Enhancing Security in Mobile Cloud Computing: An Analysis of Authentication Protocols and Innovation
Keywords:
Cloud computing, Mobile computing, Virtualization, Trust, Mobile Cloud Computing, Privacy, Security, AuthenticationAbstract
Introduction/Importance of Study: Cloud computing is a model facilitating ubiquitous, convenient, and on-demand network access to a shared pool of computing resources, offering flexibility, reliability, and scalability .
Objective: This study investigates authentication mechanisms in Mobile Cloud Computing (MCC) to enhance security and address emerging challenges.
Novelty statement: Our research contributes novel insights into authentication protocols in MCC, offering solutions to security issues not previously addressed.
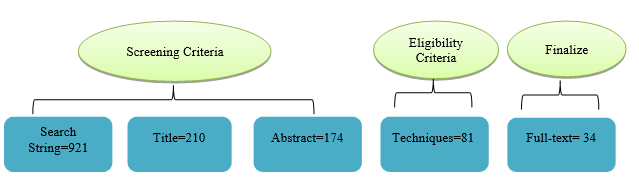
Material and Method: The study analyzed various authentication mechanisms in MCC using NIST evaluation criteria, considering their alignment with security needs and resource constraints.
Result and Discussion: Our findings underscore the importance of selecting authentication mechanisms that balance security and performance in MCC environments, highlighting the need for ongoing innovation in security measures.
Concluding Remarks: The study emphasises the significance of robust authentication protocols tailored to MCC's unique security requirements for ensuring data integrity and privacy.
References
H. Tabrizchi and M. Kuchaki Rafsanjani, “A survey on security challenges in cloud computing: issues, threats, and solutions,” J. Supercomput., vol. 76, no. 12, pp. 9493–9532, Dec. 2020, doi: 10.1007/S11227-020-03213-1/METRICS.
A. A. Ahmed, K. Wendy, M. N. Kabir, and A. S. Sadiq, “Dynamic Reciprocal Authentication Protocol for Mobile Cloud Computing,” IEEE Syst. J., vol. 15, no. 1, pp. 727–737, Mar. 2021, doi: 10.1109/JSYST.2020.3012986.
A. S. AlAhmad, H. Kahtan, Y. I. Alzoubi, O. Ali, and A. Jaradat, “Mobile cloud computing models security issues: A systematic review,” J. Netw. Comput. Appl., vol. 190, p. 103152, Sep. 2021, doi: 10.1016/J.JNCA.2021.103152.
A. A. Ikram, A. R. Javed, M. Rizwan, R. Abid, J. Crichigno, and G. Srivastava, “Mobile Cloud Computing Framework for Securing Data,” 2021 44th Int. Conf. Telecommun. Signal Process. TSP 2021, pp. 309–315, Jul. 2021, doi: 10.1109/TSP52935.2021.9522673.
H. Ullah Khan, F. Ali, S. Nazir, of Swabi, and P. Correspondence Habib Ullah Khan, “Systematic analysis of software development in cloud computing perceptions,” J. Softw. Evol. Process, vol. 36, no. 2, p. e2485, Feb. 2024, doi: 10.1002/SMR.2485.
A. Aliyu et al., “Mobile Cloud Computing: Taxonomy and Challenges,” J. Comput. Networks Commun., vol. 2020, 2020, doi: 10.1155/2020/2547921.
S. Shamshirband, M. Fathi, A. T. Chronopoulos, A. Montieri, F. Palumbo, and A. Pescapè, “Computational intelligence intrusion detection techniques in mobile cloud computing environments: Review, taxonomy, and open research issues,” J. Inf. Secur. Appl., vol. 55, p. 102582, Dec. 2020, doi: 10.1016/J.JISA.2020.102582.
S. A. Bello et al., “Cloud computing in construction industry: Use cases, benefits and challenges,” Autom. Constr., vol. 122, p. 103441, Feb. 2021, doi: 10.1016/J.AUTCON.2020.103441.
Z. A. Almusaylim and N. Jhanjhi, “Comprehensive Review: Privacy Protection of User in Location-Aware Services of Mobile Cloud Computing,” Wirel. Pers. Commun., vol. 111, no. 1, pp. 541–564, Mar. 2020, doi: 10.1007/S11277-019-06872-3/METRICS.
