Machine Learning-Based Improvement of Smart Contract Security in Fog Computing Using Word2vec And Bert
Keywords:
Fog Computing, Smart Contract, Machine Learning, Security and Feature ExtractionAbstract
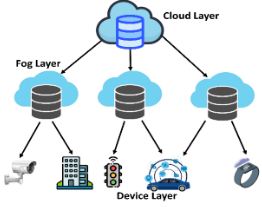
Fog computing extends cloud computing services closer to users, improving efficiency and reducing latency. Smart contracts play a key role in authentication and resource access management within this framework. As the adoption of smart contracts in fog computing grows, ensuring their security has become a major challenge. This study enhances smart contract attack detection in fog computing using machine learning techniques. A dataset of 818 smart contracts was collected from “etherscan.io.” Feature extraction was performed using Word2Vec and BERT, while feature selection was done using the information gain method. The Random Forest (RF) and Extra Trees Classifier (ETC) achieved the highest accuracy of 0.91 with Word2Vec, while the LightGBM (LGBM) classifier attained 0.90 accuracy using BERT.
These results demonstrate the effectiveness of machine learning models in improving smart contract security within fog computing environments.
References
W. M. Anwer, S. M. Khan, M. U. Farooq, “Attack Detection in IoT using Machine Learning,” Eng. Technol. Appl. Sci. Res., vol. 11, no. 3, pp. 7273–7278, 2021, doi: https://doi.org/10.48084/etasr.4202.
M. A. A.-F. Zain Ashi, Mohammad Al-Fawa’reh, “Fog computing: security challenges and countermeasures,” Int. J. Comput. Appl. Technol., vol. 175, no. 15, pp. 30–36, 2020, doi: 10.5120/ijca2020920648.
Y. I. Alzoubi, V. H. Osmanaj, A. Jaradat, and A. Al-Ahmad, “Fog computing security and privacy for the Internet of Thing applications: State-of-the-art,” Secur. Priv., vol. 4, no. 2, p. e145, Mar. 2021, doi: 10.1002/SPY2.145.
A. Ehsan et al., “Enhanced Anomaly Detection in Ethereum: Unveiling and Classifying Threats With Machine Learning,” IEEE Access, vol. 12, pp. 176440–176456, 2024, doi: 10.1109/ACCESS.2024.3504300.
A. G. & A. M. Yehia Ibrahim Alzoubi, “A systematic review of the purposes of Blockchain and fog computing integration: classification and open issues,” J. Cloud Comput., vol. 11, no. 80, 2022, doi: https://doi.org/10.1186/s13677-022-00353-y.
V. C. M. L. Yao Du, Zehua Wang, “Blockchain-Enabled Edge Intelligence for IoT: Background, Emerging Trends and Open Issues,” Futur. Internet, vol. 13, no. 2, p. 48, 2021, doi: https://doi.org/10.3390/fi13020048.
T. Hewa, A. Braeken, M. Liyanage, and M. Ylianttila, “Fog Computing and Blockchain-Based Security Service Architecture for 5G Industrial IoT-Enabled Cloud Manufacturing,” IEEE Trans. Ind. Informatics, vol. 18, no. 10, pp. 7174–7185, Oct. 2022, doi: 10.1109/TII.2022.3140792.
S. K. Dwivedi, R. Amin, and S. Vollala, “Smart contract and IPFS-based trustworthy secure data storage and device authentication scheme in fog computing environment,” Peer-to-Peer Netw. Appl., vol. 16, no. 1, pp. 1–21, Jan. 2023, doi: 10.1007/S12083-022-01376-7/METRICS.
H. A. S. F. Alaba, “Smart Contracts Security Application and Challenges: A Review,” Cloud Comput. Data Sci., 2023, doi: 10.37256/ccds.5120233271.
R. Gupta, M. M. Patel, and S. T. Shukla, Arpit, “Deep learning-based malicious smart contract detection scheme for internet of things environment,” Comput. Electr. Eng., vol. 97, p. 107583, 2022, doi: https://doi.org/10.1016/j.compeleceng.2021.107583.
T. Ehsan et al, “Securing Smart Contracts in Fog Computing: Machine Learning-Based Attack Detection for Registration and Resource Access Granting,” IEEE Access, vol. 12, pp. 42802–42815, 2024, doi: 10.1109/ACCESS.2024.3378736.
et al Liu C. H., Sun J., Ni W., “Blockchain-enabled secure fog platform: Issues, challenges and solutions,” IEEE Commun. Surv. Tutorials, vol. 22, no. 4, pp. 2488–2521, 2020.
