Pragmatic Evidence on Android Malware Analysis Techniques: A Systematic Literature Review
DOI:
https://doi.org/10.33411/ijist/2023050101Keywords:
Android Malware, Systematic Literature Review, Static Analysis, Dynamic Analysis , Reverse EngineeringAbstract
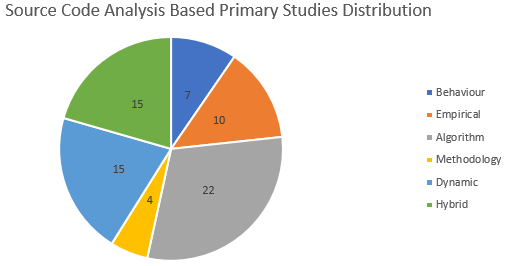
A large number of studies including research articles and surveys on android malware detection and analysis techniques have been presented during the last one and a half decades. The authors proposed different systems and frameworks to identify malware from software applications. However, there is no recent and comprehensive systematic literature review on the detection and analysis of android malware methods, systems, and frameworks. We present a systematic review of literature on android malware detection and analysis techniques and tools by following standard guidelines for Systematic Literature Review methodology from 2010 to 2021. We selected 75 most relevant studies out of 3343 published studies. We found that the prominent malicious datasets are Genome (39%) and Drebin (36%) used by different researchers for the detection of malware. The static, dynamic, and hybrid source code analysis methods are applied by android malware detection techniques. We also identified the limitations and future research directions of existing techniques as research gaps for the community. Based on the pragmatic evidence of this research, we have proposed a hybrid analysis-based multiple feature analysis framework. This framework will not only address the limitations of static and dynamic-based approaches, but it also analyzes evolving android malware datasets using deep neural network and machine learning techniques and improve the accuracy of evolving malware samples.
References
M. Amin, B. Shah, A. Sharif, T. Ali, K. L. Kim, and S. Anwar, “Android malware detection through generative adversarial networks,” Transactions on Emerging Telecommunications Technologies, vol .30, pp. 1-29, issue. e3675, 2019.
P. Faruki, V. Laxmi, A. Bharmal, M. Gaur, and V. Ganmoor, “AndroSimilar: Robust signature for detecting variants of Android malware,” Journal of Information Security and Applications, vol. 22, pp. 66–80, 2015.
S. B. Almin and M. Chatterjee, “A Novel Approach to Detect Android Malware,” Procedia Computer Science, vol. 45, pp. 407–417, 2015.
Z. Ma, H. Ge, Y. Liu, M. Zhao and J. Ma, "A Combination Method for Android Malware Detection Based on Control Flow Graphs and Machine Learning Algorithms," in IEEE Access, vol. 7, pp. 21235-21245, 2019.
M. Fan, J. Liu, X. Luo, K. Chen, Z. Tian, Q. Zheng, and T. Liu, “Android Malware Familial Classification and Representative Sample Selection via Frequent Subgraph Analysis,” IEEE Transactions on Information Forensics and Security, vol. 13, no. 8, pp. 1890–1905, 2018.
H. Papadopoulos, N. Georgiou, C. Eliades, and A. Konstantinidis, “Android malware detection with unbiased confidence guarantees,” Neurocomputing, vol. 280, pp. 3–12, 2018.
P. Palumbo, L. Sayfullina, D. Komashinskiy, E. Eirola, and J. Karhunen, “A pragmatic android malware detection procedure,” Computers & Security, vol. 70, pp. 689–701, 2017.
L. Onwuzurike, E. Mariconti, P. Andriotis, E. D. Cristofaro, G. Ross, and G. Stringhini, “MaMaDroid: Detecting Android Malware by Building Markov Chains of Behavioral Models (Extended Version),” ACM Transactions on Privacy and Security, vol. 22, no. 2, pp. 1–34, Oct. 2019.
C. Bae and S. Shin, “A collaborative approach on host and network level android malware detection,” Security and Communication Networks, vol. 9, no. 18, pp. 5639–5650, 2016.