M. Ibtihal, E. O. Driss, and N. Hassan, “Homomorphic Encryption as a Service for Outsourced Images in Mobile Cloud Computing Environment,” https://services.igi-global.com/resolvedoi/resolve.aspx?doi=10.4018/IJCAC.2017040103, vol. 7, no. 2, pp. 27–40, Jan. 1AD, doi: 10.4018/IJCAC.2017040103.
L. Pallavi, B. T. Rao, and A. Jagan, “Mobility Management Challenges and Solutions in Mobile Cloud Computing System for Next Generation Networks,” Int. J. Adv. Comput. Sci. Appl., vol. 11, no. 3, pp. 177–192, 2020, doi: 10.14569/IJACSA.2020.0110322.
M. Shabbir et al., “Enhancing Security of Health Information Using Modular Encryption Standard in Mobile Cloud Computing,” IEEE Access, vol. 9, pp. 8820–8834, 2021, doi: 10.1109/ACCESS.2021.3049564.
D. G. M. Sunil Kumar, B. Siddardha, A. Hitesh Reddy, Ch.V.Sainath Reddy, Abdul Bari Shaik, “APPLYING THE MODULAR ENCRYPTION STANDARD TO MOBILE CLOUD COMPUTING TO IMPROVE THE SAFETY OF HEALTH DATA,” J Pharm Negat Results, pp. 1911–1917, doi: 10.47750/pnr.2022.13.s08.231.
G. Verma, “Blockchain-based privacy preservation framework for healthcare data in cloud environment,” J. Exp. Theor. Artif. Intell., vol. 36, no. 1, pp. 147–160, Jan. 2024, doi: 10.1080/0952813X.2022.2135611.
L. Shi, J. Liu, V. Fonseca, P. Walker, A. Kalsekar, and M. Pawaskar, “Correlation between adherence rates measured by MEMS and self-reported questionnaires: A meta-analysis,” Health Qual. Life Outcomes, vol. 8, no. 1, pp. 1–7, Sep. 2010, doi: 10.1186/1477-7525-8-99/FIGURES/2.
B. B. Sathish and P. Venkataram, “A Dynamic Authentication Scheme for Mobile Transactions,” Int. J. Netw. Secur., vol. 8, no. 1, pp. 59–74, 2009.
H. Witte, C. Rathgeb, and C. Busch, “Context-aware mobile biometric authentication based on support vector machines,” Proc. - 2013 4th Int. Conf. Emerg. Secur. Technol. EST 2013, pp. 29–32, 2013, doi: 10.1109/EST.2013.38.
G. Dandachi, B. El Hassan, and A. El Husseini, “A novel identification/verification model using smartphone’s sensors and user behavior,” 2013 2nd Int. Conf. Adv. Biomed. Eng. ICABME 2013, pp. 235–238, Oct. 2013, doi: 10.1109/ICABME.2013.6648891.
L. X. Hung et al., “Activity-based security scheme for ubiquitous environments,” Conf. Proc. IEEE Int. Performance, Comput. Commun. Conf., pp. 475–481, 2008, doi: 10.1109/PCCC.2008.4745102.
A. Corradi, R. Montanari, and D. Tibaldi, “Context-based access control management in ubiquitous environments,” Proc. - Third IEEE Int. Symp. Netw. Comput. Appl. NCA 2004, pp. 253–260, 2004, doi: 10.1109/NCA.2004.1347784.
D. J. S. Raj, “Improved Response Time and Energy Management for Mobile Cloud Computing Using Computational Offloading,” J. ISMAC, vol. 2, no. 1, pp. 38–49, Mar. 2020, doi: 10.36548/JISMAC.2020.1.004.
M. A. Ferrag, L. Maglaras, A. Derhab, and H. Janicke, “Authentication schemes for smart mobile devices: threat models, countermeasures, and open research issues,” Telecommun. Syst. 2019 732, vol. 73, no. 2, pp. 317–348, Sep. 2019, doi: 10.1007/S11235-019-00612-5.
A. Fregly, J. Harvey, B. S. Kaliski, and S. Sheth, “Merkle Tree Ladder Mode: Reducing the Size Impact of NIST PQC Signature Algorithms in Practice,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 13871 LNCS, pp. 415–441, 2023, doi: 10.1007/978-3-031-30872-7_16/COVER.
K. Cao, Y. Liu, G. Meng, and Q. Sun, “An Overview on Edge Computing Research,” IEEE Access, vol. 8, pp. 85714–85728, 2020, doi: 10.1109/ACCESS.2020.2991734.
