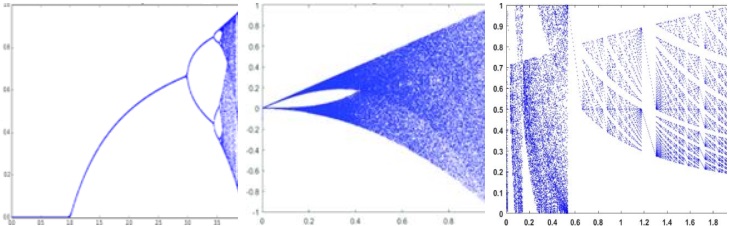
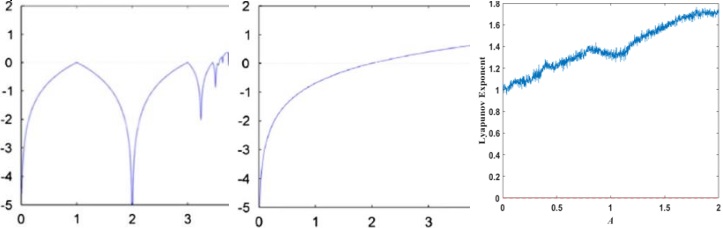
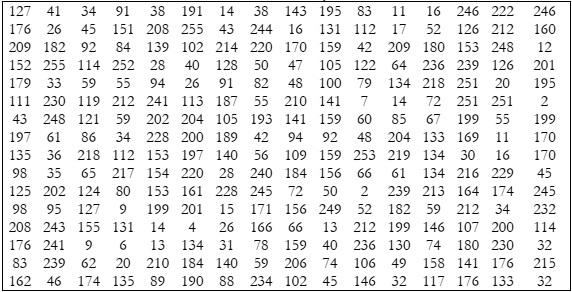
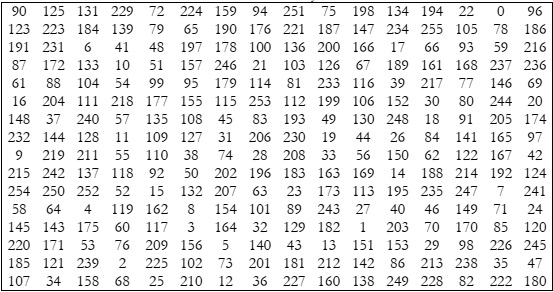
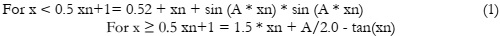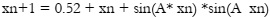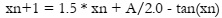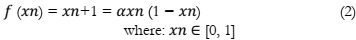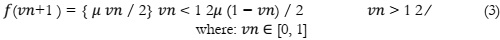A significant data and information research contribution. The development of new S-boxes is central to the
security field. After an S-box is created, it is examined to determine its. The ability to choose how strong it will be
against various attacks. (Differential and linear) [17]. There are tests for an S-Box’s cryptanalytic evaluation. Calculated
using the predetermined criteria, which include:
In general, the capacity to withstand a linear cryptanalysis attack increases with the value of nonlinearity. The
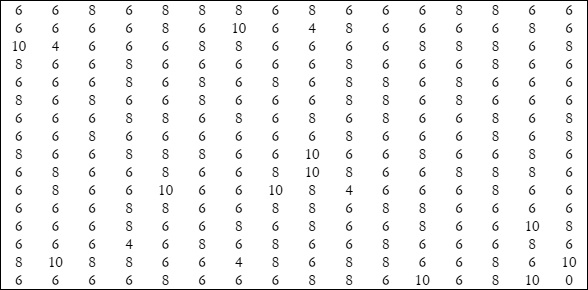
nonlinearity values of the proposed S-Box are 110, 110, 112, 108, 108, 110, 110, and 110, with the smallest value of 108, the
largest value of 112, and an average value of 109.75. The nonlinearity values of the proposed S-Box are mentioned in Table 3.
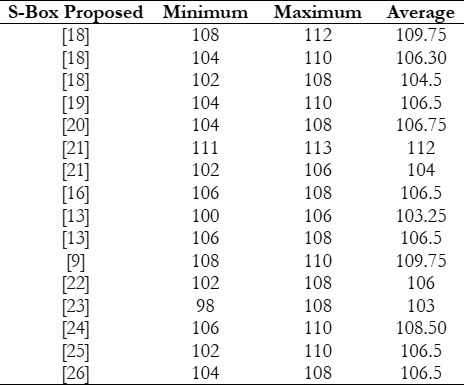
A comparison with nonlinearity values of some recent S-Boxes is shown in Table 4. It is clear that the proposed S-Box has
a higher average value of NL than most of the S-Boxes.