H. Zhang, S. Luo, Y. Zhang, and L. Pan, "An Efficient Android Malware Detection System Based on Method-Level Behavioral Semantic Analysis," in IEEE Access, vol. 7, pp. 69246-69256, 2019.
L. Onwuzurike, M. Almeida, E. Mariconti, J. Blackburn, G. Stringhini and E. De Cristofaro, "A Family of Droids-Android Malware Detection via Behavioral Modeling: Static vs Dynamic Analysis," 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, pp. 1-10, 2018.
K. A. Talha, D. I. Alper, and C. Aydin, “APK Auditor: Permission-based Android malware detection system,” Digital Investigation, vol. 13, pp. 1–14, 2015.
K. Xu, Y. Li, R. Deng, K. Chen, and J. Xu, "DroidEvolver: Self-Evolving Android Malware Detection System," 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, pp. 47-62, 2019.
D. Li, L. Zhao, Q. Cheng, N. Lu, and W. Shi, “Opcode sequence analysis of Android malware by a convolutional neural network,” Concurrency and Computation: Practice and Experience; e5308, pp. 1-18, Sep. 2019.
A. Narayanan, M. Chandramohan, L. Chen, and Y. Liu, “A multi-view context-aware approach to Android malware detection and malicious code localization,” Empirical Software Engineering, vol. 23, no. 3, pp. 1222–1274, 2018.
A. Narayanan, G. Meng, L. Yang, J. Liu and L. Chen, "Contextual Weisfeiler-Lehman graph kernel for malware detection," 2016 International Joint Conference on Neural Networks (IJCNN), pp. 4701-4708, , 2016,.
A. Arora, S. K. Peddoju and M. Conti, "PermPair: Android Malware Detection Using Permission Pairs," in IEEE Transactions on Information Forensics and Security, vol. 15, pp. 1968-1982, 2020.
Y. Zhou and X. Jiang, “Dissecting Android malware: Characterization and evolution,” in Proc. IEEE Symp. Secur. Privacy, pp. 95–109, , May 2012.
D. Arp, M. Spreitzenbarth, M. Hubner, H. Gascon, and K. Rieck, “DREBIN: Effective and explainable detection of Android malware in your pocket,” in Proc. NDSS, pp. 23–26, 2014.
C. Li, K. Mills, D. Niu, R. Zhu, H. Zhang and H. Kinawi, "Android Malware Detection Based on Factorization Machine," in IEEE Access, vol. 7, pp. 184008-184019, 2019.
K. Xu, Y. Li and R. H. Deng, "ICCDetector: ICC-Based Malware Detection on Android," in IEEE Transactions on Information Forensics and Security, vol. 11, no. 6, pp. 1252-1264, June 2016.
V. Vovk , A. Gammerman , G. Shafer , “Algorithmic Learning in a Random World”, Springer, New York, 2005 .
Y. Zhang, W. Ren, T. Zhu, and Y. Ren, “SaaS: A situational awareness and analysis system for massive android malware detection,” Future Generation Computer Systems, vol. 95, pp. 548–559, 2019.
R. Sartea, A. Farinelli, and M. Murari, “SECUR-AMA: Active Malware Analysis Based on Monte Carlo Tree Search for Android Systems,” Engineering Applications of Artificial Intelligence, vol. 87, p. 103303, Jan. 2020.
P. Feng, J. Ma, C. Sun, X. Xu and Y. Ma, "A Novel Dynamic Android Malware Detection System with Ensemble Learning," in IEEE Access, vol. 6, pp. 30996-31011, 2018.
S. Arshad, M. A. Shah, A. Wahid, A. Mehmood, H. Song and H. Yu, "SAMADroid: A Novel 3-Level Hybrid Malware Detection Model for Android Operating System," in IEEE Access, vol. 6, pp. 4321-4339, 2018.
T. Kabakus and I. A. Dogru, “An in-depth analysis of Android malware using hybrid techniques,” Digital Investigation, vol. 24, pp. 25–33, 2018.
P. Brereton, B. A. Kitchenham, D. Budgen, M. Turner, and M. Khalil, “Lessons from applying the systematic literature review process within the software engineering domain,” Journal of Systems and Software, vol. 80, no. 4, pp. 571–583, 2007.
