Evolving Security Landscape of the Internet of Things: Assessing Advantages and Challenges
Keywords:
Internet of Things, Network Security, Confidentiality, AuthenticationAbstract
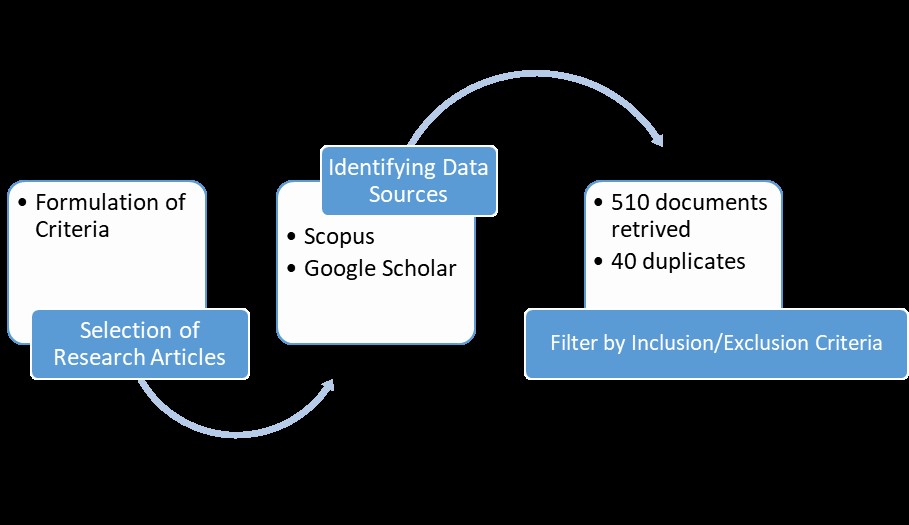
In light of the widespread integration of the Internet of Things (IoT), it is crucial for organizations to prioritize their attention towards establishing resilient system security. The presence of any vulnerability within a system has the potential to result in system failure or a cyberattack, hence causing significant repercussions on a wide scale. This encompasses a set of measures and protocols designed to safeguard against cyber threats that especially exploit vulnerabilities in physically interconnected IoT devices. The security teams responsible for managing IoT security are currently facing a range of challenges, including but not limited to inventory management, operational complexities, variety in IoT devices, ownership concerns, increasing data volumes, and emerging threats. This review provides a critical analysis of the existing body of research pertaining to the subject of security in the context of the IoT. The focus is mostly on the present state of affairs, practical implementations, and the issues that are associated with this domain. Moreover, it delves into the prospective prospects and opportunities that are anticipated in this particular domain. Lately, there has been a noticeable surge in interest among scholars hailing from diverse academic disciplines and geographical locations, all focusing on the improvement of internet network security. The assurance of data integrity, confidentiality, authentication, and authorization is imperative in light of the substantial volume of data that traverses network devices. Nevertheless, the field of IoT security exhibits significant potential for further development. The IoT has become a popular technology paradigm that facilitates the integration of diverse objects and systems. Yet, the extensive use of the IoT has generated apprehensions regarding security, specifically pertaining to the safeguarding of data and the integrity of networks.
References
A. A. G.-E. Ahmed and A. A. G.-E. Ahmed, “Benefits and Challenges of Internet of Things for Telecommunication Networks,” Telecommun. Networks - Trends Dev., Feb. 2019, doi: 10.5772/INTECHOPEN.81891.
F. T. Jaigirdar, B. Tan, C. Rudolph, and C. Bain, “Security-Aware Provenance for Transparency in IoT Data Propagation,” IEEE Access, vol. 11, pp. 55677–55691, 2023, doi: 10.1109/ACCESS.2023.3280928.
H. Ning, H. Liu, and L. T. Yang, “Cyberentity security in the internet of things,” Computer (Long. Beach. Calif)., vol. 46, no. 4, pp. 46–53, 2013, doi: 10.1109/MC.2013.74.
A. Bogdanov et al., “PRESENT: An ultra-lightweight block cipher,” Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), vol. 4727 LNCS, pp. 450–466, 2007, doi: 10.1007/978-3-540-74735-2_31.
F. Thabit, O. Can, A. O. Aljahdali, G. H. Al-Gaphari, and H. A. Alkhzaimi, “Cryptography Algorithms for Enhancing IoT Security,” Internet of Things (Netherlands), vol. 22, Jul. 2023, doi: 10.1016/j.iot.2023.100759.