When an input value and its corresponding output value are the same, an S-box fixed point. Fixed Points may induce
flaws and lessen the algorithm's security. One of the causes is that a fixed point may enable an attacker to deduce details
about the input or output values based on the relationship between the fixed point and the known input or output values. To
ensure security, the proposed S-Box was tested against a fixed point criterion. Table 2 shows that there is no fixed point in
the proposed S-Box. There is no opposite fixed point in the proposed S-Box as well [27].
Normally, the statistical correlation between the corresponding output bit patterns and all potential input bit
patterns is taken into account while evaluating the BIC [19]. A statistically balanced distribution of output bit patterns is
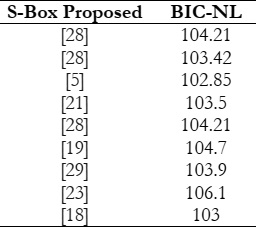
desired in order to guarantee the absence of bias and predictable relationships. Table 5 shows the BIC-NL values of the
proposed S-Box. The average value of BIC-NL is 104.21.
A comparison with average BIC-NL values of some recent S-Boxes is shown in Table 7.
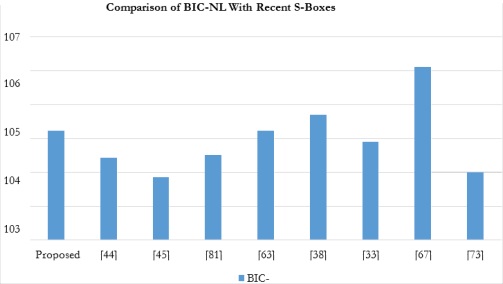
The BIC-NL visualization results of the proposed S-Box with other previously designed S-Boxes are shown in Figure 4. After
comparison, it is clear that the average BIC-NL value of the proposed S-Box 104.21 is higher than most of the other S-Boxes
it is compared with.
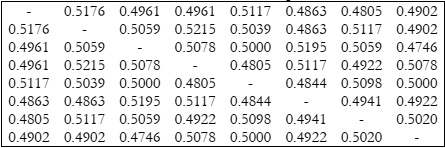
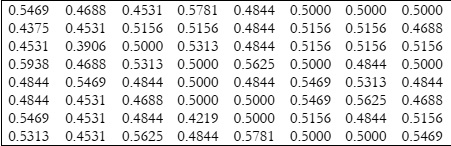
The strict avalanche criteria (SAC) describes how output behaves, and SAC is satisfied only when anyone complements a
single input bit, changing half of the output bits [20]. A single change to the input value should toggle half of the output
bit in order to satisfy SAC. As the substitution permutation recurrence advances, a single modification in the input bit will
result in an avalanche change. Each of the output bits in the S-Box should alter with a probability of 0.5 if a single input
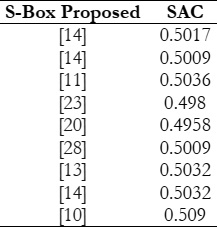
bit changes. The average SAC value of the proposed S-Box is 0.5017.
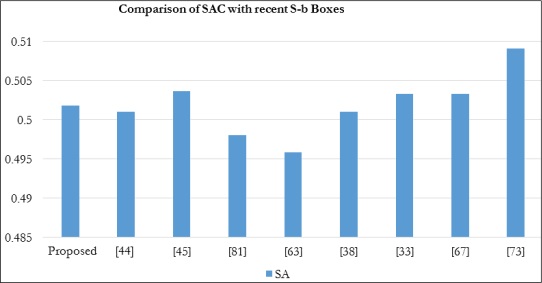
A comparison with average SAC values of some recent S-Boxes is shown in Table 9.
The SAC visualization results of the proposed S-Box with other previously designed S-Boxes are shown in Figure 5. After
comparison, it is clear that the average SAC value of the proposed S-Box which is 0.5017 is more accurate than most of the
other S-Boxes it is compared with [29].
