AI-Sentinel: A Novel AI-Powered Intrusion Detection Approach Against Cyber Threats for In-Vehicular Communication Systems
Keywords:
Intrusion detection, IDS, IVN, In-vehicular communication, ML, DL, Cyber-attacks, CAN bus, Federated Learning (FL), Intelligent connected vehicles (ICVs)Abstract
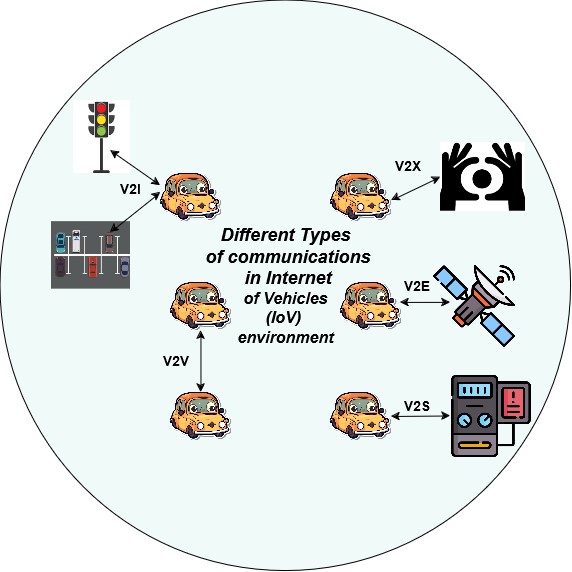
The emergence of revolutionizing technologies such as Artificial Intelligence and the Internet of Things, and their integration into the automotive industry has brought innovations and made the lives of common people easier and complacent. Leveraging the advanced intelligent services provided by the connected and autonomous vehicles the driving experience is much more convenient and effortless. The CAN (Controller Area Network) protocol is the most commonly deployed protocol in in-vehicular communications in the ICVs (intelligent connected vehicles) environment due to its efficiency and speed. However, it lacks basic security mechanisms like encryption and authentication making it vulnerable to various cyber threats. In this article, we have presented a novel, robust, cutting-edge AI-based Intrusion detection system for detecting various seen and unseen cyber-attacks in in-vehicular networks to ensure security. Two main models deployed in the proposed framework are RNN for dealing with temporal dependencies in the CAN traffic and LightGBM for efficient feature extraction. The experimental results show that the hybrid of these two models performs better in terms of various evaluation metrics, with its accuracy being 94% in classifying the CAN traffic into normal and different attack classes. A comparison with the existing state-of-the-art approaches shows that our proposed approach is more robust and secure, with it being deployed in a Federated Learning FL environment.
References
G. Dimitrakopoulos and P. Demestichas, “Intelligent transportation systems: Systems based on cognitive networking principles and management functionality,” IEEE Veh. Technol. Mag., vol. 5, no. 1, pp. 77–84, Mar. 2010, doi: 10.1109/MVT.2009.935537.
M. S. Korium, M. Saber, A. Beattie, A. Narayanan, S. Sahoo, and P. H. J. Nardelli, “Intrusion detection system for cyberattacks in the Internet of Vehicles environment,” Ad Hoc Networks, vol. 153, p. 103330, Feb. 2024, doi: 10.1016/J.ADHOC.2023.103330.
“Intelligent Transportation System(ITS): Concept, Challenge and Opportunity | IEEE Conference Publication | IEEE Xplore.” Accessed: Jun. 17, 2025. [Online]. Available: https://ieeexplore.ieee.org/document/7980336
G. Abdelkader, K. Elgazzar, and A. Khamis, “Connected Vehicles: Technology Review, State of the Art, Challenges and Opportunities,” Sensors 2021, Vol. 21, Page 7712, vol. 21, no. 22, p. 7712, Nov. 2021, doi: 10.3390/S21227712.
K. N, V. Ravi, and V. Sowmya, “Unsupervised intrusion detection system for in-vehicle communication networks,” J. Saf. Sci. Resil., vol. 5, no. 2, pp. 119–129, Jun. 2024, doi: 10.1016/J.JNLSSR.2023.12.004.
“Exploring Controller Area Networks | USENIX.” Accessed: Jun. 17, 2025. [Online]. Available: https://www.usenix.org/publications/login/dec15/foster
M. D. Pesé, J. W. Schauer, J. Li, and K. G. Shin, “S2-CAN: Sufficiently Secure Controller Area Network,” ACM Int. Conf. Proceeding Ser., pp. 425–438, Dec. 2021, doi: 10.1145/3485832.3485883;PAGE:STRING:ARTICLE/CHAPTER.