K. D. Otuekong Umoren, Raman Singh, Zeeshan Pervez, “Securing Fog Computing with a Decentralised User Authentication Approach Based on Blockchain,” Sensors (Basel), vol. 22, no. 10, p. 3956, 2022, doi: 10.3390/s22103956.
M. Soud, I. Qasse, G. Liebel, and M. Hamdaqa, “AutoMESC: Automatic Framework for Mining and Classifying Ethereum Smart Contract Vulnerabilities and Their Fixes,” Proc. - 2023 49th Euromicro Conf. Softw. Eng. Adv. Appl. SEAA 2023, pp. 410–417, 2023, doi: 10.1109/SEAA60479.2023.00068.
V. F. Derek Liu, Francesco Piccoli, “Machine Learning Approach to Identify Malicious Smart Contract Opcodes: A Preliminary Study,” JPS Conf. Proc., 2024, [Online]. Available: https://journals.jps.jp/doi/10.7566/JPSCP.43.011002
Q. Q. Ali Aljofey, Abdur Rasool, Qingshan Jiang, “A Feature-Based Robust Method for Abnormal Contracts Detection in Ethereum Blockchain,” Electronics, vol. 11, no. 18, p. 2937, 2022, doi: https://doi.org/10.3390/electronics11182937.
et al Wang T., Zhang S., Liu Y., “AI-driven detection of malicious smart contracts in blockchain networks,” Neural Comput. Appl., vol. 34, no. 10, pp. 7945–7962, 2022.
P. Kumar, R. Kumar, G. P. Gupta, and R. Tripathi, “A Distributed framework for detecting DDoS attacks in smart contract-based Blockchain-IoT Systems by leveraging Fog computing,” Trans. Emerg. Telecommun. Technol., vol. 32, no. 6, p. e4112, Jun. 2021, doi: 10.1002/ETT.4112.
et al Rehman R., Khan N., Uddin F., “Distributed denial-of-service attack detection using machine learning in IoT-enabled smart environments,” IEEE Internet Things J., vol. 9, no. 14, pp. 12687–12698, 2022.
S. El Haddouti, M. Khaldoune, M. Ayache, and M. D. Ech-Cherif El Kettani, “Smart contracts auditing and multi-classification using machine learning algorithms: an efficient vulnerability detection in ethereum blockchain,” Computing, vol. 106, no. 9, pp. 2971–3003, Sep. 2024, doi: 10.1007/S00607-024-01314-W/METRICS.
J. U. Fahad Hossain, Mehedi Hasan Shuvo, “A hybrid machine learning approach for improved ponzi scheme detection using advanced feature engineering,” Int. J. Informatics Commun. Technol., vol. 14, no. 1, pp. 50–58, 2025, [Online]. Available: https://ijict.iaescore.com/index.php/IJICT/article/view/21270
Forta Network, “Forta-network/labelled-datasets,” GitHub. Accessed: Mar. 27, 2025. [Online]. Available: https://github.com/forta-network/labelled-datasets
R. Buyya and S. N. Srirama, “Fog and edge computing : principles and paradigms,” p. 471, 2019.
P. L. Fei He, Fei Li, “Enhancing smart contract security: Leveraging pre-trained language models for advanced vulnerability detection,” IET Blockchain, 2024, doi: https://doi.org/10.1049/blc2.12072.
Qusai Omar Mustafa Hasan, “Machine Learning Based Framework for Smart Contract Vulnerability Detection,” Rochester Institute of Technology. Accessed: Mar. 27, 2025. [Online]. Available: https://books.google.com.pk/books/about/Machine_Learning_Based_Framework_for_Sma.html?id=EvML0AEACAAJ&redir_esc=y
S. Ji, C. Huang, P. Zhang, H. Dong, and Y. Xiao, “Ponzi Scheme Detection Based on Control Flow Graph Feature Extraction,” Proc. - 2023 IEEE Int. Conf. Web Serv. ICWS 2023, pp. 585–594, 2023, doi: 10.1109/ICWS60048.2023.00077.
M. Wang and J. Huang, “Detecting Ethereum Ponzi Schemes Through Opcode Context Analysis and Oversampling-Based AdaBoost Algorithm,” Comput. Syst. Sci. Eng., vol. 47, no. 1, pp. 1023–1042, May 2023, doi: 10.32604/CSSE.2023.039569.
T. L. Xueshuo Xie, Haolong Wang, Zhaolong Jian, Yaozheng Fang, Zichun Wang, “Block-gram: Mining knowledgeable features for efficiently smart contract vulnerability detection,” Digit. Commun. Networks, vol. 11, no. 1, pp. 1–12, 2025, doi: https://doi.org/10.1016/j.dcan.2023.07.009.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 50sea

This work is licensed under a Creative Commons Attribution 4.0 International License.




















