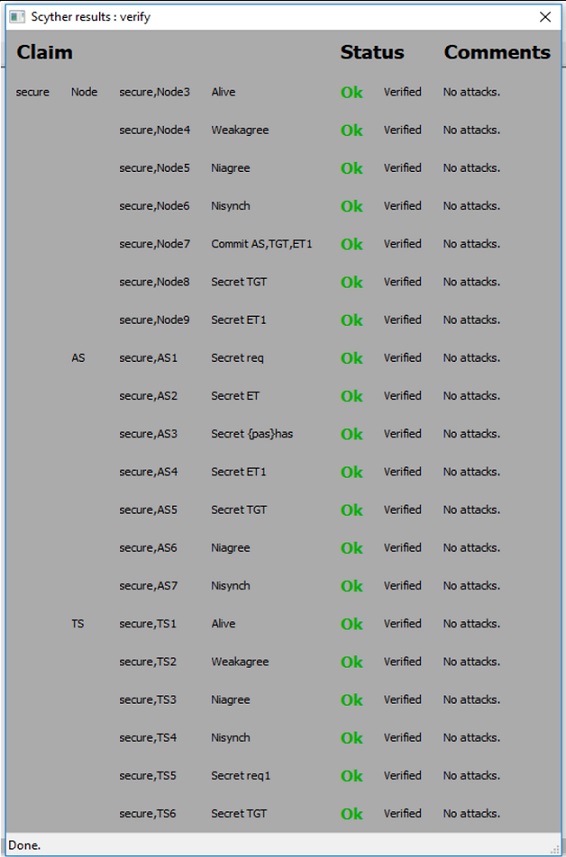
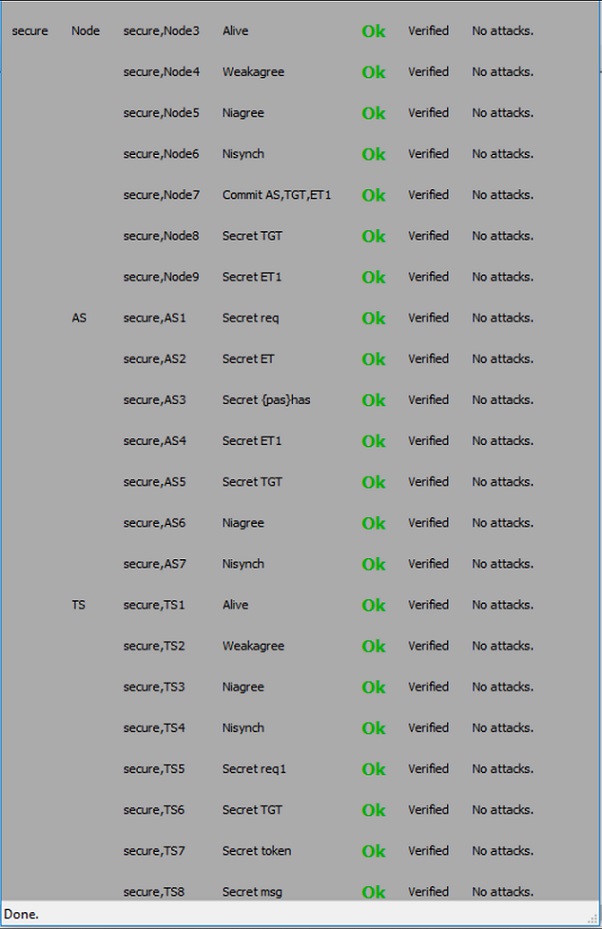
In this section, we discuss the results that we obtained from the testing environments. Analysis of the proposed scheme with its attributes is also discussed.
• The attacker has complete or partial control over the network.
• The attacker is resourceful, as detailed in the Dolev-Yao intruder model [35], and can learn, deflect, and generate messages.
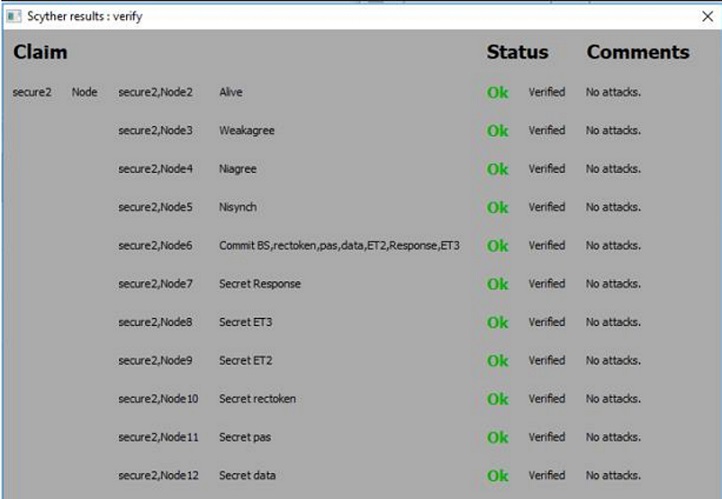
We have defined a protocol named "Example Protocol" with two roles, "I" and "R," by naming them after the protocol name in brackets. Note that we haven't yet defined the behavior of these roles. Within the curly brackets, their behaviors are defined when we need to use these roles later in the protocol implementation.