When the input and output of an S-box are linearly connected, the correlation between the input and output bits is
measured by the linear approximation probability [21]. A numeric value between 0 and 0.5 is commonly used to denote the
linear approximation probability. Significant linear approximation, or a score approaching 0.5, denotes a significant
correlation between the linear relationship and the S-box behavior. The correlation is low if the value is close to 0, which
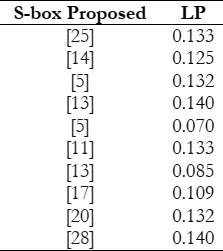
denotes a poor linear approximation [24]. The average LP of the proposed S-Box is 0.1329. A comparison with average LP values
of some recent S-Boxes is shown in Table 10.
A numeric value between 0 and 1 is commonly used to denote the differential approximation probability. The input and
output differences have a strong association when their values are close to 1, which could point to a weakness in the linear
approximation [28]. A correlation that is weak and close to 0 suggests nonlinear behavior and greater susceptibility to
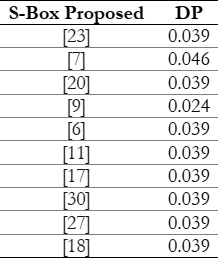
differential cryptanalysis. The average DU value is 0.0391. Table 11 shows the differential uniformity of the proposed S-Box
[22].
A comparison with average DP values of some recent S-Boxes is shown in Table 12.
On a machine running Windows 7 with 6GB of Memory and a 2.24GHz Intel Core i5 Processor, to assess the computational
efficiency of the suggested S-box approach, a Visual C simulation was done [30]. The suggested method’s calculation
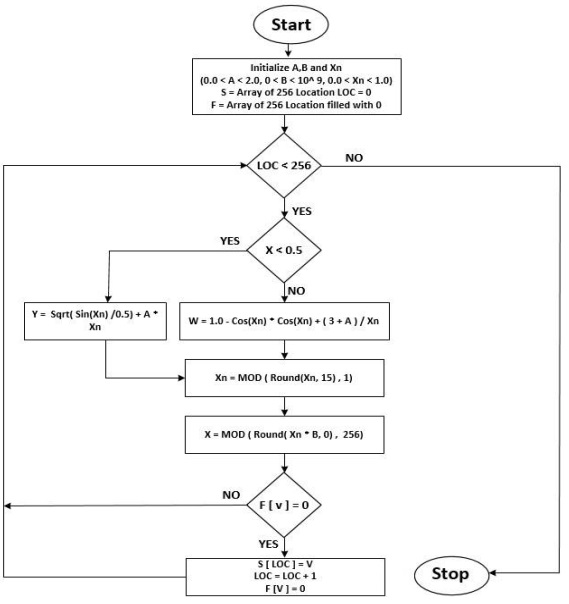
efficiency was observed for both the initial and final S-boxes. A clever and heuristic approach for calculating the initial
S- S-cryptographic box’s strength is necessary for the S-creation. box’s 100000 distinct beginning S-boxes were produced in
order to assess their time complexity and the time needed to the average time complexity of these initial and final S-box
constructions is measured in Table 10. Table 10 demonstrates how highly motivating the preliminary S-building box’s time is.
However, the proposed solution requires a little more time to build an S-box.
[1]
S. Xu, Y. Wang, Y. Guo, and C. Wang, “A novel chaos-based image encryption scheme,”
Proc. - 2009 Int. Conf. Inf. Eng. Comput. Sci. ICIECS 2009, 2009, doi:
10.1109/ICIECS.2009.5365275.
[2] S. Bukhari, A. Yousaf, S. Niazi, and M. R. Anjum, “A Novel Technique for the Generation and Application
of Substitution Boxes (s-box) for the Image Encryption,” Nucl., vol. 55, no. 4, pp. 219–225, 2018, Accessed: Dec. 09, 2023.
[Online]. Available: http://thenucleuspak.org.pk/index.php/Nucleus/article/view/229
[3] M. Ge and R. Ye, “A novel image encryption scheme based on 3D bit matrix and chaotic map with Markov
properties,” Egypt. Informatics J., vol. 20, no. 1, pp. 45–54, Mar. 2019, doi: 10.1016/J.EIJ.2018.10.001.
[4] I. Hussain, A. Anees, T. A. Al-Maadeed, and M. T. Mustafa, “Construction of S-Box Based on Chaotic Map
and Algebraic Structures,” Symmetry 2019, Vol. 11, Page 351, vol. 11, no. 3, p. 351, Mar. 2019, doi: 10.3390/SYM11030351.