F. A. Alaba, M. Othman, I. A. T. Hashem, and F. Alotaibi, “Internet of Things security: A survey,” J. Netw. Comput. Appl., vol. 88, pp. 10–28, Jun. 2017, doi: 10.1016/J.JNCA.2017.04.002.
U. Farooq, N. Tariq, M. Asim, T. Baker, and A. Al-Shamma’a, “Machine learning and the Internet of Things security: Solutions and open challenges,” J. Parallel Distrib. Comput., vol. 162, pp. 89–104, Apr. 2022, doi: 10.1016/J.JPDC.2022.01.015.
P. Peris-Lopez, Ed., “2015 International Workshop on Secure Internet of Things, SIoT 2015, Vienna, Austria, September 21-25, 2015,” SIoT, 2015, Accessed: Oct. 09, 2023. [Online]. Available: http://dblp.uni-trier.de/db/conf/siot/siot2015.html
W. Detres, M. M. Chowdhury, and N. Rifat, “IoT Security and Privacy,” IEEE Int. Conf. Electro Inf. Technol., vol. 2022-May, pp. 498–503, 2022, doi: 10.1109/EIT53891.2022.9813933.
E. Farooq, S. A. Khan, and W. H. Butt, “Covert network analysis to detect key players using correlation and social network analysis,” ACM Int. Conf. Proceeding Ser., Mar. 2017, doi: 10.1145/3018896.3025142.
P. Mugariri, H. Abdullah, M. García-Torres, B. D. Parameshchari, and K. N. Abdul Sattar, “Promoting Information Privacy Protection Awareness for Internet of Things (IoT),” Mob. Inf. Syst., vol. 2022, 2022, doi: 10.1155/2022/4247651.
S. Volpert, P. Eichhammer, F. Held, T. Huffert, H. P. Reiser, and J. Domaschka, “The view on systems monitoring and its requirements from future Cloud-to-Thing applications and infrastructures,” Futur. Gener. Comput. Syst., vol. 141, pp. 243–257, Apr. 2023, doi: 10.1016/J.FUTURE.2022.11.024.
A. Boudguiga, A. Olivereau, and N. Oualha, “Server assisted key establishment for WSN: A mikey-ticket approach,” Proc. - 12th IEEE Int. Conf. Trust. Secur. Priv. Comput. Commun. Trust. 2013, pp. 94–101, 2013, doi: 10.1109/TRUSTCOM.2013.16.
H. Zhou, G. Yang, Y. Xiang, Y. Bai, and W. Wang, “A Lightweight Matrix Factorization for Recommendation With Local Differential Privacy in Big Data,” IEEE Trans. Big Data, vol. 9, no. 1, pp. 160–173, Feb. 2023, doi: 10.1109/TBDATA.2021.3139125.
A. Nakamura, K. Naito, and T. Yamazato, “Distributed processing framework for cooperative service among edge devices,” Dig. Tech. Pap. - IEEE Int. Conf. Consum. Electron., vol. 2023-January, 2023, doi: 10.1109/ICCE56470.2023.10043588.
F. V. Meca, J. H. Ziegeldorf, P. M. Sanchez, O. G. Morchon, S. S. Kumar, and S. L. Keoh, “HIP Security architecture for the IP-based internet of things,” Proc. - 27th Int. Conf. Adv. Inf. Netw. Appl. Work. WAINA 2013, pp. 1331–1336, 2013, doi: 10.1109/WAINA.2013.158.
D. Liu, P. Ning, and L. I. Rongfang, “Establishing pairwise keys in distributed sensor networks,” ACM Trans. Inf. Syst. Secur., vol. 8, no. 1, pp. 41–77, Feb. 2005, doi: 10.1145/1053283.1053287.
T. Ito, H. Ohta, N. Matsuda, and T. Yoneda, “A key pre-distribution scheme for secure sensor networks using probability density function of node deployment,” SASN’05 - Proc. 2005 ACM Work. Secur. Ad Hoc Sens. Networks, vol. 2005, pp. 69–75, 2005, doi: 10.1145/1102219.1102233.
L. Eschenauer and V. D. Gligor, “A key-management scheme for distributed sensor networks,” Proc. ACM Conf. Comput. Commun. Secur., pp. 41–47, 2002, doi: 10.1145/586110.586117.
G. De Meulenaer, F. Gosset, F. X. Standaert, and O. Pereira, “On the energy cost of communication and cryptography in wireless sensor networks,” Proc. - 4th IEEE Int. Conf. Wirel. Mob. Comput. Netw. Commun. WiMob 2008, pp. 580–585, 2008, doi: 10.1109/WIMOB.2008.16.