M. Papaioannou, G. Mantas, A. Essop, P. Cox, I. E. Otung, and J. Rodriguez, “Risk-Based Adaptive User Authentication for Mobile Passenger ID Devices for Land/Sea Border Control,” IEEE Int. Work. Comput. Aided Model. Des. Commun. Links Networks, CAMAD, vol. 2021-October, 2021, doi: 10.1109/CAMAD52502.2021.9617802.
L. A. Gordon, M. P. Loeb, and L. Zhou, “Integrating cost–benefit analysis into the NIST Cybersecurity Framework via the Gordon–Loeb Model,” J. Cybersecurity, vol. 6, no. 1, Jan. 2020, doi: 10.1093/CYBSEC/TYAA005.
N. Mouha and C. Celi, “Extending NIST’s CAVP testing of cryptographic hash function implementations,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 12006 LNCS, pp. 129–145, 2020, doi: 10.1007/978-3-030-40186-3_7/COVER.
S. Boboň, “Analysis of NIST FIPS 140-2 security certificates.” 2021.
M. Fagan et al., “IoT Device Cybersecurity Guidance for the Federal Government: IoT Device Cybersecurity Requirement Catalog,” Nov. 2021, doi: 10.6028/NIST.SP.800-213A.
“NIST roadmap toward criteria for threshold schemes for cryptographic primitives.” Accessed: Mar. 28, 2024. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/ir/2020/NIST.IR.8214A.pdf
S. F. Aghili, M. Sedaghat, D. Singelée, and M. Gupta, “MLS-ABAC: Efficient Multi-Level Security Attribute-Based Access Control scheme,” Futur. Gener. Comput. Syst., vol. 131, pp. 75–90, Jun. 2022, doi: 10.1016/J.FUTURE.2022.01.003.
M. S. Sheikh, J. Liang, and W. Wang, “Security and Privacy in Vehicular Ad Hoc Network and Vehicle Cloud Computing: A Survey,” Wirel. Commun. Mob. Comput., vol. 2020, 2020, doi: 10.1155/2020/5129620.
K. Benzekki, A. El Fergougui, and A. E. B. Elalaoui, “A Context-Aware Authentication System for Mobile Cloud Computing,” Procedia Comput. Sci., vol. 127, pp. 379–387, Jan. 2018, doi: 10.1016/J.PROCS.2018.01.135.
S. Abidin, A. Swami, E. Ramirez-Asís, J. Alvarado-Tolentino, R. K. Maurya, and N. Hussain, “Quantum cryptography technique: A way to improve security challenges in mobile cloud computing (MCC),” Mater. Today Proc., vol. 51, pp. 508–514, Jan. 2022, doi: 10.1016/J.MATPR.2021.05.593.
M. J. O. Saarinen, “WiP: Applicability of ISO Standard Side-Channel Leakage Tests to NIST Post-Quantum Cryptography,” Proc. 2022 IEEE Int. Symp. Hardw. Oriented Secur. Trust. HOST 2022, pp. 69–72, 2022, doi: 10.1109/HOST54066.2022.9839849.
T. Hai et al., “An archetypal determination of mobile cloud computing for emergency applications using decision tree algorithm,” J. Cloud Comput., vol. 12, no. 1, pp. 1–15, Dec. 2023, doi: 10.1186/S13677-023-00449-Z/TABLES/8.
M. A. Arshed, S. Mumtaz, O. Riaz, W. Sharif, and S. Abdullah, “A Deep Learning Framework for Multi Drug Side Effects Prediction with Drug Chemical Substructure,” Int. J. Innov. Sci. Technol., vol. 4, no. 1, pp. 19–31, Jan. 2022, Accessed: Feb. 13, 2024. [Online]. Available: https://journal.50sea.com/index.php/IJIST/article/view/140
M. A. Arshed, H. Ghassan, M. Hussain, M. Hassan, A. Kanwal, and R. Fayyaz, “A Light Weight Deep Learning Model for Real World Plant Identification,” 2022 2nd Int. Conf. Distrib. Comput. High Perform. Comput. DCHPC 2022, pp. 40–45, 2022, doi: 10.1109/DCHPC55044.2022.9731841.
A. Shahzad, M. A. Arshed, F. Liaquat, M. Tanveer, M. Hussain, and R. Alamdar, “Pneumonia Classification from Chest X-ray Images Using Pre-Trained Network Architectures,” VAWKUM Trans. Comput. Sci., vol. 10, no. 2, pp. 34–44, Dec. 2022, doi: 10.21015/VTCS.V10I2.1271.