[5] W. Yan and Q. Ding, “A Novel S-Box Dynamic Design Based on Nonlinear-Transform of 1D Chaotic Maps,”
Electron. 2021, Vol. 10, Page 1313, vol. 10, no. 11, p. 1313, May 2021, doi: 10.3390/ELECTRONICS10111313.
[6] S. Shaukat Jamal, D. Shah, A. Deajim, and T. Shah, “The Effect of the Primitive Irreducible Polynomial on
the Quality of Cryptographic Properties of Block Ciphers,” Secur. Commun. Networks, vol. 2020, 2020, doi:
10.1155/2020/8883884.
[7] X. Zhang et al., “Generation and Evaluation of a New Time-Dependent Dynamic S-Box Algorithm for AES Block
Cipher Cryptosystems,” IOP Conf. Ser. Mater. Sci. Eng., vol. 978, no. 1, p. 012042, Nov. 2020, doi:
10.1088/1757-899X/978/1/012042.
[8] V. Kumar and A. Girdhar, “A 2D logistic map and Lorenz-Rossler chaotic system based RGB image encryption
approach,” Multimed. Tools Appl., vol. 80, no. 3, pp. 3749–3773, Jan. 2021, doi: 10.1007/S11042-020-09854-X/METRICS.
[9] X. yuan Wang and Q. Yu, “A block encryption algorithm based on dynamic sequences of multiple chaotic
systems,” Commun. Nonlinear Sci. Numer. Simul., vol. 14, no. 2, pp. 574–581, Feb. 2009, doi: 10.1016/J.CNSNS.2007.10.011.
[10] S. Hanis and R. Amutha, “A fast double-keyed authenticated image encryption scheme using an improved
chaotic map and a butterfly-like structure,” Nonlinear Dyn., vol. 95, no. 1, pp. 421–432, Jan. 2019, doi:
10.1007/S11071-018-4573-7/METRICS.
[11] H. Gao, Y. Zhang, S. Liang, and D. Li, “A new chaotic algorithm for image encryption,” Chaos, Solitons &
Fractals, vol. 29, no. 2, pp. 393–399, Jul. 2006, doi: 10.1016/J.CHAOS.2005.08.110.
[12] X. Wang and D. Chen, “A parallel encryption algorithm based on piecewise linear chaotic map,” Math.
Probl. Eng., vol. 2013, 2013, doi: 10.1155/2013/537934.
[13] N. A. Khan, M. Altaf, and F. A. Khan, “Selective encryption of JPEG images with chaotic based novel
S-box,” Multimed. Tools Appl., vol. 80, no. 6, pp. 9639–9656, Mar. 2021, doi: 10.1007/S11042-020-10110-5/METRICS.
[14] L. C. Nizam Chew and E. S. Ismail, “S-box Construction Based on Linear Fractional Transformation and
Permutation Function,” Symmetry 2020, Vol. 12, Page 826, vol. 12, no. 5, p. 826, May 2020, doi: 10.3390/SYM12050826.
[15] K. Ishaq and A. A. Qarni, “An Innovative Design of Substitution Box Using Trigonometric Transformation,”
Aug. 2023, Accessed: Dec. 26, 2023. [Online]. Available: https://arxiv.org/abs/2311.16107v1
[16] H. Liu, B. Zhao, and L. Huang, “Quantum Image Encryption Scheme Using Arnold Transform and S-box
Scrambling,” Entropy 2019, Vol. 21, Page 343, vol. 21, no. 4, p. 343, Mar. 2019, doi: 10.3390/E21040343.
[17] K. Z. Zamli, “Optimizing S-box generation based on the Adaptive Agent Heroes and Cowards Algorithm,”
Expert Syst. Appl., vol. 182, p. 115305, Nov. 2021, doi: 10.1016/J.ESWA.2021.115305.
[18] X. Wang et al., “S-Box Based Image Encryption Application Using a Chaotic System without Equilibrium,”
Appl. Sci. 2019, Vol. 9, Page 781, vol. 9, no. 4, p. 781, Feb. 2019, doi: 10.3390/APP9040781.
[19] X. Wang, J. Yang, and N. Guan, “High-sensitivity image encryption algorithm with random cross diffusion
based on dynamically random coupled map lattice model,” Chaos, Solitons & Fractals, vol. 143, p. 110582, Feb. 2021, doi:
10.1016/J.CHAOS.2020.110582.
