A Review based on Active Research Areas in Mining Software Bug Repositories: Limitations and Possible Future Trends
Keywords:
Mining Software Repositories, Bug Localization, Bug Classification, Bug Estimation, Bug TriagingAbstract
Introduction/ Importance of Study: Bug repository mining is a crucial research area in software engineering, analyzing software change trends, defect prediction, and evolution. It involves developing methods and tools for mining repositories, providing essential data for bug management.
Objective: The goal of this study is to analyze and synthesize recent trends in mining software bug repositories, providing valuable insights for future research and practical bug management.
Novelty statement: Our research contributes novel insights into mining software repository techniques and approaches employed in specific tasks such as bug localization, triaging, and prediction, along with their limitations and possible future trends.
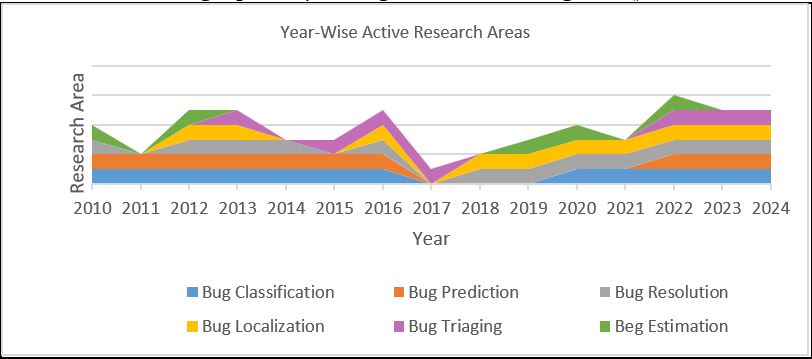
Material and Method: This study presents a comprehensive survey that categorizes and synthesizes the current research within this field. This categorization is derived from an in-depth review of studies conducted over the past fifteen years, from 2010 to 2024. The survey is organized around three key dimensions: the test systems employed in bug repositories, the methodologies commonly used in this area of research, and the prevailing trends shaping the field.
Results and Discussion: Our results highlight the significance of artificial intelligence and machine learning integration in bug repository mining; that has revolutionized software development process by enhancing classification, prediction and vulnerability detection of bugs.
Concluding Remarks: This survey aims to provide a clear and detailed understanding of the evolution of bug repository mining, offering valuable insights for ongoing advancement of software engineering.
References
R. Lotufo, L. Passos, and K. Czarnecki, “Towards improving bug tracking systems with game mechanisms,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 2–11, 2012, doi: 10.1109/MSR.2012.6224293.
B. Sisman and A. C. Kak, “Incorporating version histories in Information Retrieval based bug localization,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 50–59, 2012, doi: 10.1109/MSR.2012.6224299.
N. Bettenburg, M. Nagappan, and A. E. Hassan, “Think locally, act globally: Improving defect and effort prediction models,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 60–69, 2012, doi: 10.1109/MSR.2012.6224300.
Lucia, F. Thung, D. Lo, and L. Jiang, “Are faults localizable?,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 74–77, 2012, doi: 10.1109/MSR.2012.6224302.
V. Guana, F. Rocha, A. Hindle, and E. Stroulia, “Do the stars align? Multidimensional analysis of Android’s layered architecture,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 124–127, 2012, doi: 10.1109/MSR.2012.6224269.
A. Breckel, “Error mining: Bug detection through comparison with large code databases,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 175–178, 2012, doi: 10.1109/MSR.2012.6224278.
S. Wang, F. Khomh, and Y. Zou, “Improving bug localization using correlations in crash reports,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 247–256, 2013, doi: 10.1109/MSR.2013.6624036.
M. Amoui, N. Kaushik, A. Al-Dabbagh, L. Tahvildari, S. Li, and W. Liu, “Search-based duplicate defect detection: An industrial experience,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 173–182, 2013, doi: 10.1109/MSR.2013.6624025.
B. Sisman and A. C. Kak, “Assisting code search with automatic query reformulation for bug localization,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 309–318, 2013, doi: 10.1109/MSR.2013.6624044.
“Locating Bugs without Looking Back | IEEE Conference Publication | IEEE Xplore.” Accessed: Aug. 28, 2024. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/7832908
R. Malhotra, S. Aggarwal, R. Girdhar, and R. Chugh, “Bug localization in software using NSGA-II,” ISCAIE 2018 - 2018 IEEE Symp. Comput. Appl. Ind. Electron., pp. 428–433, Jul. 2018, doi: 10.1109/ISCAIE.2018.8405511.
