Quantum Key Distribution Protocols for Secure Communication
Keywords:
Eavesdropping, Classical Cryptography (CC), Quantum Cryptography (QC), Quantum Key Distribution (QKD), Continuous and Discrete protocolsAbstract
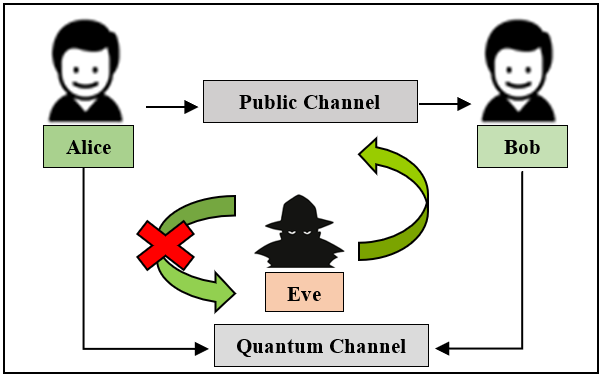
Data protection and information security have been the essence of communication in today's digital era. Authentication and secrecy of secure communication are achieved using key-based cryptographic primitives; the security of which significantly relies upon the underlying computationally complex mathematics. Moreover, these existing cryptographic primitives are considered to be non-deterministic on the basis of the existing computational capabilities. However, the considerable advancements in the development of quantum computers have significantly enhanced parallel computations; thereby, posing a great threat to these existing encryption primitives. Thus, in the future, the physical manifestation of a large successful quantum computer is likely to break all the existing public-key encryption algorithms in no time. This has led to a remarkable surge of interest in propelling quantum mechanics into existence; subsequently, leading cryptographers to research various viable domains to offer quantum-resistant secure communications. Resultantly, quantum cryptography/quantum key distribution has emerged as a futuristic replacement for classical cryptography as it offers unconditionally secure communication along with the inherent detection of any unintended user. Thus, keeping in view the significance of this relatively newer domain of cryptography this research focuses on presenting a consolidated review of the various Quantum Key Distribution (QKD) protocols. A comparative analysis of the working mechanism of the prominent QKD protocols is presented along with an overview of the various emerging trends that have been proposed to optimize the implementational efficiency of the BB84 protocol.
References
X. Tan, “Introduction to Quantum Cryptography,” Theory Pract. Cryptogr. Netw. Secur. Protoc. Technol., Jul. 2013, doi: 10.5772/56092.
A. I. Nurhadi and N. R. Syambas, “Quantum Key Distribution (QKD) Protocols: A Survey,” Proceeding 2018 4th Int. Conf. Wirel. Telemat. ICWT 2018, Nov. 2018, doi: 10.1109/ICWT.2018.8527822.
A. L, “Survey of Most Prominent Quantum Key Distribution Protocols,” Int. Res. J. Eng. Technol., pp. 2395–56, 2016.
M. Javed and K. Aziz, “A survey of quantum key distribution protocols,” Proc. 6th Int. Conf. Front. Inf. Technol. FIT ’09, 2009, doi: 10.1145/1838002.1838046.
M. Moizuddin, J. Winston, and M. Qayyum, “A comprehensive survey: Quantum cryptography,” 2017 2nd Int. Conf. Anti-Cyber Crimes, ICACC 2017, pp. 98–102, Apr. 2017, doi: 10.1109/ANTI-CYBERCRIME.2017.7905271.
V. Padamvathi, B. V. Vardhan, and A. V. N. Krishna, “Quantum Cryptography and Quantum Key Distribution Protocols: A Survey,” Proc. - 6th Int. Adv. Comput. Conf. IACC 2016, pp. 556–562, Aug. 2016, doi: 10.1109/IACC.2016.109.
A. Sharma and A. Kumar, “A Survey on Quantum Key Distribution,” IEEE Int. Conf. Issues Challenges Intell. Comput. Tech. ICICT 2019, Sep. 2019, doi: 10.1109/ICICT46931.2019.8977649.
M. Javed and K. Aziz, “A survey of quantum key distribution protocols,” Proc. 6th Int. Conf. Front. Inf. Technol. FIT ’09, no. May 2014, 2009, doi: 10.1145/1838002.1838046.
Z. Liliana, “Two, three and four dimensional BB84: A comparative analysis based on C# simulation,” 2019 8th Int. Conf. Emerg. Secur. Technol. EST 2019, Jul. 2019, doi: 10.1109/EST.2019.8806204.
I. H. L. Grande et al., “Adaptable transmitter for discrete and continuous variable quantum key distribution,” Opt. Express, Vol. 29, Issue 10, pp. 14815-14827, vol. 29, no. 10, pp. 14815–14827, May 2021, doi: 10.1364/OE.425382.
R. Amiri, P. Wallden, A. Kent, and E. Andersson, “Secure quantum signatures using insecure quantum channels,” Phys. Rev. A, vol. 93, no. 3, pp. 2619–2633, Mar. 2016, doi: 10.1103/PhysRevA.93.032325.