K. Liu, S. Xu, G. Xu, M. Zhang, D. Sun and H. Liu, "A Review of Android Malware Detection Approaches Based on Machine Learning," in IEEE Access, vol. 8, pp. 124579-124607, 2020.
H.-J. Zhu, Z.-H. You, Z.-X. Zhu, W.-L. Shi, X. Chen, and L. Cheng, “DroidDet: Effective and robust detection of android malware using static analysis along with rotation forest model,” Neurocomputing, vol. 272, pp. 638–646, 2018.
N. Milosevic, A. Dehghantanha, and K.-K. R. Choo, “Machine learning aided Android malware classification,” Comput. Electr. Eng., vol. 61, pp. 266–274, 2017.
F. Alswaina and K. Elleithy, "Android Malware Permission-Based Multi-Class Classification Using Extremely Randomized Trees," in IEEE Access, vol. 6, pp. 76217-76227, 2018.
A. Skovoroda and D. Gamayunov, "Automated Static Analysis and Classification of Android Malware using Permission and API Calls Models," 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, pp. 243-24309, , 2017.
Z. Wang, C. Li, Z. Yuan, Y. Guan, and Y. Xue, “DroidChain: A novel Android malware detection method based on behavior chains,” Pervasive Mob. Comput., vol. 32, pp. 3–14, 2016.
K. Tian, D. Yao, B. G. Ryder, G. Tan and G. Peng, "Detection of Repackaged Android Malware with Code-Heterogeneity Features," in IEEE Transactions on Dependable and Secure Computing, vol. 17, no. 1, pp. 64-77, 1 Jan.-Feb. 2020
T. Lei, Z. Qin, Z. Wang, Q. Li and D. Ye, "EveDroid: Event-Aware Android Malware Detection Against Model Degrading for IoT Devices," in IEEE Internet of Things Journal, vol. 6, no. 4, pp. 6668-6680, Aug. 2019.
H. Gascon, F. Yamaguchi, D. Arp, and K. Rieck, “Structural detection of android malware using embedded call graphs,” in Proceedings of the 2013 ACM workshop on Artificial intelligence and security - AISec ’13, pp. 45-54, , 2013.
K. O. Elish, X. Shu, D. (daphne) Yao, B. G. Ryder, and X. Jiang, “Profiling user-trigger dependence for Android malware detection,” Comput. Secur., vol. 49, pp. 255–273, 2015.
S. Wu, P. Wang, X. Li, and Y. Zhang, “Effective detection of android malware based on the usage of data flow APIs and machine learning,” Inf. Softw. Technol., vol. 75, pp. 17–25, 2016.
J. Chen, M. H. Alalfi, T. R. Dean, and Y. Zou, “Detecting android malware using clone detection,” J. Comput. Sci. Technol., vol. 30, no. 5, pp. 942–956, 2015.
J. Garcia, M. Hammad, and S. Malek, “Lightweight, obfuscation-resilient detection and family identification of android malware,” ACM Trans. Softw. Eng. Methodol., vol. 26, no. 3, pp. 1–29, 2018.
T. Kim, B. Kang, M. Rho, S. Sezer and E. G. Im, "A Multimodal Deep Learning Method for Android Malware Detection Using Various Features," in IEEE Transactions on Information Forensics and Security, vol. 14, no. 3, pp. 773-788, March 2019.
K. Xu, Y. Li, R. H. Deng and K. Chen, "DeepRefiner: Multi-layer Android Malware Detection System Applying Deep Neural Networks," 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, pp. 473-487, 2018.
L. Deshotels, V. Notani, and A. Lakhotia, “DroidLegacy: Automated familial classification of android malware,” in Proceedings of ACM SIGPLAN on Program Protection and Reverse Engineering Workshop 2014 - PPREW’14, pp. 1-12, 2014.
M. Grace, Y. Zhou, Q. Zhang, S. Zou, and X. Jiang, “RiskRanker: Scalable and accurate zero-day android malware detection,” in Proceedings of the 10th international conference on Mobile systems, applications, and services - MobiSys ’12, pp. 281-294, 2012.
