Machine Learning with Data Balancing Technique for IoT Attack and Anomalies Detection
DOI:
https://doi.org/10.33411/ijist/2022040218Keywords:
IoT Attacks, IoT Anomalies, Random Under Sampling, Machine LearningAbstract
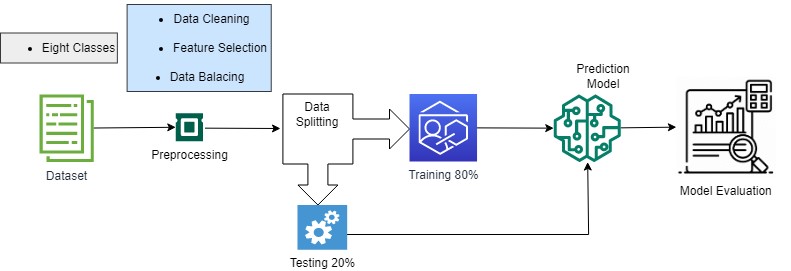
Nowadays the significant concern in IoT infrastructure is anomaly and attack detection from IoT devices. Due to the advanced technology, the attack issues are increasing gradually. There are many attacks like Data Type Probing, Denial of Service, Malicious Operation, Malicious Control, Spying, Scan, and Wrong Setup that cause the failure of the IoT-based system. In this paper, several machine learning model performances have been compared to effectively predict the attack and anomaly. The performance of the models is compared with evaluation matrices (Accuracy) and confusion matrix for the final version of the effective model. Most of the recent studies performed experiments on an unbalanced dataset; that is clear that the model will be biased for such a dataset, so we completed the experiments in two forms, unbalanced and balanced data samples. For the unbalanced dataset, we have achieved the highest accuracy of 98.0% with Generalized Linear Model as well as with Random Forest; Unbalanced dataset means most of the chances are that model is biased, so we have also performed the experiments with Random Under Sampling Technique (Balancing Data) and achieved the highest accuracy of 94.3% with Generalized Linear Model. The confusion matrix in this study also supports the performance of the Generalized Linear Model.
References
M. Burhan, R. A. Rehman, B. Khan, and B. S. Kim, “IoT elements, layered architectures and security issues: A comprehensive survey,” Sensors (Switzerland), vol. 18, no. 9, pp. 1–37, 2018, doi: 10.3390/s18092796.
M. A. Rahman and A. T. Asyhari, “The emergence of internet of things (Iot): Connecting anything, anywhere,” Computers, vol. 8, no. 2, pp. 8–11, 2019, doi: 10.3390/computers8020040.
D. Sehrawat and N. S. Gill, “Smart sensors: Analysis of different types of IoT sensors,” Proc. Int. Conf. Trends Electron. Informatics, ICOEI 2019, no. Icoei, pp. 523–528, 2019, doi: 10.1109/ICOEI.2019.8862778.
T. M. Tukade and R. M. Banakar, “Data Transfer Protocols in IoT-An Overview,” Int. J. Pure Appl. Math., vol. 118, no. 16, pp. 121–138, 2018.
X. Liu, Y. Liu, A. Liu, and L. T. Yang, “Defending ON-OFF attacks using light probing messages in smart sensors for industrial communication systems,” IEEE Trans. Ind. Informatics, vol. 14, no. 9, pp. 3801–3811, 2018, doi: 10.1109/TII.2018.2836150.
S. M. Tahsien, H. Karimipour, and P. Spachos, “Machine learning based solutions for security of Internet of Things (IoT): A survey,” J. Netw. Comput. Appl., vol. 161, no. March, 2020, doi: 10.1016/j.jnca.2020.102630.
M. Uma and G. Padmavathi, “A survey on various cyber attacks and their classification,” Int. J. Netw. Secur., vol. 15, no. 5, pp. 390–396, 2013.
A. S.-S. [ETEBMS-2016] and undefined 2016, “Applications of artificial intelligence & associated technologies,” test.globalinfocloud.com, Accessed: May 18, 2022.
I. El Naqa and M. J. Murphy, “Machine Learning in Radiation Oncology,” Mach. Learn. Radiat. Oncol., pp. 3–11, 2015, doi: 10.1007/978-3-319-18305-3.