V. Iyer, D. Kim, B. Nikolic, and S. A. Seshia, “RTL bug localization through LTL specification mining (WIP),” MEMOCODE 2019 - 17th ACM-IEEE Int. Conf. Form. Methods Model. Syst. Des., Oct. 2019, doi: 10.1145/3359986.3361202.
S. A. Akbar, “Source Code Search for Automatic Bug Localization,” Theses Diss. Available from ProQuest, Jan. 2020, Accessed: Aug. 28, 2024. [Online]. Available: https://docs.lib.purdue.edu/dissertations/AAI30504782
M. Medeiros, U. Kulesza, R. Bonifacio, E. Adachi, and R. Coelho, “Improving Bug Localization by Mining Crash Reports: An Industrial Study,” Proc. - 2020 IEEE Int. Conf. Softw. Maint. Evol. ICSME 2020, pp. 766–775, Sep. 2020, doi: 10.1109/ICSME46990.2020.00086.
A. Sood et al., “Bug Localization Using Multi-objective Approach and Information Retrieval,” Adv. Intell. Syst. Comput., vol. 1165, pp. 709–723, 2021, doi: 10.1007/978-981-15-5113-0_58.
Z. Zhu, H. Tong, Y. Wang, and Y. Li, “Enhancing bug localization with bug report decomposition and code hierarchical network,” Knowledge-Based Syst., vol. 248, p. 108741, Jul. 2022, doi: 10.1016/J.KNOSYS.2022.108741.
Y. Zhao, X. Li, Y. Li, Y. Zhang, W. Qi, and J. Song, “Bug localization with semantic guidance using pseudo-Siamese network,” SPIE, vol. 12721, p. 127210A, Jun. 2023, doi: 10.1117/12.2683291.
S. Jahan, M. B. Shah, and M. M. Rahman, “Towards Understanding the Challenges of Bug Localization in Deep Learning Systems,” Feb. 2024, Accessed: Aug. 28, 2024. [Online]. Available: https://arxiv.org/abs/2402.01021v1
C. Sun, D. Lo, X. Wang, J. Jiang, and S. C. Khoo, “A discriminative model approach for accurate duplicate bug report retrieval,” Proc. - Int. Conf. Softw. Eng., vol. 1, pp. 45–54, 2010, doi: 10.1145/1806799.1806811.
N. K. Nagwani and A. Bhansali, “A data mining model to predict software bug complexity using bug estimation and clustering,” ITC 2010 - 2010 Int. Conf. Recent Trends Information, Telecommun. Comput., pp. 13–17, 2010, doi: 10.1109/ITC.2010.56.
G. Bougie, C. Treude, D. M. German, and M. A. Storey, “A comparative exploration of FreeBSD bug lifetimes,” Proc. - Int. Conf. Softw. Eng., pp. 106–109, 2010, doi: 10.1109/MSR.2010.5463291.
D. Wijayasekara, M. Manic, J. L. Wright, and M. McQueen, “Mining bug databases for unidentified software vulnerabilities,” Int. Conf. Hum. Syst. Interact. HSI, pp. 89–96, 2012, doi: 10.1109/HSI.2012.22.
S. Xie, F. Khomh, and Y. Zou, “An empirical study of the fault-proneness of clone mutation and clone migration,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 149–158, 2013, doi: 10.1109/MSR.2013.6624022.
A. Alipour, A. Hindle, and E. Stroulia, “A contextual approach towards more accurate duplicate bug report detection,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 183–192, 2013, doi: 10.1109/MSR.2013.6624026.
W. Hu and K. Wong, “Using Citation Influence to Predict Software Defects”.
K. Herzig, S. Just, and A. Zeller, “It’s not a bug, it’s a feature: How misclassification impacts bug prediction,” Proc. - Int. Conf. Softw. Eng., pp. 392–401, 2013, doi: 10.1109/ICSE.2013.6606585.
H. Valdivia-Garcia, E. Shihab, and M. Nagappan, “Characterizing and predicting blocking bugs in open source projects,” J. Syst. Softw., vol. 143, pp. 44–58, Sep. 2018, doi: 10.1016/J.JSS.2018.03.053.