G. Meng, Y. Xue, Z. Xu, Y. Liu, J. Zhang, and A. Narayanan, “Semantic modelling of Android malware for effective malware comprehension, detection, and classification,” in Proceedings of the 25th International Symposium on Software Testing and Analysis - ISSTA, pp 306–317, 2016.
F. Shen, J. D. Vecchio, A. Mohaisen, S. Y. Ko and L. Ziarek, "Android Malware Detection Using Complex-Flows," 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, pp. 2430-2437, 2017.
G. Suarez-Tangil, S. K. Dash, M. Ahmadi, J. Kinder, G. Giacinto, and L. Cavallaro, “DroidSieve: Fast and accurate classification of obfuscated android malware,” in Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, pp 309-320, 2017.
S. Zou, J. Zhang, and X. Lin, “An effective behavior-based Android malware detection system,” Secur. Commun. Netw., vol. 8, no. 12, pp. 2079–2089, 2015.
X. Xiao, X. Xiao, Y. Jiang, X. Liu, and R. Ye, “Identifying Android malware with system call co-occurrence matrices,” Trans. emerg. telecommun. technol., vol. 27, no. 5, pp. 675–684, 2016.
L. Gheorghe et al., “Smart malware detection on Android,” Secur. Commun. Netw., vol. 8, no. 18, pp. 4254–4272, 2015.
X. Xiao, S. Zhang, F. Mercaldo, G. Hu, and A. K. Sangaiah, “Android malware detection based on system call sequences and LSTM,” Multimed. Tools Appl., vol. 78, no. 4, pp. 3979–3999, 2019.
P. Vinod and P. Viswalakshmi, “Empirical evaluation of a system call-based android malware detector,” Arab. J. Sci. Eng., vol. 43, no. 12, pp. 6751–6770, 2018.
V. M. Afonso, M. F. de Amorim, A. R. A. Grégio, G. B. Junquera, and P. L. de Geus, “Identifying Android malware using dynamically obtained features,” J. comput. virol. hacking tech., vol. 11, no. 1, pp. 9–17, 2015.
Burguera, U. Zurutuza, and S. Nadjm-Tehrani, “Crowdroid: Behavior-based malware detection system for Android,” in Proceedings of the 1st ACM workshop on Security and privacy in smartphones and mobile devices - SPSM ’11. pp. 15-26, 2011.
H. Cai, N. Meng, B. Ryder and D. Yao, "DroidCat: Effective Android Malware Detection and Categorization via App-Level Profiling," in IEEE Transactions on Information Forensics and Security, vol. 14, no. 6, pp. 1455-1470, June 2019.
S. K. Dash et al., "DroidScribe: Classifying Android Malware Based on Runtime Behavior," 2016 IEEE Security and Privacy Workshops (SPW), San Jose, CA, pp. 252-261, 2016,
A.sShabtai, U. Kanonov, Y. Elovici, C. Glezer, and Y. Weiss, “‘Andromaly’: a behavioral malware detection framework for android devices,” J. Intell. Inf. Syst., vol. 38, no. 1, pp. 161–190, 2012.
P. Teufl, M. Ferk, A. Fitzek, D. Hein, S. Kraxberger, and C. Orthacker, “Malware detection by applying knowledge discovery processes to application metadata on the Android Market (Google Play): Android Malware Detection based on Metadata Analysis,” Secur. Commun. Netw., vol. 9, no. 5, pp. 389–419, 2016.
A. Saracino, D. Sgandurra, G. Dini and F. Martinelli, "MADAM: Effective and Efficient Behavior-based Android Malware Detection and Prevention," in IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 1, pp. 83-97, 1 Jan.-Feb. 2018
J. Lin, X. Zhao, and H. Li, “Target: Category-based android malware detection revisited,” in Proceedings of the Australasian Computer Science Week Multiconference on - ACSW ’17, pp. 1-9, 2017.
J. Yu, Q. Huang, and C. Yian, “DroidScreening: a practical framework for real-world Android malware analysis: A practical framework for real-world Android malware analysis,” Secur. Commun. Netw., vol. 9, no. 11, pp. 1435–1449, 2016.