M. Abdullahi et al., “Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review,” Electron., vol. 11, no. 2, pp. 1–27, 2022, doi: 10.3390/electronics11020198.
S. H. Haji and S. Y. Ameen, “Attack and Anomaly Detection in IoT Networks using Machine Learning Techniques: A Review,” Asian J. Res. Comput. Sci., no. June, pp. 30–46, 2021, doi: 10.9734/ajrcos/2021/v9i230218.
Q. A. Al-Haija, M. Krichen, and W. A. Elhaija, “Machine-Learning-Based Darknet Traffic Detection System for IoT Applications,” Electron., vol. 11, no. 4, 2022, doi: 10.3390/electronics11040556.
I. Mukherjee, N. K. Sahu, and S. K. Sahana, “Simulation and Modeling for Anomaly Detection in IoT Network Using Machine Learning,” Int. J. Wirel. Inf. Networks, no. 0123456789, 2022, doi: 10.1007/s10776-021-00542-7.
L. Xiao, X. Wan, X. Lu, Y. Zhang, and D. Wu, “IoT Security Techniques Based on Machine Learning: How Do IoT Devices Use AI to Enhance Security?,” IEEE Signal Process. Mag., vol. 35, no. 5, pp. 41–49, 2018, doi: 10.1109/MSP.2018.2825478.
B. Li, Y. Feng, Z. Xiong, W. Yang, and G. Liu, “Research on AI security enhanced encryption algorithm of autonomous IoT systems,” Inf. Sci. (Ny)., vol. 575, pp. 379–398, 2021, doi: 10.1016/j.ins.2021.06.016.
A. K. Sarica and P. Angin, “Explainable security in SDN-based IoT networks,” Sensors (Switzerland), vol. 20, no. 24, pp. 1–30, 2020, doi: 10.3390/s20247326.
T. K. Dang, C. D. M. Pham, and T. L. P. Nguyen, “A pragmatic elliptic curve cryptography-based extension for energy-efficient device-to-device communications in smart cities,” Sustain. Cities Soc., vol. 56, p. 102097, 2020, doi: 10.1016/j.scs.2020.102097.
D. Jyoti, R. Kamalraj, G. Ramesh, K. S. Sankaran, S. Sharma, and S. Khasim, “Microprocessors and Microsystems A machine learning based IoT for providing an intrusion detection system for security,” Microprocess. Microsyst., vol. 82, no. November 2020, p. 103741, 2021, doi: 10.1016/j.micpro.2020.103741.
J. A. Bland, M. D. Petty, T. S. Whitaker, K. P. Maxwell, and W. A. Cantrell, “Machine Learning Cyberattack and Defense Strategies,” Comput. Secur., vol. 92, p. 101738, 2020, doi: 10.1016/j.cose.2020.101738.
S. Aldhaheri, D. Alghazzawi, L. Cheng, A. Barnawi, and B. A. Alzahrani, “Artificial Immune Systems approaches to secure the internet of things: A systematic review of the literature and recommendations for future research,” J. Netw. Comput. Appl., vol. 157, p. 102537, 2020, doi: 10.1016/j.jnca.2020.102537.
Z. Ahmad et al., “Anomaly detection using deep neural network for iot architecture,” Appl. Sci., vol. 11, no. 15, 2021, doi: 10.3390/app11157050.
M. Shafiq, Z. Tian, Y. Sun, X. Du, and M. Guizani, “Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city,” Futur. Gener. Comput. Syst., vol. 107, pp. 433–442, 2020, doi: 10.1016/j.future.2020.02.017.
J. Roldán, J. Boubeta-Puig, J. Luis Martínez, and G. Ortiz, “Integrating complex event processing and machine learning: An intelligent architecture for detecting IoT security attacks,” Expert Syst. Appl., vol. 149, 2020, doi: 10.1016/j.eswa.2020.113251.
Published
How to Cite
Issue
Section
License
Copyright (c) 2022 50SEA

This work is licensed under a Creative Commons Attribution 4.0 International License.




