Y. Liu, C. Xu, and S. C. Cheung, “Characterizing and detecting performance bugs for smartphone applications,” Proc. - Int. Conf. Softw. Eng., no. 1, pp. 1013–1024, May 2014, doi: 10.1145/2568225.2568229.
F. Zhang, A. Mockus, I. Keivanloo, and Y. Zou, “Towards building a universal defect prediction model,” 11th Work. Conf. Min. Softw. Repos. MSR 2014 - Proc., pp. 182–191, May 2014, doi: 10.1145/2597073.2597078.
R. Coelho, L. Almeida, G. Gousios, and A. Van Deursen, “Unveiling exception handling bug hazards in android based on GitHub and Google code issues,” IEEE Int. Work. Conf. Min. Softw. Repos., vol. 2015-August, pp. 134–145, Aug. 2015, doi: 10.1109/MSR.2015.20.
P. Abate, R. Di Cosmo, L. Gesbert, F. Le Fessant, R. Treinen, and S. Zacchiroli, “Mining component repositories for installability issues,” IEEE Int. Work. Conf. Min. Softw. Repos., vol. 2015-August, pp. 24–33, Aug. 2015, doi: 10.1109/MSR.2015.10.
W. Maalej and H. Nabil, “Bug report, feature request, or simply praise? On automatically classifying app reviews,” 2015 IEEE 23rd Int. Requir. Eng. Conf. RE 2015 - Proc., pp. 116–125, Nov. 2015, doi: 10.1109/RE.2015.7320414.
F. Camilo, A. Meneely, and M. Nagappan, “Do bugs foreshadow vulnerabilities? A study of the chromium project,” IEEE Int. Work. Conf. Min. Softw. Repos., vol. 2015-August, pp. 269–279, Aug. 2015, doi: 10.1109/MSR.2015.32.
P. Ciancarini, F. Poggi, D. Rossi, and A. Sillitti, “Mining Concurrency Bugs”, Accessed: Aug. 27, 2024. [Online]. Available: https://bz.apache.org/bugzilla/
J. Xuan et al., “Towards effective bug triage with software data reduction techniques,” IEEE Trans. Knowl. Data Eng., vol. 27, no. 1, pp. 264–280, Jan. 2015, doi: 10.1109/TKDE.2014.2324590.
“U.S. Patent and Trademark Office | U.S. Department of Commerce.” Accessed: Aug. 28, 2024. [Online]. Available: https://www.commerce.gov/bureaus-and-offices/uspto
F. Fang, J. Wu, Y. Li, X. Ye, W. Aljedaani, and M. W. Mkaouer, “On the classification of bug reports to improve bug localization,” Soft Comput., vol. 25, no. 11, pp. 7307–7323, Jun. 2021, doi: 10.1007/S00500-021-05689-2/METRICS.
M. N. Noor, T. A. Khan, F. Haneef, and M. I. Ramay, “Machine Learning Model to Predict Automated Testing Adoption,” https://services.igi-global.com/resolvedoi/resolve.aspx?doi=10.4018/IJSI.293268, vol. 10, no. 1, pp. 1–15, Jan. 1AD, doi: 10.4018/IJSI.293268.
O. Koksal and C. E. Ozturk, “A Survey on Machine Learning-based Automated Software Bug Report Classification,” ISMSIT 2022 - 6th Int. Symp. Multidiscip. Stud. Innov. Technol. Proc., pp. 635–640, 2022, doi: 10.1109/ISMSIT56059.2022.9932822.
L. Zhifang, W. Kun, Z. Qi, L. Shengzong, Z. Yan, and H. Jianbiao, “Classification of open source software bug report based on transfer learning,” Expert Syst., vol. 41, no. 5, p. e13184, May 2024, doi: 10.1111/EXSY.13184.
P. Yildirim Taser, “A novel multi-view ordinal classification approach for software bug prediction,” Expert Syst., vol. 39, no. 7, p. e13044, Aug. 2022, doi: 10.1111/EXSY.13044.
Y. Tang, H. Zhou, and H. Su, “Automatic Classification of Software Bug Reports Based on LDA and Word2Vec,” 2022 2nd Int. Conf. Comput. Sci. Electron. Inf. Eng. Intell. Control Technol. CEI 2022, pp. 491–495, 2022, doi: 10.1109/CEI57409.2022.9950207.
A. Singh, P. K. Kapur, and V. B. Singh, “Developing classifiers by considering sentiment analysis of reported bugs for priority prediction,” Int. J. Syst. Assur. Eng. Manag., vol. 15, no. 5, pp. 1888–1899, May 2024, doi: 10.1007/S13198-023-02199-2/METRICS.
