A Revolutionary Approach Using Artificial Intelligence and Quantum Cryptography – A Review
Keywords:
Quantum Computing, Quantum Cryptography, Post-Quantum Cryptography, Artificial Intelligence, Quantum Machine LearningAbstract
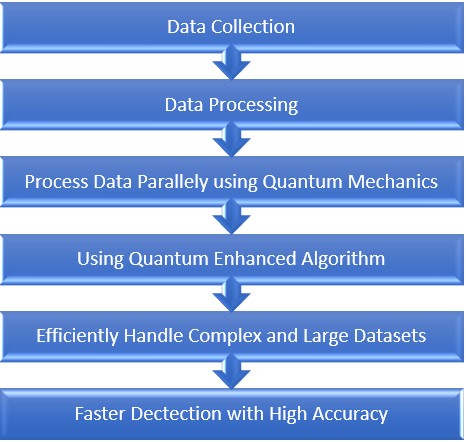
Data security is one of the most important aspects of the digital world as technology evolves and expands. Existing cryptographic systems are vulnerable due to quantum threats. The integration of Artificial Intelligence with Quantum Cryptography is an emerging field. AI-driven methods in QC to mitigate and be robust against the quantum threat. Quantum computing uses quantum mechanics to process data very quickly and accurately. Quantum Machine Learning can process big data as compare to classical methods with much more efficiency. The synergistic combination improves the threat detection and classification with accuracy. The integration also significantly enhances the speed and scalability of the large-scale deployment. AI enhances the efficiency and security of QC systems, and the challenges and opportunities of using AI-powered integration of quantum computing are reviewed.
References
M. Mafu, “Advances in artificial intelligence and machine learning for quantum communication applications,” IET Quantum Commun., vol. 5, no. 3, pp. 202–231, Sep. 2024, doi: 10.1049/QTC2.12094;WGROUP:STRING:PUBLICATION.
A. H. Hussain, N. Hasan, N. U. Prince, M. Islam, S. Islam, and S. K. Hasan, “Enhancing cyber security using quantum computing and Artificial Intelligence: A review,” World J. Adv. Res. Rev., vol. 2021, no. 03, pp. 448–456, 2021, doi: 10.30574/wjarr.2021.10.3.0196.
U. U. Mujeeb-ur-Rehman Jamali, Najma Imtiaz Ali, Imtiaz Ali Brohi, Muhammad Umar Murad, Yasir Nawaz, “An Empirical Evaluation of Data Integrity Algorithm Performance in Non-Relational Document Databases,” VAWKUM Trans. Comput. Sci., vol. 11, no. 2, pp. 70–82, 2023, doi: https://doi.org/10.21015/vtcs.v11i2.1663.
A. Jamali, Mujeeb-ur-Rehman; Ali, Najma Imtiaz; Memon, Abdul Ghafoor; Maree, Mujeeb-u-Rehman; and Jamali, “Architectural Design for Data Security in Cloud-based Big Data Systems,” Baghdad Sci. J., vol. 21, no. 9, 2024, [Online]. Available: https://bsj.uobaghdad.edu.iq/home/vol21/iss9/5/
P. W. Shor, “Scheme for reducing decoherence in quantum computer memory,” Phys. Rev. A, vol. 52, no. 4, p. R2493, Oct. 1995, doi: 10.1103/PhysRevA.52.R2493.
P. Radanliev, “Artificial intelligence and quantum cryptography,” J. Anal. Sci. Technol., vol. 15, no. 1, pp. 1–17, Dec. 2024, doi: 10.1186/S40543-024-00416-6/FIGURES/3.
A. Jenefa, V. Ebenezer, A. J. Isaac, J. Marshell, P. Pradeepa, and V. Naveen, “Adversarial Attacks on Generative AI Anomaly Detection in the Quantum Era,” 7th Int. Conf. Electron. Commun. Aerosp. Technol. ICECA 2023 - Proc., pp. 1833–1840, 2023, doi: 10.1109/ICECA58529.2023.10395092.