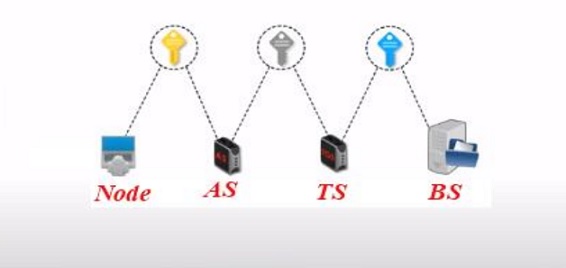
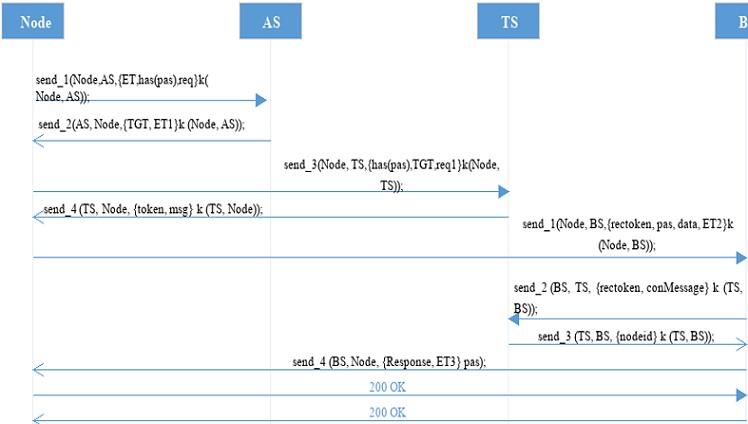
Because the proposed scheme consists of four components that’s why here in the input files four roles are created i.e. Node, AS, TS, and BS.
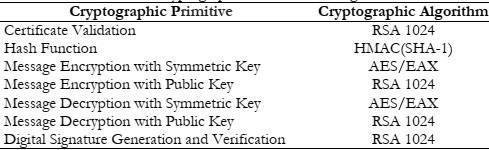
Because authors of the schemes with which comparisons are performed for efficiency also use the same benchmarks for performance evaluation. Because for accurate results the same benchmark is very important. In this study cryptographic algorithm for performing each cryptographic primitive in the proposed scheme as well as the crypto algorithm and primitives that are used in the comparison, schemes are presented in Table 1.
Digital Signature Generation and Verification RSA 1024
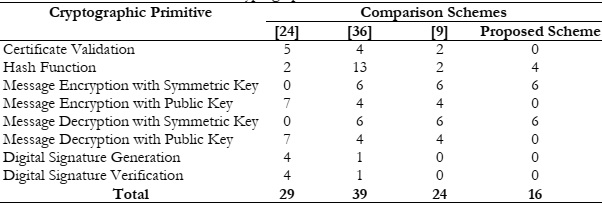
We can calculate how many times each cryptographic primitive is done in total by evaluating the authentication schemes provided in [9][24] and [36] and in this study proposed scheme, considering the benchmarks from [37], as presented in Table 2. For completing the authentication process the proposed schemes in [9][24] and [36] use twenty-four, twenty-nine, and thirty-nine cryptographic primitives respectively.
However, in the proposed scheme only eighteen primitives are required to complete the authentication process which means approximately 25% less computation and calculation cost.
Next, the time required to complete the authentication process is examined, also known as authentication delay. It is divided into two parts, the transmission time and the processing time. The processing time is the most important component because it reflects the time required to perform cryptographic primitives. The transmission time is defined as “The time required to send the message between the communication nodes. “For numerical results, it is assumed that in the proposed scheme and all the comparison schemes have the same transmission time so for calculation of the authentication delay transmission time was omitted.