A. Barati, A. Movaghar, and M. Sabaei, “Energy Efficient and High Speed Error Control Scheme for Real Time Wireless Sensor Networks,” Int. J. Distrib. Sens. Networks, vol. 2014, 2014, doi: 10.1155/2014/698125.
M. Althunayyan, A. Javed, and O. Rana, “A robust multi-stage intrusion detection system for in-vehicle network security using hierarchical federated learning,” Veh. Commun., vol. 49, p. 100837, Oct. 2024, doi: 10.1016/J.VEHCOM.2024.100837.
S. Checkoway et al., “Comprehensive Experimental Analyses of Automotive Attack Surfaces”.
C. Young, J. Zambreno, H. Olufowobi, and G. Bloom, “Survey of automotive controller area network intrusion detection systems,” IEEE Des. Test, vol. 36, no. 6, pp. 48–55, Dec. 2019, doi: 10.1109/MDAT.2019.2899062.
C. W. Axelrod, “INTEGRATING IN-VEHICLE, VEHICLE-TO-VEHICLE, AND INTELLIGENT ROADWAY SYSTEMS,” Int. J. Des. Nat. Ecodynamics, vol. 13, no. 1, pp. 23–38, Jan. 2018, doi: 10.2495/DNE-V13-N1-23-38.
S. Garg, K. Kaur, G. Kaddoum, S. H. Ahmed, and D. N. K. Jayakody, “SDN-Based Secure and Privacy-Preserving Scheme for Vehicular Networks: A 5G Perspective,” IEEE Trans. Veh. Technol., vol. 68, no. 9, pp. 8421–8434, Sep. 2019, doi: 10.1109/TVT.2019.2917776.
J. Ondruš, E. Kolla, P. Vertaľ, and Ž. Šarić, “How Do Autonomous Cars Work?,” Transp. Res. Procedia, vol. 44, pp. 226–233, Jan. 2020, doi: 10.1016/J.TRPRO.2020.02.049.
C. F. Cheng, G. Srivastava, J. C. W. Lin, and Y. C. Lin, “Fault-Tolerance Mechanisms for Software-Defined Internet of Vehicles,” IEEE Trans. Intell. Transp. Syst., vol. 22, no. 6, pp. 3859–3868, Jun. 2021, doi: 10.1109/TITS.2020.3043729.
R. Khan, P. Kumar, D. N. K. Jayakody, and M. Liyanage, “A Survey on Security and Privacy of 5G Technologies: Potential Solutions, Recent Advancements, and Future Directions,” IEEE Commun. Surv. Tutorials, vol. 22, no. 1, pp. 196–248, Jan. 2020, doi: 10.1109/COMST.2019.2933899.
K. Koscher et al., “Experimental security analysis of a modern automobile,” Proc. - IEEE Symp. Secur. Priv., pp. 447–462, 2010, doi: 10.1109/SP.2010.34.
“Jeep hackers at it again, this time taking control of steering and braking systems | The Verge.” Accessed: Jun. 17, 2025. [Online]. Available: https://www.theverge.com/2016/8/2/12353186/car-hack-jeep-cherokee-vulnerability-miller-valasek
“OwnStar Device Can Remotely Locate, Unlock, and Start GM Cars | Threatpost.” Accessed: Jun. 17, 2025. [Online]. Available: https://threatpost.com/ownstar-device-can-remotely-locate-unlock-and-start-gm-cars/114042/
“New Vehicle Security Research by KeenLab: Experimental Security Assessment of BMW Cars | Keen Security Lab Blog.” Accessed: Jun. 17, 2025. [Online]. Available: https://keenlab.tencent.com/en/2018/05/22/New-CarHacking-Research-by-KeenLab-Experimental-Security-Assessment-of-BMW-Cars/
“Tencent Keen Security Lab: Experimental Security Assessment on Lexus Cars | Keen Security Lab Blog.” Accessed: Jun. 17, 2025. [Online]. Available: https://keenlab.tencent.com/en/2020/03/30/Tencent-Keen-Security-Lab-Experimental-Security-Assessment-on-Lexus-Cars/
T. Alladi, V. Kohli, V. Chamola, and F. R. Yu, “A deep learning based misbehavior classification scheme for intrusion detection in cooperative intelligent transportation systems,” Digit. Commun. Networks, vol. 9, no. 5, pp. 1113–1122, Oct. 2023, doi: 10.1016/J.DCAN.2022.06.018.
