Artificial Intelligence-Augmented Intrusion Detection Systems for Advanced Threat Taxonomy in Cloud Computing Environments
Keywords:
SaaS, Malware, CIDS, ClassificationAbstract
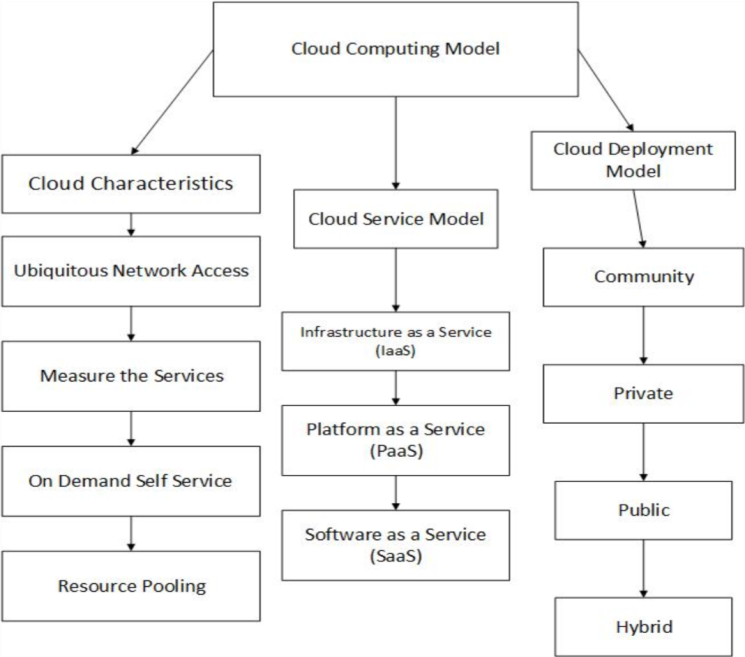
Over the past few decades, cyber-attacks have emerged as a grave form of criminal activity and a subject of intense scholarly and policy debate. The rapid proliferation of cloud computing services— particularly Software as a Service (SaaS)—has further motivated research to classify security threats and their corresponding countermeasures. Scholars have increasingly focused on the risks, vulnerabilities, and malicious intrusions inherent in such environments, with particular emphasis on MITM (MITM) attacks and their mitigation and detection mechanisms. Host-based virtual software has demonstrated considerable efficacy in detecting malware within localized environments. Building on this foundation, the present study classifies Man-in-the-Middle (MITM) attacks in SaaS platforms through the deployment of Cloud-based Intrusion Detection Systems (CIDS). Our investigation concentrates specifically on attacks that target cloud hosts deployed within SaaS infrastructures. The proposed methodology incorporates the roles of the source cloud, destination cloud, and directional flow of the attack vector. In this context, the cloud ecosystem is understood as a dynamic environment where any participating entity, equipped with sufficient technical expertise, may both launch and be subjected to sophisticated intrusions. Accordingly, adaptive CIDS monitoring architectures are essential to safeguard communication between cloud actors. Moreover, CIDS frameworks furnish modular components capable of aggregating alerts, conducting analysis, and notifying administrators of potential breaches. To further illustrate the threat landscape, we present a statistical analysis of vulnerabilities most frequently exploited in MITM scenarios. This classification not only highlights the evolving tactics of adversaries but also equips readers with a structured understanding of MITM attacks, thereby fostering greater familiarity with contemporary cloud security challenges.
References
F. Nisar, M. Amin, M. Touseef Irshad, H. Hadi, N. Ahmad, and M. Ladan,“Machine learning-based spreading factor optimization in LoRaWAN networks,” Front. Comput. Sci, vol. 7, 2025, doi: https://doi.org/10.3389/fcomp.2025.1666262.
G. Idex, “Cisco Global Cloud Index-Forecast and Methodology-2016-2021,” Cisco, San Jose, Ca, USA, white Pap., 2018, [Online]. Available: https://www.scribd.com/document/370618138/Cisco-Global-Cloud-Index-Forecast-and-Methodology-2016-2021
T. S. and G. Byrd, “The Internet of Everything,” Computer (Long. Beach. Calif)., 2014, [Online]. Available: https://www.researchgate.net/publication/264231862_The_Internet_of_Everything
D. E. Culler, “THE ONCE AND FUTURE INTERNET OF EVERYTHING,” GetMobile Mob. Comput. Commun., vol. 20, no. 3, pp. 5–11, Jan. 2017, doi: 10.1145/3036699.3036701.
W. Shi and S. Dustdar, “The Promise of Edge Computing,” Computer (Long. Beach. Calif)., vol. 49, no. 5, pp. 78–81, May 2016, doi: 10.1109/MC.2016.145.