E. Farhi, J. Goldstone, S. Gutmann, and H. Neven, “Quantum Algorithms for Fixed Qubit Architectures,” Mar. 2017, Accessed: Jun. 17, 2025. [Online]. Available: https://arxiv.org/pdf/1703.06199
D. Bhoumik, S. Sur-Kolay, L. K. K. J., and S. S. Iyengar, “Synergy of machine learning with quantum computing and communication,” Oct. 2023, Accessed: Jun. 17, 2025. [Online]. Available: https://arxiv.org/pdf/2310.03434
P. A. Adepoju, B. Austin-Gabriel, A. B. Ige, N. Y. Hussain, O. O. Amoo, and A. I. Afolabi, “Machine learning innovations for enhancing quantum-resistant cryptographic protocols in secure communication,” Open Access Res. J. Multidiscip. Stud., vol. 4, no. 1, pp. 131–139, Sep. 2022, doi: 10.53022/OARJMS.2022.4.1.0075.
R. Renner and R. Wolf, “Quantum Advantage in Cryptography,” AIAA J., vol. 61, no. 5, pp. 1895–1910, Jun. 2022, doi: 10.2514/1.J062267.
D. J. Bernstein, “Introduction to post-quantum cryptography,” Post-Quantum Cryptogr., pp. 1–14, Jan. 2009, doi: 10.1007/978-3-540-88702-7_1.
“Post-Quantum Cryptography | CSRC.” Accessed: Jun. 17, 2025. [Online]. Available: https://csrc.nist.gov/projects/post-quantum-cryptography
A. Jadhav, A. Rasool, and M. Gyanchandani, “Quantum Machine Learning: Scope for real-world problems,” Procedia Comput. Sci., vol. 218, pp. 2612–2625, Jan. 2023, doi: 10.1016/J.PROCS.2023.01.235.
Shoumya Singh and Deepak Kumar, “Enhancing Cyber Security Using Quantum Computing and Artificial Intelligence: A Review,” Int. J. Adv. Res. Sci. Commun. Technol., pp. 4–11, Jun. 2024, doi: 10.48175/IJARSCT-18902.
N. Gisin, G. Ribordy, W. Tittel, and H. Zbinden, “Quantum cryptography,” Rev. Mod. Phys., vol. 74, no. 1, p. 145, Mar. 2002, doi: 10.1103/RevModPhys.74.145.
C. H. Bennett and G. Brassard, “Quantum cryptography: Public key distribution and coin tossing,” Theor. Comput. Sci., vol. 560, no. P1, pp. 7–11, Dec. 2014, doi: 10.1016/J.TCS.2014.05.025.
A. K. Ekert, “Quantum cryptography based on Bell’s theorem,” Phys. Rev. Lett., vol. 67, no. 6, p. 661, Aug. 1991, doi: 10.1103/PhysRevLett.67.661.
V. Scarani, H. Bechmann-Pasquinucci, N. J. Cerf, M. Dusek, N. Lutkenhaus, and M. Peev, “The Security of Practical Quantum Key Distribution,” Rev. Mod. Phys., vol. 81, no. 3, pp. 1301–1350, Feb. 2008, doi: 10.1103/RevModPhys.81.1301.
M. Mafu and M. Senekane, “Security of Quantum Key Distribution Protocols,” Adv. Technol. Quantum Key Distrib., May 2018, doi: 10.5772/INTECHOPEN.74234.
K. Karabo, C. Sekga, C. Kissack, M. Mafu, and F. Petruccione, “A novel quantum key distribution resistant against large-pulse attacks,” IET Quantum Commun., vol. 5, no. 3, pp. 282–290, Sep. 2024, doi: 10.1049/QTC2.12089.
“Artificial Intelligence for the Real World.” Accessed: Jun. 17, 2025. [Online]. Available: https://hbr.org/webinar/2018/02/artificial-intelligence-for-the-real-world
C. Janiesch, P. Zschech, and K. Heinrich, “Machine learning and deep learning,” Electron. Mark., vol. 31, no. 3, pp. 685–695, Apr. 2021, doi: 10.1007/s12525-021-00475-2.
“Artificial Intelligence: A Modern Approach.” Accessed: Jun. 17, 2025. [Online]. Available: https://www.pearson.com/en-us/subject-catalog/p/artificial-intelligence-a-modern-approach/P200000003500/9780137505135?srsltid=AfmBOoqb0YgCTklkTw235M61b3Yqugl95hJVcNJLb3R0pgY1e_SIT7fA
“Pattern Recognition and Machine Learning | SpringerLink.” Accessed: Jun. 17, 2025. [Online]. Available: https://link.springer.com/book/9780387310732
P. Mehta et al., “A high-bias, low-variance introduction to Machine Learning for physicists,” Phys. Rep., vol. 810, pp. 1–124, May 2019, doi: 10.1016/j.physrep.2019.03.001.