[20] M. Ahmad, E. Al-Solami, A. M. Alghamdi, and M. A. Yousaf, “Bijective S-Boxes Method Using Improved
Chaotic Map-Based Heuristic Search and Algebraic Group Structures,” IEEE Access, vol. 8, pp. 110397–110411, 2020, doi:
10.1109/ACCESS.2020.3001868.
[21] H. Alsaif, R. Guesmi, A. Kalghoum, B. M. Alshammari, and T. Guesmi, “A Novel Strong S-Box Design Using
Quantum Crossover and Chaotic Boolean Functions for Symmetric Cryptosystems,” Symmetry 2023, Vol. 15, Page 833, vol. 15, no.
4, p. 833, Mar. 2023, doi: 10.3390/SYM15040833.
[22] Z. Jiang and Q. Ding, “Construction of an S-Box Based on Chaotic and Bent Functions,” Symmetry 2021, Vol.
13, Page 671, vol. 13, no. 4, p. 671, Apr. 2021, doi: 10.3390/SYM13040671.
[23] M. F. Khan, K. Saleem, M. A. Alshara, and S. Bashir, “Multilevel information fusion for cryptographic
substitution box construction based on inevitable random noise in medical imaging,” Sci. Reports 2021 111, vol. 11, no. 1,
pp. 1–23, Jul. 2021, doi: 10.1038/s41598-021-93344-z.
[24] Q. Lu, C. Zhu, and X. Deng, “An Efficient Image Encryption Scheme Based on the LSS Chaotic Map and Single
S-Box,” IEEE Access, vol. 8, pp. 25664–25678, 2020, doi: 10.1109/ACCESS.2020.2970806.
[25] X. Liu, X. Tong, Z. Wang, and M. Zhang, “Efficient high nonlinearity S-box generating algorithm based on
third-order nonlinear digital filter,” Chaos, Solitons & Fractals, vol. 150, p. 111109, Sep. 2021, doi:
10.1016/J.CHAOS.2021.111109.
[26] M. Ahmad, U. Shamsi, and I. R. Khan, “An Enhanced Image Encryption Algorithm Using Fractional Chaotic
Systems,” Procedia Comput. Sci., vol. 57, pp. 852–859, Jan. 2015, doi: 10.1016/J.PROCS.2015.07.494.
[27] “Image Encryption based on Chaotic Map and Reversible Integer Wavelet Transform.” Accessed: Dec. 09,
2023. [Online]. Available: https://sciendo.com/article/10.2478/jee-2014-0013
[28] A. Razzaque et al., “An efficient S-box design scheme for image encryption based on the combination of a
coset graph and a matrix transformer,” Electron. Res. Arch. 2023 52708, vol. 31, no. 5, pp. 2708–2732, 2023, doi:
10.3934/ERA.2023137.
[29] L. Liu, Y. Zhang, and X. Wang, “A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic
Dynamics,” Appl. Sci. 2018, Vol. 8, Page 2650, vol. 8, no. 12, p. 2650, Dec. 2018, doi: 10.3390/APP8122650.
[30] F. ul Islam and G. Liu, “Designing S-Box Based on 4D-4Wing Hyperchaotic System,” 3D Res., vol. 8, no. 1,
pp. 1–9, Mar. 2017, doi: 10.1007/S13319-017-0119-X/METRICS.
[31] M. A. Arshed, S. Mumtaz, O. Riaz, W. Sharif, and S. Abdullah, “A Deep Learning Framework for Multi-Drug
Side Effects Prediction with Drug Chemical Substructure,” Int. J. Innov. Sci. Technol., vol. 4, no. 1, pp. 19–31, 2022.
[32] M. T. Ubaid, M. Z. Khan, M. Rumaan, M. A. Arshed, M. U. G. Khan, and A. Darboe, “COVID-19 SOP’s
Violations Detection in Terms of Face Mask Using Deep Learning,” 4th Int. Conf. Innov. Comput. ICIC 2021, 2021, doi:
10.1109/ICIC53490.2021.9692999.
[33] M. A. Arshed, H. Ghassan, M. Hussain, M. Hassan, A. Kanwal, and R. Fayyaz, “A Light Weight Deep Learning
Model for Real World Plant Identification,” 2022 2nd Int. Conf. Distrib. Comput. High Perform. Comput. DCHPC 2022, pp. 40–45,
2022, doi: 10.1109/DCHPC55044.2022.9731841.