According to [37], the time for message encryption with the public key is 0.08ms, the time for message encryption with a symmetric key is 1.8µs, for the message decryption with a public key time is 1.46ms, the message decryption with symmetric key takes 1.8µs, the hashing time using HMAC (SHA-1) is 0.509µs, the time required for signature generation is 1.48ms and the verification time using RSA 1024 is 0.07ms.
In [24] the authentication time was 17.3ms, the authentication time of the proposed scheme in [36] was 8.02ms and in [9] it was 7.23ms respectively. And the authentication time in the proposed scheme is approximately 27.236 µs or 0.027236ms. These results, it is proof that the proposed scheme is approximately 84%, 66%, and 62% faster in comparison to that in [24] [36] and [9], respectively.
From the result, it is clear that the proposed approach cuts down the authentication time. Moreover, symmetric-key cryptography is utilized to encrypt and decrypt the majority of the messages transmitted between communication parties. Symmetric key cryptography has less memory use less power utilization and less memory occupation. Hence the proposed scheme is optimized and less complicated than that of comparison schemes. From the future perspective, due to the importance of machine learning (ML) in different fields and network advancement [38][39][40][41][42][43][44] we have planned to work with ML models.
[1]H. N. Dai, R. C. W. Wong, H. Wang, Z. Zheng, and A. V. Vasilakos, “Big Data Analytics for Large-scale Wireless Networks,” ACM Comput. Surv., vol. 52, no. 5, Sep. 2019, doi: 10.1145/3337065.
[2]S. Abidin, V. R. Vadi, and A. Rana, “On Confidentiality, Integrity, Authenticity, and Freshness (CIAF) in WSN,” Adv. Intell. Syst. Comput., vol. 1158, pp. 87–97, 2021, doi: 10.1007/978-981-15-4409-5_8/COVER.
[3]C. Biswas, U. Das Gupta, and M. M. Haque, “An Efficient Algorithm for Confidentiality, Integrity and Authentication Using Hybrid Cryptography and Steganography,” 2nd Int. Conf. Electr. Comput. Commun. Eng. ECCE 2019, Apr. 2019, doi: 10.1109/ECACE.2019.8679136.
[4]J. Cui, L. Shao, H. Zhong, Y. Xu, and L. Liu, “Data aggregation with end-to-end confidentiality and integrity for large-scale wireless sensor networks,” Peer-to-Peer Netw. Appl., vol. 11, no. 5, pp. 1022–1037, Sep. 2018, doi: 10.1007/S12083-017-0581-5/TABLES/7.
[5]J. Zhao and G. Cao, “Robust topology control in multi-hop cognitive radio networks,” IEEE Trans. Mob. Comput., vol. 13, no. 11, pp. 2634–2647, Nov. 2014, doi: 10.1109/TMC.2014.2312715.
[6] A. J. Olaode, “AVAILABILITY OF INFORMATION AND ITS SECURITY MEASURES,” СОВРЕМЕННЫЕ ТЕХНОЛОГИИ АКТУАЛЬНЫЕ ВОПРОСЫ, ДОСТИЖЕНИЯ И ИННОВАЦИИ, pp. 37–42, 2019.
[7] M. Khasawneh, I. Kajman, R. Alkhudaidy, and A. Althubyani, “A Survey on Wi-Fi Protocols: WPA and WPA2,” Commun. Comput. Inf. Sci., vol. 420 CCIS, pp. 496–511, 2014, doi: 10.1007/978-3-642-54525-2_44/COVER.
[8] H. Z. U. K. and H. Zahid, “Comparative study of authentication techniques,” Int. J. Video Image Process. Netw. Secur. IJVIPNS, vol. 10, no. 4, pp. 9–13, 2010.
[9] M. Khasawneh and A. Agarwal, “A Secure and Efficient Authentication Mechanism Applied to Cognitive Radio Networks,” IEEE Access, vol. 5, pp. 15597–15608, Jul. 2017, doi: 10.1109/ACCESS.2017.2723322.
[10] A. Al Abdulwahid, N. Clarke, I. Stengel, S. Furnell, and C. Reich, “Continuous and transparent multimodal authentication: reviewing the state of the art,” Cluster Comput., vol. 19, no. 1, pp. 455–474, Mar. 2016, doi: 10.1007/S10586-015-0510-4/METRICS.
[11] A. H. Moon, U. Iqbal, and G. M. Bhat, “Implementation of Node Authentication for WSN Using Hash Chains,” Procedia Comput. Sci., vol. 89, pp. 90–98, Jan. 2016, doi: 10.1016/J.PROCS.2016.06.013.
