Unsupervised Detection of Credential Stuffing and Account Takeover Attempts through User Behavioral Biometrics in Web Applications
Keywords:
Unsupervised Learning, Anomaly Detection, Behavioral Biometrics, Credential Stuffing, Account Takeover, Risk-Based Authentication, Web Security, User Behavior AnalyticsAbstract
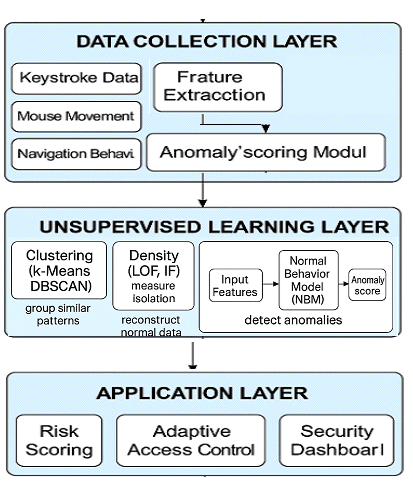
Credential stuffing and account takeover (ATO) attacks can still be stated as being one of the most ongoing risks of contemporary web applications, as they use reused credentials and defy traditional authentication procedures. Conventional supervised detection approaches rely on labeled attack data (which is frequently non-existent or incomplete) in the real world. In this paper, a credential stuffing and ATO adversarial behavior multi-layer detector is suggested through modeling user behavioral biometrics based on the web-session navigation patterns and chaining information during the login procedure. The framework combines Isolation Forest and Local Outlier Factor to train a normal behavioral distribution and detect deviations that suggest abnormal use of the accounts, which are either automated or reports of hacked accounts. Analysis of three different datasets RBA, MSNBC, and CERT Insider Threat, has shown that the framework is highly detection sensitive with an ROC-AUC of up to 0.936 and an F1-score of 0.842 in login-level anomaly detection, and cross-domain generalization on enterprise data. The findings validate the practicability of unsupervised behavioral modelling as a lightweight defense mechanism that is scalable and resistant to credential abuse. The suggested solution ensures that labelling is reduced, the privacy of users is maintained, and a scalable basic infrastructure is provided to accommodate the adaptive and risk-centric authentication models in massive web applications.
References
A. Tariq, “Tracking for Good: Finding Behavioral Biometrics on the Web using Static Taint Analysis,” Univ. Waterloo, 2025, [Online]. Available: https://uwspace.uwaterloo.ca/items/a27d11b8-354e-487b-88ff-69e269eabb6d
M. M. Kamol, M. S. Siddiky, F. Anwar, A. M. Khan, and A. Salam, “Credentials Stuffing Attack Prevention Using Machine Learning,” 2024 27th Int. Conf. Comput. Inf. Technol. ICCIT 2024 - Proc., pp. 2899–2904, 2024, doi: 10.1109/ICCIT64611.2024.11022023.
A. Bara, “Finding Behavioural Biometrics Scripts on the Web Using Dynamic Taint Analysis,” Univ. Waterloo, 2025, [Online]. Available: https://uwspace.uwaterloo.ca/items/c77e83a2-c624-40f4-85f5-51e3f539ab07
A. Riyaz Fathima and A. Saravanan, “An approach to cloud user access control using behavioral biometric-based authentication and continuous monitoring,” Int. J. Adv. Technol. Eng. Explor., vol. 11, no. 119, pp. 1469–1496, 2024, doi: 10.19101/IJATEE.2024.111100516.
A. Barkworth, R. Tabassum, and A. Habibi Lashkari, “Detecting IMAP Credential Stuffing Bots Using Behavioural Biometrics,” ACM Int. Conf. Proceeding Ser., pp. 7–15, Dec. 2022, doi: 10.1145/3586102.3586104;JOURNAL:JOURNAL:ACMOTHERCONFERENCES;CTYPE:STRING:BOOK.
V. Arora and R. Kanji, “Modelling and Predicting User Behaviour”.
F. A. Idialu, “Leveraging Zero Trust Architectures and Blockchain Protocols to Prevent Credential Stuffing and Lateral Fraud Attacks in Enterprise Systems,” Int. J. Comput. Appl. Technol. Res., vol. 14, no. 8, 2025, doi: 10.7753/IJCATR1408.1002.
P. Teimoory, “Towards robust security in smart payment systems: challenges and solutions,” Smart Cities Reg. Dev. J., vol. 9, no. 3, pp. 29–38, 2025, doi: https://scrd.eu/index.php/scrd/article/view/627.
S. Sadeghpour, “Machine Learning-Based Defences Against Advanced ‘Session-Replay’ Web Bots,” York, vol. 3, 2024, [Online]. Available: https://yorkspace.library.yorku.ca/items/6ac36ce5-a90c-49d7-85b4-e470695aca53
M. Hämäläinen, “Analysis of artificial intelligence in cybersecurity identity and access management : potential for disruptive innovation,” LUT Univ., 2024, [Online]. Available: https://lutpub.lut.fi/handle/10024/168740
S. Kumar, “Biometric systems security and privacy issues,” Leveraging Comput. Vis. to Biometric Appl., pp. 68–91, Oct. 2024, doi: 10.1201/9781032614663-4/BIOMETRIC-SYSTEMS-SECURITY-PRIVACY-ISSUES-SUNIL-KUMAR.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 50sea

This work is licensed under a Creative Commons Attribution 4.0 International License.




