“What Is Machine Learning (ML)? | IBM.” Accessed: Jun. 17, 2025. [Online]. Available: https://www.ibm.com/think/topics/machine-learning
B. M. Lake, T. D. Ullman, J. B. Tenenbaum, and S. J. Gershman, “Building Machines That Learn and Think Like People,” Behav. Brain Sci., vol. 40, Apr. 2016, doi: 10.1017/S0140525X16001837.
Y. Lecun, Y. Bengio, and G. Hinton, “Deep learning,” Nature, vol. 521, no. 7553, pp. 436–444, May 2015, doi: 10.1038/NATURE14539;SUBJMETA=117,639,705;KWRD=COMPUTER+SCIENCE,MATHEMATICS+AND+COMPUTING.
M. Schuld and F. Petruccione, “Machine Learning with Quantum Computers,” 2021, doi: 10.1007/978-3-030-83098-4.
K. T. Schütt, S. Chmiela, O. A. von Lilienfeld, A. Tkatchenko, K. Tsuda, and K.-R. Müller, Eds., “Machine Learning Meets Quantum Physics,” vol. 968, 2020, doi: 10.1007/978-3-030-40245-7.
G. Carleo et al., “Machine learning and the physical sciences,” Rev. Mod. Phys., vol. 91, no. 4, Mar. 2019, doi: 10.1103/RevModPhys.91.045002.
C. Jiang, H. Zhang, Y. Ren, Z. Han, K. C. Chen, and L. Hanzo, “Machine Learning Paradigms for Next-Generation Wireless Networks,” IEEE Wirel. Commun., vol. 24, no. 2, pp. 98–105, Apr. 2017, doi: 10.1109/MWC.2016.1500356WC.
K. Merrick and M. Lou Maher, “Motivated reinforcement learning: Curious characters for multiuser games,” Motiv. Reinf. Learn. Curious Characters Multiuser Games, pp. 1–206, 2009, doi: 10.1007/978-3-540-89187-1/COVER.
W. Ma, Z. Liu, Z. A. Kudyshev, A. Boltasseva, W. Cai, and Y. Liu, “Deep learning for the design of photonic structures,” Nat. Photonics 2020 152, vol. 15, no. 2, pp. 77–90, Oct. 2020, doi: 10.1038/s41566-020-0685-y.
M. Kraus, S. Feuerriegel, and A. Oztekin, “Deep learning in business analytics and operations research: Models, applications and managerial implications,” Eur. J. Oper. Res., vol. 281, no. 3, pp. 628–641, Mar. 2020, doi: 10.1016/J.EJOR.2019.09.018.
V. Dhote, M. Sadim, P. Tanna, and A. N. Tiwari, “Machine Learning Strategies in Quantum-Resistant Network Security Protocols,” 3rd IEEE Int. Conf. ICT Bus. Ind. Gov. ICTBIG 2023, 2023, doi: 10.1109/ICTBIG59752.2023.10456284.
B. S. Rocha, J. A. M. Xexeo, and R. H. Torres, “Post-quantum cryptographic algorithm identification using machine learning,” J. Inf. Secur. Cryptogr., vol. 9, no. 1, pp. 1–8, Dec. 2022, doi: 10.17648/JISC.V9I1.81.
G. Yalamuri, P. Honnavalli, and S. Eswaran, “A Review of the Present Cryptographic Arsenal to Deal with Post-Quantum Threats,” Procedia Comput. Sci., vol. 215, pp. 834–845, Jan. 2022, doi: 10.1016/J.PROCS.2022.12.086.
H. Gonaygunta, G. S. Nadella, P. P. Pawar, and D. Kumar, “Study on Empowering Cyber Security by Using Adaptive Machine Learning Methods,” 2024 Syst. Inf. Eng. Des. Symp. SIEDS 2024, pp. 166–171, 2024, doi: 10.1109/SIEDS61124.2024.10534694.
N. Jain et al., “Future proofing network encryption technology with continuous-variable quantum key distribution,” Feb. 2024, Accessed: Jun. 17, 2025. [Online]. Available: https://arxiv.org/pdf/2402.18881
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 50sea

This work is licensed under a Creative Commons Attribution 4.0 International License.




