L. Chmielowski and M. Kucharzak, “Impact of Software Bug Report Preprocessing and Vectorization on Bug Assignment Accuracy,” Lect. Notes Networks Syst., vol. 255, pp. 153–162, 2022, doi: 10.1007/978-3-030-81523-3_15.
B. Ilijoski et al., “Deep Learning Methods for Bug Bite Classification: An End-to-End System,” Appl. Sci. 2023, Vol. 13, Page 5187, vol. 13, no. 8, p. 5187, Apr. 2023, doi: 10.3390/APP13085187.
N. Tabassum, A. Namoun, T. Alyas, A. Tufail, M. Taqi, and K. H. Kim, “Classification of Bugs in Cloud Computing Applications Using Machine Learning Techniques,” Appl. Sci. 2023, Vol. 13, Page 2880, vol. 13, no. 5, p. 2880, Feb. 2023, doi: 10.3390/APP13052880.
J. P. Meher, S. Biswas, and R. Mall, “Deep learning-based software bug classification,” Inf. Softw. Technol., vol. 166, p. 107350, Feb. 2024, doi: 10.1016/J.INFSOF.2023.107350.
D. Wang, M. Lin, H. Zhang, and H. Hu, “Detect related bugs from source code using bug information,” Proc. - Int. Comput. Softw. Appl. Conf., pp. 228–237, 2010, doi: 10.1109/COMPSAC.2010.27.
N. K. Nagwani and S. Verma, “Predictive data mining model for software bug estimation using average weighted similarity,” 2010 IEEE 2nd Int. Adv. Comput. Conf. IACC 2010, pp. 373–378, 2010, doi: 10.1109/IADCC.2010.5422923.
C. Rahmani and D. Khazanchi, “A study on defect density of open source software,” Proc. - 9th IEEE/ACIS Int. Conf. Comput. Inf. Sci. ICIS 2010, pp. 679–683, 2010, doi: 10.1109/ICIS.2010.11.
M. Asaduzzaman, M. C. Bullock, C. K. Roy, and K. A. Schneider, “Bug introducing changes: A case study with Android,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 116–119, 2012, doi: 10.1109/MSR.2012.6224267.
L. Martie, V. K. Palepu, H. Sajnani, and C. Lopes, “Trendy bugs: Topic trends in the Android bug reports,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 120–123, 2012, doi: 10.1109/MSR.2012.6224268.
M. Steff and B. Russo, “Co-evolution of logical couplings and commits for defect estimation,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 213–216, 2012, doi: 10.1109/MSR.2012.6224283.
A. C. Nguyen and S. C. Khoo, “Discovering complete API rules with mutation testing,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 151–160, 2012, doi: 10.1109/MSR.2012.6224275.
C. Sadowski, J. Yi, and S. Kim, “The evolution of data races,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 171–174, 2012, doi: 10.1109/MSR.2012.6224277.
T. H. Chen, S. W. Thomas, M. Nagappan, and A. E. Hassan, “Explaining software defects using topic models,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 189–198, 2012, doi: 10.1109/MSR.2012.6224280.
R. Sawarkar, N. K. Nagwani, and S. Kumar, “Predicting Bug Estimation Time for Newly Reported Bug Using Machine Learning Algorithms,” 2019 IEEE 5th Int. Conf. Converg. Technol. I2CT 2019, Mar. 2019, doi: 10.1109/I2CT45611.2019.9033749.
A. Munde, “Envisaging Bugs by Means of Entropy Measures,” Smart Innov. Syst. Technol., vol. 196, pp. 149–156, 2021, doi: 10.1007/978-981-15-7062-9_15.
H. Mahfoodh and Q. Obediat, “Software Risk Estimation through Bug Reports Analysis and Bug-fix Time Predictions,” 2020 Int. Conf. Innov. Intell. Informatics, Comput. Technol. 3ICT 2020, Dec. 2020, doi: 10.1109/3ICT51146.2020.9312003.
M. Kumari, U. K. Singh, and M. Sharma, “Entropy Based Machine Learning Models for Software Bug Severity Assessment in Cross Project Context,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 12254 LNCS, pp. 939–953, 2020, doi: 10.1007/978-3-030-58817-5_66.