[12] and W. C. L. Zhou, X. Li, K.-H. Yeh, C. Su, “Lightweight IoT-based authentication scheme in cloud computing circumstance,” Futur. Gener. Comput. Syst, vol. 91, pp. 244–251, 2019.
[13] N. A. M. Risalat, M. T. Hasan, M. S. Hossain, and M. M. Rahman, “Advanced real time RFID mutual authentication protocol using dynamically updated secret value through encryption and decryption process,” ECCE 2017 - Int. Conf. Electr. Comput. Commun. Eng., pp. 788–793, Apr. 2017, doi: 10.1109/ECACE.2017.7913010.
[14] A. Ometov, S. Bezzateev, N. Mäkitalo, S. Andreev, T. Mikkonen, and Y. Koucheryavy, “Multi-Factor Authentication: A Survey,” Cryptogr. 2018, Vol. 2, Page 1, vol. 2, no. 1, p. 1, Jan. 2018, doi: 10.3390/CRYPTOGRAPHY2010001.
[15] Z. A. Alizai, N. F. Tareen, and I. Jadoon, “Improved IoT Device Authentication Scheme Using Device Capability and Digital Signatures,” ICAEM 2018 - 2018 Int. Conf. Appl. Eng. Math. Proc., pp. 115–119, Nov. 2018, doi: 10.1109/ICAEM.2018.8536261.
[16] D. Wang and P. Wang, “Two Birds with One Stone: Two-Factor Authentication with Security beyond Conventional Bound,” IEEE Trans. Dependable Secur. Comput., vol. 15, no. 4, pp. 708–722, Jul. 2018, doi: 10.1109/TDSC.2016.2605087.
[17] Z. L. et Al., “FBS-Radar: Uncovering Fake Base Stations at Scale in the Wild,” 2017.
[18] M. Pannu, R. Bird, B. Gill, and K. Patel, “Investigating vulnerabilities in GSM security,” 2015 Int. Conf. Work. Comput. Commun. IEMCON 2015, Dec. 2015, doi: 10.1109/IEMCON.2015.7344480.
[19] O. Delgado-Mohatar, A. Fúster-Sabater, and J. M. Sierra, “A light-weight authentication scheme for wireless sensor networks,” Ad Hoc Networks, vol. 9, no. 5, pp. 727–735, Jul. 2011, doi: 10.1016/J.ADHOC.2010.08.020.
[20] X. Sun, S. Men, C. Zhao, and Z. Zhou, “A security authentication scheme in machine-to-machine home network service,” Secur. Commun. Networks, vol. 8, no. 16, pp. 2678–2686, Nov. 2015, doi: 10.1002/SEC.551.
[21] K. Garrett, S. R. Talluri, and S. Roy, “On vulnerability analysis of several password authentication protocols,” Innov. Syst. Softw. Eng., vol. 11, no. 3, pp. 167–176, Sep. 2015, doi: 10.1007/S11334-015-0250-X/METRICS.
[22] H. J. Mun, S. Hong, and J. Shin, “A novel secure and efficient hash function with extra padding against rainbow table attacks,” Cluster Comput., vol. 21, no. 1, pp. 1161–1173, Mar. 2018, doi: 10.1007/S10586-017-0886-4/METRICS.
[23] S. Parvin and F. K. Hussain, “Digital signature-based secure communication in cognitive radio networks,” Proc. - 2011 Int. Conf. Broadband Wirel. Comput. Commun. Appl. BWCCA 2011, pp. 230–235, 2011, doi: 10.1109/BWCCA.2011.95.
[24] S. Parvin, F. K. Hussain, and O. K. Hussain, “Digital signature-based authentication framework in cognitive radio networks,” ACM Int. Conf. Proceeding Ser., pp. 136–142, 2012, doi: 10.1145/2428955.2428985.
[25] A. A.-M. and M. C. Morogan, “Identity-based authentication and access control in wireless sensor networks,” Int. J. Comput. Appl, vol. 41, no. 13, 2012.
[26] V. J. Rathod, N. C. Iyer, and S. M. Meena, “A survey on fingerprint biometric recognition system,” Proc. 2015 Int. Conf. Green Comput. Internet Things, ICGCIoT 2015, pp. 323–326, Jan. 2016, doi: 10.1109/ICGCIOT.2015.7380482.
[27] A. El-Sayed, “Multi-biometric systems: a state of the art survey and research irections,” IJACSA) Int. J. Adv. Comput. Sci. Appl, vol. 6, 2015.
[28] Q. Jiang, J. Ma, G. Li, and X. Li, “Improvement of robust smart-card-based password authentication scheme,” Int. J. Commun. Syst., vol. 28, no. 2, pp. 383–393, Jan. 2015, doi: 10.1002/DAC.2644.
