Investigating Threats to ICS and SCADA Systems Via Honeypot Data Analysis and SIEM
Keywords:
ICS, SCADA, OT, Honeypot, Critical Infrastructure ProtectionAbstract
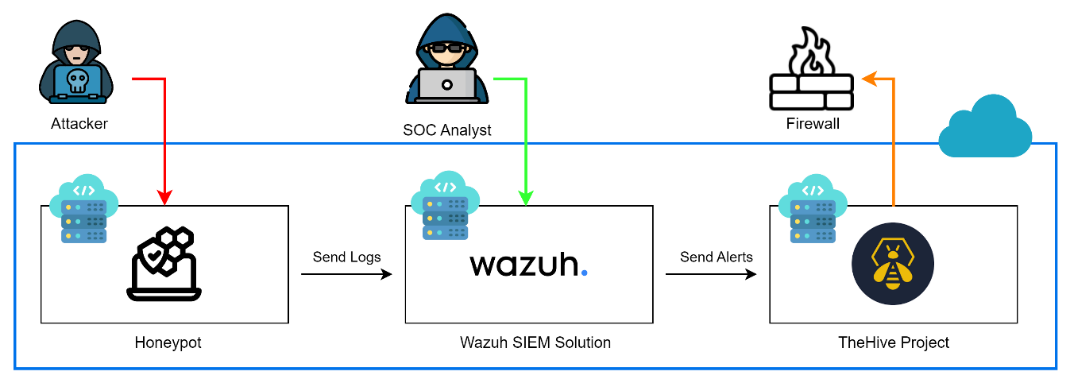
Supervisory Control and Data Acquisition (SCADA) and Industrial Control Systems (ICS) are crucial for managing essential infrastructure, but their exposure to the internet has made them vulnerable to cyber threats, which can lead to significant consequences. This study presents an innovative approach to investigating cyber threats to SCADA and ICS systems by combining open-source honeypot deployment, log analysis, and integration with open-source SIEM solutions to enhance threat detection capabilities and incident response. A Conpot honeypot was deployed in a containerized environment on a cloud platform and exposed to the internet to collect real-world threat data, which was then analyzed by the Wazuh SIEM solution and integrated with TheHive for security orchestration and automated response. The analysis of the honeypot logs and SIEM alerts revealed various types of attacks, including brute force login attempts, reconnaissance and vulnerability scanning, and unauthorized access attempts, originating from multiple countries and targeting different industrial protocols. The integration with TheHive enabled the creation of playbooks for automating response actions, such as blocking malicious IP addresses or isolating infected systems. The study demonstrates the effectiveness of this combined approach using open-source tools in protecting critical infrastructure and enhancing cybersecurity posture for SCADA and ICS systems.
References
M. Mesbah, M. S. Elsayed, A. D. Jurcut, and M. Azer, “Analysis of ICS and SCADA Systems Attacks Using Honeypots,” Futur. Internet 2023, Vol. 15, Page 241, vol. 15, no. 7, p. 241, Jul. 2023, doi: 10.3390/FI15070241.
A. Nechibvute and H. D. Mafukidze, “Integration of SCADA and Industrial IoT: Opportunities and Challenges,” IETE Tech. Rev., May 2024, doi: 10.1080/02564602.2023.2246426.
A. Ara, “Security in Supervisory Control and Data Acquisition (SCADA) based Industrial Control Systems: Challenges and Solutions,” IOP Conf. Ser. Earth Environ. Sci., vol. 1026, no. 1, p. 012030, May 2022, doi: 10.1088/1755-1315/1026/1/012030.
“Know Your Enemy: Revealing the Security Tools, Tactics, and Motives of the Blackhat Community: Honeynet Project: 9780201746136: Amazon.com: Books.” Accessed: May 06, 2024. [Online]. Available: https://www.amazon.com/Know-Your-Enemy-Revealing-Community/dp/0201746131
“World Wide ICS Honeypots: A Study into the Deployment of Conpot Honeypots.” Accessed: May 06, 2024. [Online]. Available: https://www.researchgate.net/publication/358166067_World_Wide_ICS_Honeypots_A_Study_into_the_Deployment_of_Conpot_Honeypots
S. Chamotra, J. S. Bhatia, R. Kamal, and A. K. Ramani, “Deployment of a low interaction honeypot in an organizational private network,” Proc. 2011 Int. Conf. Emerg. Trends Networks Comput. Commun. ETNCC2011, pp. 130–135, 2011, doi: 10.1109/ETNCC.2011.5958501.
P. Radoglou-Grammatikis et al., “TRUSTY: A solution for threat hunting using data analysis in critical infrastructures,” Proc. 2021 IEEE Int. Conf. Cyber Secur. Resilience, CSR 2021, pp. 485–490, Jul. 2021, doi: 10.1109/CSR51186.2021.9527936.
A. Jicha, M. Patton, and H. Chen, “SCADA honeypots: An in-depth analysis of Conpot,” IEEE Int. Conf. Intell. Secur. Informatics Cybersecurity Big Data, ISI 2016, pp. 196–198, Nov. 2016, doi: 10.1109/ISI.2016.7745468.
A. M. Nasution, M. Zarlis, and S. Suherman, “Analysis and Implementation of Honeyd as a Low-Interaction Honeypot in Enhancing Security Systems,” Randwick Int. Soc. Sci. J., vol. 2, no. 1, pp. 124–135, Jan. 2021, doi: 10.47175/RISSJ.V2I1.209.
J. Franco, A. Aris, B. Canberk, and A. S. Uluagac, “A Survey of Honeypots and Honeynets for Internet of Things, Industrial Internet of Things, and Cyber-Physical Systems,” IEEE Commun. Surv. Tutorials, vol. 23, no. 4, pp. 2351–2383, 2021, doi: 10.1109/COMST.2021.3106669.
S. Sharma and A. Kaul, “A survey on Intrusion Detection Systems and Honeypot based proactive security mechanisms in VANETs and VANET Cloud,” Veh. Commun., vol. 12, pp. 138–164, Apr. 2018, doi: 10.1016/J.VEHCOM.2018.04.005.
J. Uitto, S. Rauti, S. Laurén, and V. Leppänen, “A Survey on Anti-honeypot and Anti-introspection Methods,” Adv. Intell. Syst. Comput., vol. 570, pp. 125–134, 2017, doi: 10.1007/978-3-319-56538-5_13.
J. Cao, W. Li, J. Li, and B. Li, “DiPot: A Distributed Industrial Honeypot System,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 10699 LNCS, pp. 300–309, 2018, doi: 10.1007/978-3-319-73830-7_30.
E. López-Morales et al., “HoneyPLC: A Next-Generation Honeypot for Industrial Control Systems,” Proc. ACM Conf. Comput. Commun. Secur., pp. 279–291, Oct. 2020, doi: 10.1145/3372297.3423356.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 50SEA

This work is licensed under a Creative Commons Attribution 4.0 International License.




