E. Mashhadi, S. Chowdhury, S. Modaberi, H. Hemmati, and G. Uddin, “An Empirical Study on Bug Severity Estimation using Source Code Metrics and Static Analysis,” Jun. 2022, doi: 10.1016/j.jss.2024.112179.
D. Tambe and L. Ragha, “Analysis of Software Bug Prediction and Tracing Models from a Statistical Perspective Using Machine Learning,” 2022 2nd Int. Conf. Intell. Technol. CONIT 2022, 2022, doi: 10.1109/CONIT55038.2022.9848385.
A. Bachmann and A. Bernstein, “When process data quality affects the number of bugs: Correlations in software engineering datasets,” Proc. - Int. Conf. Softw. Eng., pp. 62–71, 2010, doi: 10.1109/MSR.2010.5463286.
Y. Liu and K. Ben, “Knowledge representation of software faults based on open bug repository,” 2010 Int. Conf. Comput. Des. Appl. ICCDA 2010, vol. 2, 2010, doi: 10.1109/ICCDA.2010.5541110.
R. Souza and C. Chavez, “Characterizing verification of bug fixes in two open source IDEs,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 70–73, 2012, doi: 10.1109/MSR.2012.6224301.
J. Park, M. Kim, B. Ray, and D.-H. Bae, “An Empirical Study of Supplementary Bug Fixes”, Accessed: Aug. 27, 2024. [Online]. Available: http://cvs2svn.tigris.org/
A. Issabayeva, A. Nugroho, and J. Visser, “Issue handling performance in proprietary software projects,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 209–212, 2012, doi: 10.1109/MSR.2012.6224282.
S. Mani, S. Nagar, D. Mukherjee, R. Narayanam, V. S. Sinha, and A. A. Nanavati, “Bug resolution catalysts: Identifying essential non-committers from bug repositories,” 2013 10th IEEE Work. Conf. Min. Softw. Repos. (MSR 2013), pp. 193–202, May 2013, doi: 10.1109/MSR.2013.6624027.
A. Nistor, T. Jiang, and L. Tan, “Discovering, reporting, and fixing performance bugs,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 237–246, 2013, doi: 10.1109/MSR.2013.6624035.
T. H. Chen, M. Nagappan, E. Shihab, and A. E. Hassan, “An empirical study of dormant bugs,” 11th Work. Conf. Min. Softw. Repos. MSR 2014 - Proc., pp. 82–91, May 2014, doi: 10.1145/2597073.2597108.
H. Osman, M. Lungu, and O. Nierstrasz, “Mining frequent bug-fix code changes,” 2014 Softw. Evol. Week - IEEE Conf. Softw. Maintenance, Reengineering, Reverse Eng. CSMR-WCRE 2014 - Proc., pp. 343–347, 2014, doi: 10.1109/CSMR-WCRE.2014.6747191.
M. Gupta, A. Sureka, and S. Padmanabhuni, “Process mining multiple repositories for software defect resolution from control and organizational perspective,” 11th Work. Conf. Min. Softw. Repos. MSR 2014 - Proc., pp. 122–131, May 2014, doi: 10.1145/2597073.2597081.
H. Oumarou, N. Anquetil, A. Etien, S. Ducasse, and K. D. Taiwe, “Identifying the Exact Bug Fixing Actions,” Proc. - 7th Int. Work. Empir. Softw. Eng. Pract. IWESEP 2016, pp. 51–56, May 2016, doi: 10.1109/IWESEP.2016.13.
“A Deeper Look into Bug Fixes: Patterns, Replacements, Deletions, and Additions | IEEE Conference Publication | IEEE Xplore.” Accessed: Aug. 28, 2024. [Online]. Available: https://ieeexplore.ieee.org/document/7832938
“CLEVER: Combining Code Metrics with Clone Detection for Just-in-Time Fault Prevention and Resolution in Large Industrial Projects | IEEE Conference Publication | IEEE Xplore.” Accessed: Aug. 28, 2024. [Online]. Available: https://ieeexplore.ieee.org/document/8595198
J. M. Zhang et al., “A Study of Bug Resolution Characteristics in Popular Programming Languages,” IEEE Trans. Softw. Eng., vol. 47, no. 12, pp. 2684–2697, Dec. 2021, doi: 10.1109/TSE.2019.2961897.