[29] W. M. AlOmari and H. Abusaimeh, “Modified USB Security Token for User Authentication,” Comput. Inf. Sci., vol. 8, no. 3, p. p51, Aug. 2015, doi: 10.5539/CIS.V8N3P51.
[30] A. X. Liu and L. R. A. Bailey, “PAP: A privacy and authentication protocol for passive RFID tags,” Comput. Commun., vol. 32, no. 7–10, pp. 1194–1199, May 2009, doi: 10.1016/J.COMCOM.2009.03.006.
[31] P. Gope, J. Lee, and T. Q. S. Quek, “Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions,” IEEE Trans. Inf. Forensics Secur., vol. 13, no. 11, pp. 2831–2843, Nov. 2018, doi: 10.1109/TIFS.2018.2832849.
[32] and A. P. H. Yang, V. Oleshchuk, “Verifying group authentication protocols by Scyther,” J. Wirel. Mob. Networks, Ubiquitous Comput. Dependable Appl, vol. 7, no. 2, pp. 3–19, 2019.
[33] C. Cremers, “Scyther User Manual. 18 February 2014. - References - Scientific Research Publishing,” 2014. https://www.scirp.org/(S(351jmbntvnsjt1aadkozje))/reference/ReferencesPapers.aspx?ReferenceID=1424654 (accessed Sep. 14, 2023).
[34] D. Dolev and A. C. Yao, “On the Security of Public Key Protocols,” IEEE Trans. Inf. Theory, vol. 29, no. 2, pp. 198–208, 1983, doi: 10.1109/TIT.1983.1056650.
[35] I. Cervesato, “The Dolev-Yao intruder is the most powerful attacker,” 16th Annu. Symp. Log. Comput. Sci., vol. 1, 2001.
[36] K. Chatterjee, A. De, and D. Gupta, “A Secure and Efficient Authentication Protocol in Wireless Sensor Network,” Wirel. Pers. Commun., vol. 81, no. 1, pp. 17–37, Mar. 2015, doi: 10.1007/S11277-014-2115-2/METRICS.
[37] “Speed Comparison of Popular Crypto Algorithms.” https://www.cryptopp.com/benchmarks.html (accessed Sep. 14, 2023).
[38] M. T. Ubaid, A. Kiran, M. T. Raja, U. A. Asim, A. Darboe, and M. A. Arshed, “Automatic Helmet Detection using EfficientDet,” 4th Int. Conf. Innov. Comput. ICIC 2021, 2021, doi: 10.1109/ICIC53490.2021.9693093.
[39] M. T. Ubaid, M. Z. Khan, M. Rumaan, M. A. Arshed, M. U. G. Khan, and A. Darboe, “COVID-19 SOP’s Violations Detection in Terms of Face Mask Using Deep Learning,” 4th Int. Conf. Innov. Comput. ICIC 2021, 2021, doi: 10.1109/ICIC53490.2021.9692999.
[40] M. A. Arshed, W. Qureshi, M. U. G. Khan, and M. A. Jabbar, “Symptoms Based Covid-19 Disease Diagnosis Using Machine Learning Approach,” 4th Int. Conf. Innov. Comput. ICIC 2021, 2021, doi: 10.1109/ICIC53490.2021.9692986.
[41] M. Mubeen, M. A. Arshed, and H. A. Rehman, “DeepFireNet - A Light-Weight Neural Network for Fire-Smoke Detection,” Commun. Comput. Inf. Sci., vol. 1616 CCIS, pp. 171–181, 2022, doi: 10.1007/978-3-031-10525-8_14/COVER.
[42] M. A. Arshed, S. Mumtaz, M. S. Liaqat, and I. Haq, “LSTM Based Sentiment Analysis Model to Monitor COVID-19 Emotion LSTM Based Sentiment Analysis Model to Monitor COVID-19 Emotion,” no. May, 2022.
[43] M. Tanveer, A. U. Khan, N. Kumar, and M. M. Hassan, “RAMP-IoD: A Robust Authenticated Key Management Protocol for the Internet of Drones,” IEEE Internet Things J., vol. 9, no. 2, pp. 1339–1353, Jan. 2022, doi: 10.1109/JIOT.2021.3084946.
[44] M. Tanveer, H. Alasmary, N. Kumar, and A. Nayak, “SAAF-IoD: Secure and Anonymous Authentication Framework for the Internet of Drones,” IEEE Trans. Veh. Technol., 2023, doi: 10.1109/TVT.2023.3306813.