J.-W. Jang, J. Yun, A. Mohaisen, J. Woo, and H. K. Kim, “Detecting and classifying method based on similarity matching of Android malware behavior with profile,” Springerplus, vol. 5, no. 1, p. 273, 2016.
A. Altaher, “An improved Android malware detection scheme based on an evolving hybrid neuro-fuzzy classifier (EHNFC) and permission-based features,” Neural Comput. Appl., vol. 28, no. 12, pp. 4147–4157, 2017.
A. Pektaş and T. Acarman, “Learning to detect Android malware via opcode sequences,” Neurocomputing, vol. 396, pp. 599–608, 2020.
Z.-U. Rehman et al., “Machine learning-assisted signature and heuristic-based detection of malwares in Android devices,” Comput. Electr. Eng., vol. 69, pp. 828–841, 2018.
A. I. Ali-Gombe, B. Saltaformaggio, J. “ram” Ramanujam, D. Xu, and G. G. Richard III, “Toward a more dependable hybrid analysis of android malware using aspect-oriented programming,” Comput. Secur., vol. 73, pp. 235–248, 2018.
S. Y. Yerima and S. Sezer, "DroidFusion: A Novel Multilevel Classifier Fusion Approach for Android Malware Detection," in IEEE Transactions on Cybernetics, vol. 49, no. 2, pp. 453-466, Feb. 2019
J. H. Abawajy and A. Kelarev, "Iterative Classifier Fusion System for the Detection of Android Malware," in IEEE Transactions on Big Data, vol. 5, no. 3, pp. 282-292, 1 Sept. 2019
S. Chen, M. Xue, Z. Tang, L. Xu, and H. Zhu, “StormDroid: A streaminglized machine learning-based system for detecting android malware,” in Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security,pp. 377-388, 2016.
E. B. Karbab, M. Debbabi, A. Derhab, and D. Mouheb, “MalDozer: Automatic framework for android malware detection using deep learning,” Digit. investig., vol. 24, pp. 48–59, 2018.
A. Narayanan, M. Chandramohan, L. Chen and Y. Liu, "Context-Aware, Adaptive, and Scalable Android Malware Detection Through Online Learning," in IEEE Transactions on Emerging Topics in Computational Intelligence, vol. 1, no. 3, pp. 157-175, June 2017.
L. Zhang, V. L. L. Thing, and Y. Cheng, “A scalable and extensible framework for android malware detection and family attribution,” Comput. Secur., vol. 80, pp. 120–133, 2019.
M. Nauman, T. A. Tanveer, S. Khan, and T. A. Syed, “Deep neural architectures for large scale android malware analysis,” Cluster Comput., vol. 21, no. 1, pp. 569–588, 2018.
A. Martín, H. D. Menéndez, and D. Camacho, “MOCDroid: multi-objective evolutionary classifier for Android malware detection,” Soft Comput., vol. 21, no. 24, pp. 7405–7415, 2017.
Y. Pan, X. Ge, C. Fang and Y. Fan, "A Systematic Literature Review of Android Malware Detection Using Static Analysis," in IEEE Access, vol. 8, pp. 116363-116379, 2020.
T. Cover, "Estimation by the nearest neighbor rule," in IEEE Transactions on Information Theory, vol. 14, no. 1, pp. 50-55, January 1968.
Hosmer Jr DW, Lemeshow S, Sturdivant RX. Logistic regression for matched case–control studies. Applied Logistic Regression, Third Edition:, pp. 243–268, 1989.
Crammer K, Kulesza A, Dredze M. Adaptive regularization of weight vectors. In Advances in Neural Information Processing Systems, Columbia, Canada, pp. 414–422, , 2009.
A. Veloso, W. Meira and M. J. Zaki, "Lazy Associative Classification," Sixth International Conference on Data Mining (ICDM'06), pp. 645-654, 2006.
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 50SEA

This work is licensed under a Creative Commons Attribution 4.0 International License.




