“The Symptom, Cause and Repair of Workaround | IEEE Conference Publication | IEEE Xplore.” Accessed: Aug. 28, 2024. [Online]. Available: https://ieeexplore.ieee.org/document/9286099
L. Chmielowski, M. Kucharzak, and R. Burduk, “APPLICATION OF EXPLAINABLE ARTIFICIAL INTELLIGENCE IN SOFTWARE BUG CLASSIFICATION,” Inform. Autom. Pomiary w Gospod. i Ochr. Środowiska, vol. 13, no. 1, pp. 14–17, Mar. 2023, doi: 10.35784/IAPGOS.3396.
M. A. Arshad and H. Zhiqiu, “Using CNN to Predict the Resolution Status of Bug Reports,” J. Phys. Conf. Ser., vol. 1828, no. 1, p. 012106, Feb. 2021, doi: 10.1088/1742-6596/1828/1/012106.
M. K. Yucel and A. Tosun, “Measuring Bug Reporter’s Reputation and Its Effect on Bug Resolution Time Prediction,” Proc. - 7th Int. Conf. Comput. Sci. Eng. UBMK 2022, pp. 110–115, 2022, doi: 10.1109/UBMK55850.2022.9919454.
E. Eiroa-Lledo, R. H. Ali, G. Pinto, J. Anderson, and E. Linstead, “Large-Scale Identification and Analysis of Factors Impacting Simple Bug Resolution Times in Open Source Software Repositories,” Appl. Sci. 2023, Vol. 13, Page 3150, vol. 13, no. 5, p. 3150, Feb. 2023, doi: 10.3390/APP13053150.
“Machine Learning and Just-in-Time Strategies for Effective Bug Tracking in Software Development | International Journal of Intelligent Systems and Applications in Engineering.” Accessed: Aug. 28, 2024. [Online]. Available: https://ijisae.org/index.php/IJISAE/article/view/4013
F. Haneef and M. A. Sindhu, “DLIQ: A Deterministic Finite Automaton Learning Algorithm through Inverse Queries,” Inf. Technol. Control, vol. 51, no. 4, pp. 611–624, Dec. 2022, doi: 10.5755/J01.ITC.51.4.31394.
F. Haneef and M. A. Sindhu, “IDLIQ: An Incremental Deterministic Finite Automaton Learning Algorithm Through Inverse Queries for Regular Grammar Inference,” https://home.liebertpub.com/big, May 2023, doi: 10.1089/BIG.2022.0158.
R. Shokripour, J. Anvik, Z. M. Kasirun, and S. Zamani, “Why so complicated? Simple term filtering and weighting for location-based bug report assignment recommendation,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 2–11, 2013, doi: 10.1109/MSR.2013.6623997.
H. Naguib, N. Narayan, B. Brügge, and D. Helal, “Bug report assignee recommendation using activity profiles,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 22–30, 2013, doi: 10.1109/MSR.2013.6623999.
“(PDF) Efficient Bug Triaging Using Text Mining.” Accessed: Aug. 27, 2024. [Online]. Available: https://www.researchgate.net/publication/235911086_Efficient_Bug_Triaging_Using_Text_Mining
A. Lamkanfi, J. Pérez, and S. Demeyer, “The eclipse and mozilla defect tracking dataset: A genuine dataset for mining bug information,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 203–206, 2013, doi: 10.1109/MSR.2013.6624028.
J. Xuan, H. Jiang, Z. Ren, and W. Zou, “Developer prioritization in bug repositories,” Proc. - Int. Conf. Softw. Eng., pp. 25–35, 2012, doi: 10.1109/ICSE.2012.6227209.
M. E. Joorabchi, M. Mirzaaghaei, and A. Mesbah, “Works for me! characterizing non-reproducible bug reports,” 11th Work. Conf. Min. Softw. Repos. MSR 2014 - Proc., pp. 62–71, May 2014, doi: 10.1145/2597073.2597098.
C. A. Thompson, G. C. Murphy, M. Palyart, and M. Gašparič, “How Software developers use work breakdown relationships in issue repositories,” Proc. - 13th Work. Conf. Min. Softw. Repos. MSR 2016, pp. 281–285, May 2016, doi: 10.1145/2901739.2901779.
Tamanna and O. P. Sangwan, “Review of text mining techniques for software bug localization,” Proc. 9th Int. Conf. Cloud Comput. Data Sci. Eng. Conflu. 2019, pp. 208–211, Jan. 2019, doi: 10.1109/CONFLUENCE.2019.8776959.