M. Mubeen, M. A. Arshed, and H. A. Rehman, “DeepFireNet - A Light-Weight Neural Network for Fire-Smoke Detection,” Commun. Comput. Inf. Sci., vol. 1616 CCIS, pp. 171–181, 2022, doi: 10.1007/978-3-031-10525-8_14/COVER.
M. A. Arshed, S. Mumtaz, M. Hussain, R. Alamdar, M. T. Hassan, and M. Tanveer, “DeepFinancial Model for Exchange Rate Impacts Prediction of Political and Financial Statements,” 3rd IEEE Int. Conf. Artif. Intell. ICAI 2023, pp. 13–19, 2023, doi: 10.1109/ICAI58407.2023.10136658.
“Tomato Disease Classification using Fine-Tuned Convolutional Neural Network,” vol. 4, no. 1, pp. 123–134, 2022.
M. A. Arshed, A. Shahzad, K. Arshad, D. Karim, S. Mumtaz, and M. Tanveer, “Multiclass Brain Tumor Classification from MRI Images using Pre-Trained CNN Model,” VFAST Trans. Softw. Eng., vol. 10, no. 4, pp. 22–28, Nov. 2022, doi: 10.21015/VTSE.V10I4.1182.
“Machine Learning with Data Balancing Technique for IoT Attack and Anomalies Detection | International Journal of Innovations in Science & Technology.” Accessed: Feb. 07, 2024. [Online]. Available: https://journal.50sea.com/index.php/IJIST/article/view/277
H. A. Arshad, M. Hussain, A. Amin, and M. A. Arshed, “Impact of Artificial Intelligence in COVID-19 Pandemic: A Comprehensive Review,” 2022 2nd Int. Conf. Distrib. Comput. High Perform. Comput. DCHPC 2022, pp. 66–73, 2022, doi: 10.1109/DCHPC55044.2022.9732091.
M. A. Arshed, W. Qureshi, M. Rumaan, M. T. Ubaid, A. Qudoos, and M. U. G. Khan, “Comparison of Machine Learning Classifiers for Breast Cancer Diagnosis,” 4th Int. Conf. Innov. Comput. ICIC 2021, 2021, doi: 10.1109/ICIC53490.2021.9692926.
M. A. Arshed and F. Riaz, “Machine Learning for High Risk Cardiovascular Patient Identification 1,” J. Distrib. Comput. Syst., vol. 4, no. 2, pp. 34–39, 2021.
M. Hussain, A. Shahzad, F. Liaquat, M. A. Arshed, S. Mansoor, and Z. Akram, “Performance Analysis of Machine Learning Algorithms for Early Prognosis of Cardiac Vascular Disease,” Tech. J., vol. 28, no. 02, pp. 31–41, Jun. 2023, Accessed: Feb. 13, 2024. [Online]. Available: https://tj.uettaxila.edu.pk/index.php/technical-journal/article/view/1778
H. Alasmary and M. Tanveer, “ESCI-AKA: Enabling Secure Communication in an IoT-Enabled Smart Home Environment Using Authenticated Key Agreement Framework,” Math. 2023, Vol. 11, Page 3450, vol. 11, no. 16, p. 3450, Aug. 2023, doi: 10.3390/MATH11163450.
M. Tanveer, A. U. Khan, M. Ahmad, T. N. Nguyen, and A. A. A. El-Latif, “Resource-Efficient Authenticated Data Sharing Mechanism for Smart Wearable Systems,” IEEE Trans. Netw. Sci. Eng., vol. 10, no. 5, pp. 2525–2536, Sep. 2023, doi: 10.1109/TNSE.2022.3203927.
K. Ishaq and S. Fareed, “Mitigation Techniques for Cyber Attacks: A Systematic Mapping Study,” Aug. 2023, Accessed: Mar. 28, 2024. [Online]. Available: https://arxiv.org/abs/2308.13587v1
K. Ishaq and F. Khan, “Block Chain in the IoT industry: A Systematic Literature Review,” Aug. 2023, Accessed: Mar. 28, 2024. [Online]. Available: https://arxiv.org/abs/2308.13613v1
N. A. Nawaz et al., “A comprehensive review of security threats and solutions for the online social networks industry,” PeerJ Comput. Sci., vol. 9, p. e1143, Jan. 2023, doi: 10.7717/PEERJ-CS.1143.
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 50SEA

This work is licensed under a Creative Commons Attribution 4.0 International License.




