[34] H. Younis, M. A. Arshed, F. ul Hassan, M. Khurshid, and H. Ghassan, “Tomato Disease Classification using
Fine-Tuned Convolutional Neural Network,” Int. J. Innov. Sci. Technol., vol. 4, no. 1, pp. 123–134, 2022, doi:
10.33411/ijist/2022040109.
[35] M. Mubeen, M. A. Arshed, and H. A. Rehman, “DeepFireNet - A Light-Weight Neural Network for Fire-Smoke
Detection,” Commun. Comput. Inf. Sci., vol. 1616 CCIS, pp. 171–181, 2022, doi: 10.1007/978-3-031-10525-8_14/COVER.
[36] M. A. Arshed, S. Mumtaz, M. Hussain, R. Alamdar, M. T. Hassan, and M. Tanveer, “DeepFinancial Model for
Exchange Rate Impacts Prediction of Political and Financial Statements,” 3rd IEEE Int. Conf. Artif. Intell. ICAI 2023, pp.
13–19, 2023, doi: 10.1109/ICAI58407.2023.10136658.
[37] R. A. A. Shahzad, M. A. Arshed, F. Liaquat, M. Tanveer, M. Hussain, “Pneumonia Classification from Chest
X-ray Images Using Pre-Trained Network Architectures,” VAWKUM trans. Comput. sci., vol. 10, no. 2, pp. 34–44, 2022.
[38] M. T. M. A. Arshed, A. Shahzad, K. Arshad, D. Karim, S. Mumtaz, “Multiclass Brain Tumor Classification
from MRI Images using Pre-Trained CNN Model,” VFAST trans. softw. eng., vol. 10, no. 4, pp. 22–28, 2022.
[39] M. A. Arshed et al., “Machine Learning with Data Balancing Technique for IoT Attack and Anomalies
Detection,” Int. J. Innov. Sci. Technol., vol. 4, no. 2, pp. 490–498, 2022, doi: 10.33411/ijist/2022040218.
[40] H. A. Arshad, M. Hussain, A. Amin, and M. A. Arshed, “Impact of Artificial Intelligence in COVID-19
Pandemic: A Comprehensive Review,” 2022 2nd Int. Conf. Distrib. Comput. High Perform. Comput. DCHPC 2022, pp. 66–73, 2022,
doi: 10.1109/DCHPC55044.2022.9732091.
[41] M. A. Arshed, W. Qureshi, M. Rumaan, M. T. Ubaid, A. Qudoos, and M. U. G. Khan, “Comparison of Machine
Learning Classifiers for Breast Cancer Diagnosis,” 4th Int. Conf. Innov. Comput. ICIC 2021, 2021, doi:
10.1109/ICIC53490.2021.9692926.
[42] M. A. Arshed and F. Riaz, “Machine Learning for High Risk Cardiovascular Patient Identification 1,” J.
Distrib. Comput. Syst., vol. 4, no. 2, pp. 34–39, 2021, Accessed: Dec. 26, 2023. [Online]. Available:
https://ijdcs.ir/wp-content/uploads/2022/08/IJDCS-8-6.pdf
[43] M. Hussain, A. Shahzad, F. Liaquat, M. A. Arshed, S. Mansoor, and Z. Akram, “Performance Analysis of
Machine Learning Algorithms for Early Prognosis of Cardiac Vascular Disease,” Tech. J., vol. 28, no. 02, pp. 31–41, Jun.
2023, Accessed: Dec. 26, 2023. [Online]. Available: https://tj.uettaxila.edu.pk/index.php/technical-journal/article/view/1778
[44] M. F. Idris, J. Sen Teh, J. L. S. Yan, and W. Z. Yeoh, “A Deep Learning Approach for Active S-Box
Prediction of Lightweight Generalized Feistel Block Ciphers,” IEEE Access, vol. 9, pp. 104205–104216, 2021, doi:
10.1109/ACCESS.2021.3099802.
[45] G. Kim, H. Kim, Y. Heo, Y. Jeon, and J. Kim, “Generating Cryptographic S-Boxes Using the Reinforcement
Learning,” IEEE Access, vol. 9, pp. 83092–83104, 2021, doi: 10.1109/ACCESS.2021.3085861.