A. Chauhan and R. Kumar, “Bug Severity Classification Using Semantic Feature with Convolution Neural Network,” Adv. Intell. Syst. Comput., vol. 1025, pp. 327–335, 2019, doi: 10.1007/978-981-32-9515-5_31.
S. Panthaplackel, J. J. Li, M. Gligoric, and R. J. Mooney, “Learning to Describe Solutions for Bug Reports Based on Developer Discussions,” Proc. Annu. Meet. Assoc. Comput. Linguist., pp. 2935–2952, 2022, doi: 10.18653/V1/2022.FINDINGS-ACL.231.
“GitHub - HadiJahanshahi/ADPTriage: ADPTriage: Approximate Dynamic Programming for Bug Triage.” Accessed: Aug. 28, 2024. [Online]. Available: https://github.com/HadiJahanshahi/ADPTriage
R. R. Panda and N. K. Nagwani, “An Improved Software Bug Triaging Approach Based on Topic Modeling and Fuzzy Logic,” Lect. Notes Networks Syst., vol. 479, pp. 337–346, 2023, doi: 10.1007/978-981-19-3148-2_29.
Y. Liu, X. Qi, J. Zhang, H. Li, X. Ge, and J. Ai, “Automatic Bug Triaging via Deep Reinforcement Learning,” Appl. Sci. 2022, Vol. 12, Page 3565, vol. 12, no. 7, p. 3565, Mar. 2022, doi: 10.3390/APP12073565.
J. Jang and G. Yang, “A Bug Triage Technique Using Developer-Based Feature Selection and CNN-LSTM Algorithm,” Appl. Sci. 2022, Vol. 12, Page 9358, vol. 12, no. 18, p. 9358, Sep. 2022, doi: 10.3390/APP12189358.
H. Dong, H. Ren, J. Shi, Y. Xie, and X. Hu, “Neighborhood contrastive learning-based graph neural network for bug triaging,” Sci. Comput. Program., vol. 235, p. 103093, Jul. 2024, doi: 10.1016/J.SCICO.2024.103093.
S. Raemaekers, G. F. Nane, A. Van Deursen, and J. Visser, “Testing principles, current practices, and effects of change localization,” IEEE Int. Work. Conf. Min. Softw. Repos., pp. 257–266, 2013, doi: 10.1109/MSR.2013.6624037.
& S. Hart, G. W., Kern Jr, E. C., “F. C. (1989). U.S. Patent No. 4,858,141. Washington, DC: U.S. Patent and Trademark Office.”.
F. Haneef, “Review of Automaton Learning Algorithms with Polynomial Complexity -- Completely Solved Examples,” Apr. 2024, Accessed: Aug. 28, 2024. [Online]. Available: https://arxiv.org/abs/2404.11096v1
“(PDF) A Review on Big Data and Social Network Analytics Techniques.” Accessed: Aug. 28, 2024. [Online]. Available: https://www.researchgate.net/publication/342144889_A_Review_on_Big_Data_and_Social_Network_Analytics_Techniques
I. M. Pereira, T. G. de Senna Carneiro, and E. Figueiredo, “Exploring the Ci/Cd Pipeline in Floss Repositories of Embedded Iot Systems”, doi: 10.2139/SSRN.4529908.
G. A. Destro and B. B. N. De França, “Mining Software Repositories for the Characterization of Continuous Integration and Delivery,” ACM Int. Conf. Proceeding Ser., pp. 664–669, Oct. 2020, doi: 10.1145/3422392.3422503.
F. Haneef and M. A. Sindhu, “A Reinforcement Learning Based Grammatical Inference Algorithm Using Block-Based Delta Inverse Strategy,” IEEE Access, vol. 11, pp. 12525–12535, 2023, doi: 10.1109/ACCESS.2023.3242124.
J. P. Meher and R. Mall, “Machine Learning-based Software Bug Classification through Mining Open Source Repositories,” OCIT 2023 - 21st Int. Conf. Inf. Technol. Proc., pp. 17–22, 2023, doi: 10.1109/OCIT59427.2023.10431348.
S. M. Abozeed, M. Y. Elnainay, S. A. Fouad, and M. S. Abougabal, “Software bug prediction employing feature selection and deep learning,” 2019 Int. Conf. Adv. Emerg. Comput. Technol. AECT 2019, Feb. 2020, doi: 10.1109/AECT47998.2020.9194215.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 50SEA

This work is licensed under a Creative Commons Attribution 4.0 International License.




