A. A. Abdullah, R. Z. Khalaf, and H. B. Habib, “Modified BB84 Quantum Key Distribution Protocol Using Legendre Symbol,” SCCS 2019 - 2019 2nd Sci. Conf. Comput. Sci., pp. 154–157, Mar. 2019, doi: 10.1109/SCCS.2019.8852619.
S. Sreelatha and G. Murali, “Error correction and detection techniques in quantum cryptography protocol,” 2017 Int. Conf. Energy, Commun. Data Anal. Soft Comput. ICECDS 2017, pp. 3584–3588, Jun. 2018, doi: 10.1109/ICECDS.2017.8390130.
J. Mora, A. Ruiz, W. Amaya, and J. Capmany, “Dispersion supported BB84 quantum key distribution using phase modulated light,” Jan. 2010, doi: 10.48550/arxiv.1001.0547.
Y. C. Jeong, S. W. Ji, C. Hong, H. S. Park, and J. Jang, “Deterministic Secure Quantum Communication on the BB84 System,” Entropy 2020, Vol. 22, Page 1268, vol. 22, no. 11, p. 1268, Nov. 2020, doi: 10.3390/E22111268.
X. Yang, J. Jiao, Y. Shi, and Y. Liu, “Modeling and Security Analysis Method of Quantum Key Distribution Protocol Based on Colored Petri Nets,” Int. Conf. Commun. Technol. Proceedings, ICCT, pp. 283–289, Oct. 2019, doi: 10.1109/ICCT46805.2019.8947177.
V. Usenko, M. Lasota, and R. Filip, “Continuous and discrete-variable quantum key distribution with nonclassical light over noisy channels,” 2016 39th Int. Conf. Telecommun. Signal Process. TSP 2016, pp. 753–756, Nov. 2016, doi: 10.1109/TSP.2016.7760985.
A. Gueddana, M. Attia, and R. Chatta, “Optimized QKD BB84 protocol using quantum dense coding and CNOT gates: feasibility based on probabilistic optical devices,” Nonlinear Opt. Its Appl. VIII; Quantum Opt. III, vol. 9136, no. May 2020, p. 913627, 2014, doi: 10.1117/12.2048809.
Y. Zhang and I. B. Djordjevic, “Generalized PPM-based BB84 QKD protocol,” Int. Conf. Transparent Opt. Networks, 2014, doi: 10.1109/ICTON.2014.6876373.
H. F. Li, L. X. Zhu, K. Wang, and K. Bin Wang, “The improvement of QKD scheme based on BB84 protocol,” Proc. - 2016 Int. Conf. Inf. Syst. Artif. Intell. ISAI 2016, pp. 314–317, Jan. 2017, doi: 10.1109/ISAI.2016.0073.
R. Rostom, B. Bakhache, H. Salami, and A. Awad, “Quantum cryptography and chaos for the transmission of security keys in 802.11 networks,” Proc. Mediterr. Electrotech. Conf. - MELECON, no. April, pp. 350–356, 2014, doi: 10.1109/MELCON.2014.6820559.
J. S. Choe, H. Ko, B. S. Choi, K. J. Kim, and C. J. Youn, “Silica Planar Lightwave Circuit Based Integrated 1 × 4 Polarization Beam Splitter Module for Free-Space BB84 Quantum Key Distribution,” IEEE Photonics J., vol. 10, no. 1, 2018, doi: 10.1109/JPHOT.2017.2788638.
X. Sun, I. B. Djordjevic, and M. A. Neifeld, “Secret Key Rates and Optimization of BB84 and Decoy State Protocols over Time-Varying Free-Space Optical Channels,” IEEE Photonics J., vol. 8, no. 3, 2016, doi: 10.1109/JPHOT.2016.2570000.
Z. Yan et al., “Novel high-speed polarization source for decoy-state BB84 quantum key distribution over free space and satellite links,” J. Light. Technol., vol. 31, no. 9, pp. 1399–1408, 2013, doi: 10.1109/JLT.2013.2249040.
M. Jofre et al., “100 MHz amplitude and polarization modulated optical source for free-space quantum key distribution at 850 nm,” J. Light. Technol., vol. 28, no. 17, pp. 2572–2578, 2010, doi: 10.1109/JLT.2010.2056673.
Y. C. Jeong, Y. S. Kim, and Y. H. Kim, “An experimental comparison of BB84 and SARG04 quantum key distribution protocols,” Laser Phys. Lett., vol. 11, no. 9, pp. 1–5, 2014, doi: 10.1088/1612-2011/11/9/095201.
G. Brassard, N. Lütkenhaus, T. Mor, and B. C. Sanders, “Limitations on practical quantum cryptography,” Phys. Rev. Lett., vol. 85, no. 6, pp. 1330–1333, 2000, doi: 10.1103/PhysRevLett.85.1330.
M. Jofre et al., “100 MHz amplitude and polarization modulated optical source for free-space quantum communications at 850 nm,” Lect. Notes Inst. Comput. Sci. Soc. Telecommun. Eng., vol. 43 LNICST, no. 17, pp. 297–304, 2010, doi: 10.1007/978-3-642-13618-4_22.
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 International Journal of Innovations in Science & Technology

This work is licensed under a Creative Commons Attribution 4.0 International License.




