E. Gelenbe, B. C. Gül, and M. Nakıp, “DISFIDA: Distributed Self-Supervised Federated Intrusion Detection Algorithm with online learning for health Internet of Things and Internet of Vehicles,” Internet of Things, vol. 28, p. 101340, Dec. 2024, doi: 10.1016/J.IOT.2024.101340.
Y. K. Saheed and J. E. Chukwuere, “XAIEnsembleTL-IoV: A new eXplainable Artificial Intelligence ensemble transfer learning for zero-day botnet attack detection in the Internet of Vehicles,” Results Eng., vol. 24, Dec. 2024, doi: 10.1016/J.RINENG.2024.103171.
J. Yang, J. Hu, and T. Yu, “Federated AI-Enabled In-Vehicle Network Intrusion Detection for Internet of Vehicles,” Electron. 2022, Vol. 11, Page 3658, vol. 11, no. 22, p. 3658, Nov. 2022, doi: 10.3390/ELECTRONICS11223658.
A. Khadka, P. Karypidis, A. Lytos, and G. Efstathopoulos, “A benchmarking framework for cyber-attacks on autonomous vehicles,” Transp. Res. Procedia, vol. 52, pp. 323–330, Jan. 2021, doi: 10.1016/J.TRPRO.2021.01.038.
P. Dakic et al., “Intrusion detection using metaheuristic optimization within IoT/IIoT systems and software of autonomous vehicles,” Sci. Rep., vol. 14, no. 1, p. 22884, Dec. 2024, doi: 10.1038/S41598-024-73932-5;SUBJMETA=1041,1042,117,639,705;KWRD=APPLIED+MATHEMATICS,COMPUTATIONAL+SCIENCE,COMPUTER+SCIENCE.
S. . Satheeskumaran, Y. Zhang, V. E. Balas, T. Hong, and D. Pelusi, “Intelligent computing for sustainable development : first International Conference, ICICSD 2023, Hyderabad, India, August 25-26, 2023, revised selected papers. Part I,” 2024.
T. Alladi, V. Kohli, V. Chamola, F. R. Yu, and M. Guizani, “Artificial Intelligence (AI)-Empowered Intrusion Detection Architecture for the Internet of Vehicles,” IEEE Wirel. Commun., vol. 28, no. 3, pp. 144–149, Jun. 2021, doi: 10.1109/MWC.001.2000428.
S. Samarakoon, M. Bennis, W. Saad, and M. Debbah, “Distributed Federated Learning for Ultra-Reliable Low-Latency Vehicular Communications,” IEEE Trans. Commun., vol. 68, no. 2, pp. 1146–1159, Feb. 2020, doi: 10.1109/TCOMM.2019.2956472.
Di. M. Manias and A. Shami, “Making a Case for Federated Learning in the Internet of Vehicles and Intelligent Transportation Systems,” IEEE Netw., vol. 35, no. 3, pp. 88–94, May 2021, doi: 10.1109/MNET.011.2000552.
T. N. Hoang and D. Kim, “Detecting in-vehicle intrusion via semi-supervised learning-based convolutional adversarial autoencoders,” Veh. Commun., vol. 38, p. 100520, Dec. 2022, doi: 10.1016/J.VEHCOM.2022.100520.
H. Lee, S. H. Jeong, and H. K. Kim, “OTIDS: A novel intrusion detection system for in-vehicle network by using remote frame,” Proc. - 2017 15th Annu. Conf. Privacy, Secur. Trust. PST 2017, pp. 57–66, Sep. 2018, doi: 10.1109/PST.2017.00017.
J. Zhang and K. B. Letaief, “Mobile Edge Intelligence and Computing for the Internet of Vehicles,” Proc. IEEE, vol. 108, no. 2, pp. 246–261, Feb. 2020, doi: 10.1109/JPROC.2019.2947490.
H. Brendan McMahan, E. Moore, D. Ramage, S. Hampson, and B. Agüera y Arcas, “Communication-Efficient Learning of Deep Networks from Decentralized Data,” Proc. 20th Int. Conf. Artif. Intell. Stat. AISTATS 2017, Feb. 2016, Accessed: Jun. 17, 2025. [Online]. Available: https://arxiv.org/pdf/1602.05629
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 50sea

This work is licensed under a Creative Commons Attribution 4.0 International License.




