F. Nisar, M. Amin, M. Touseef Irshad, H. Hadi, N. Ahmad, and M. Ladan, “XGBoost-Driven Adaptive Spreading Factor Allocation for Energy-Efficient LoRaWAN Networks,” Front. Commun. Networks, vol. 6, p. 1665262, doi: 10.3389/FRCMN.2025.1665262.
D. Boneh and M. Franklin, “Identity-Based Encryption from the Weil Pairing,” https://doi.org/10.1137/S0097539701398521, vol. 32, no. 3, pp. 586–615, Feb. 2012, doi: 10.1137/S0097539701398521.
K. Upreti, B. K. Vargis, R. Jain, and M. Upadhyaya, “Analytical study on performance of cloud computing with respect to data security,” Proc. - 5th Int. Conf. Intell. Comput. Control Syst. ICICCS 2021, pp. 96–101, May 2021, doi: 10.1109/ICICCS51141.2021.9432268.
G. A. Shiraz M, “Mobile Cloud Computing: Critical Analysis of Application Deployment in Virtual Machines,” Int. Conf. Comput. Netw. (ICICN 2012), 2012, [Online]. Available: https://www.researchgate.net/publication/264888478_Mobile_Cloud_Computing_Critical_Analysis_of_Application_Deployment_in_Virtual_Machines
Q. S. and D. L.-J. M. R. Baharon, “A New Lightweight Homomorphic Encryption Scheme for Mobile Cloud Computing,” 2015 IEEE Int. Conf. Comput. Inf. Technol., pp. 618–625, 2015, doi: 10.1109/CIT/IUCC/DASC/PICOM.2015.88.
C. Wang, W. Li, Y. Li, and X. Xu, “A Ciphertext-Policy Attribute-Based Encryption Scheme Supporting Keyword Search Function,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 8300 LNCS, pp. 377–386, 2013, doi: 10.1007/978-3-319-03584-0_28.
J. K. L. Xu Yang, Xinyi Huang a, “Efficient handover authentication with user anonymity and untraceability for Mobile Cloud Computing,” Futur. Gener. Comput. Syst., vol. 62, pp. 190–195, 2016, doi: https://doi.org/10.1016/j.future.2015.09.028.
K. Zhang, “Energy-Efficient Offloading for Mobile Edge Computing in 5G Heterogeneous Networks,” IEEE Access, vol. 4, pp. 5896–5907, 2016, doi: 10.1109/ACCESS.2016.2597169.
A. Shamir, “Identity-Based Cryptosystems and Signature Schemes,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), pp. 47–53, 2000, [Online]. Available: https://link.springer.com/chapter/10.1007/3-540-39568-7_5
B. Waters, “Ciphertext-Policy Attribute-Based Encryption: An Expressive, Efficient, and Provably Secure Realization,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), 2011, doi: https://doi.org/10.1007/978-3-642-19379-8_4.
A. Lewko, A. Sanais, and B. Waters, “Revocation systems with very small private keys,” Proc. - IEEE Symp. Secur. Priv., pp. 273–285, 2010, doi: 10.1109/SP.2010.23.
G. B. & M. S. Matt Blaze, “Divertible protocols and atomic proxy cryptography,” Adv. Cryptol. — EUROCRYPT’98, pp. 127–144, 2006, doi: https://doi.org/10.1007/BFb0054122.
Y. D. Anca Ivan, “Proxy Cryptography Revisited,” Netw. Distrib. Syst. Secur. Sympt SanDaiego CA, 2003, [Online]. Available: https://www.ndss-symposium.org/wp-content/uploads/2017/09/Proxy-Cryptography-Revisited-Anca-Ivan.pdf
J. Weng, R. H. Deng, X. Ding, C. K. Chu, and J. Lai, “Conditional proxy re-encryption secure against chosen-ciphertext attack,” Proc. 4th Int. Symp. ACM Symp. Information, Comput. Commun. Secur. ASIACCS’09, pp. 322–332, 2009, doi: 10.1145/1533057.1533100.
T. ElGamal, “A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms,” Lect. Notes Comput. Sci., 1985, doi: https://doi.org/10.1007/3-540-39568-7_2.
J. A. González-Martínez, E. G.-S. , Miguel L. Bote-Lorenzo, and R. Cano-Parra, “Cloud computing and education: A state-of-the-art survey,” Comput. Educ., vol. 80, pp. 132–151, 2015, doi: https://doi.org/10.1016/j.compedu.2014.08.017.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 50sea

This work is licensed under a Creative Commons Attribution 4.0 International License.




