W. Du, J. Deng, and Y. S. Han, “A key predistribution scheme for sensor networks using deployment knowledge,” IEEE Trans. Dependable Secur. Comput., vol. 3, no. 1, pp. 62–77, 2006, doi: 10.1109/TDSC.2006.2.
E. Rescorla, “Diffie-Hellman Key Agreement Method,” Jun. 1999, doi: 10.17487/RFC2631.
Q. Jing, A. V. Vasilakos, J. Wan, J. Lu, and D. Qiu, “Security of the Internet of Things: perspectives and challenges,” Wirel. Networks, vol. 20, no. 8, pp. 2481–2501, Oct. 2014, doi: 10.1007/S11276-014-0761-7.
R. Hummen, J. H. Ziegeldorf, H. Shafagh, S. Raza, and K. Wehrle, “Towards viable certificate-based authentication for the Internet of Things,” HotWiSec 2013 - Proc. 2013 ACM Work. Hot Top. Wirel. Netw. Secur. Priv., pp. 37–41, 2013, doi: 10.1145/2463183.2463193.
S. Sicari, A. Rizzardi, L. A. Grieco, and A. Coen-Porisini, “Security, privacy and trust in Internet of things: The road ahead,” Comput. Networks, vol. 76, pp. 146–164, Jan. 2015, doi: 10.1016/J.COMNET.2014.11.008.
R. Roman, J. Zhou, and J. Lopez, “On the features and challenges of security and privacy in distributed internet of things,” Comput. Networks, vol. 57, no. 10, pp. 2266–2279, Jul. 2013, doi: 10.1016/J.COMNET.2012.12.018.
K. T. Nguyen, M. Laurent, and N. Oualha, “Survey on secure communication protocols for the Internet of Things,” Ad Hoc Networks, vol. 32, pp. 17–31, Sep. 2015, doi: 10.1016/J.ADHOC.2015.01.006.
D. Miorandi, S. Sicari, F. De Pellegrini, and I. Chlamtac, “Internet of things: Vision, applications and research challenges,” Ad Hoc Networks, vol. 10, no. 7, pp. 1497–1516, 2012, doi: 10.1016/J.ADHOC.2012.02.016.
S. A. A. Shukor, M. Q. Aminuddin, and E. J. Rushforth, “Managing huge point cloud data through geometrical-based registration,” ACM Int. Conf. Proceeding Ser., Mar. 2017, doi: 10.1145/3018896.3056783.
M. A. Taiye, S. S. Kamaruddin, and F. K. Ahmad, “Combined WSD algorithms with LSA to identify semantic similarity in unstructured textual data,” ACM Int. Conf. Proceeding Ser., Mar. 2017, doi: 10.1145/3018896.3056785.
A. Harit, A. Ezzati, and R. Elharti, “Internet of things security: Challenges and perspectives,” ACM Int. Conf. Proceeding Ser., Mar. 2017, doi: 10.1145/3018896.3056784.
M. Javaid and I. H. Khan, “Internet of Things (IoT) enabled healthcare helps to take the challenges of COVID-19 Pandemic,” J. Oral Biol. Craniofacial Res., vol. 11, no. 2, pp. 209–214, Apr. 2021, doi: 10.1016/J.JOBCR.2021.01.015.
A. Ghasempour, “Internet of things in smart grid: Architecture, applications, services, key technologies, and challenges,” Inventions, vol. 4, no. 1, Mar. 2019, doi: 10.3390/INVENTIONS4010022.
P. Radanliev and D. De Roure, “Alternative mental health therapies in prolonged lockdowns: narratives from Covid-19,” Health Technol. (Berl)., vol. 11, no. 5, pp. 1101–1107, Sep. 2021, doi: 10.1007/S12553-021-00581-3.
S. Madakam, R. Ramaswamy, and S. Tripathi, “Internet of Things (IoT): A Literature Review,” J. Comput. Commun., vol. 03, no. 05, pp. 164–173, 2015, doi: 10.4236/JCC.2015.35021.
J. Pike, T. Bogich, S. Elwood, D. C. Finnoff, and P. Daszak, “Economic optimization of a global strategy to address the pandemic threat,” Proc. Natl. Acad. Sci. U. S. A., vol. 111, no. 52, pp. 18519–18523, Dec. 2014, doi: 10.1073/PNAS.1412661112.
T. Mohammed, C. Jean-Yves, B. Peter, and R. Christophe, “Petrogenesis of the post-collisional Bled M’Dena volcanic ring complex in Reguibat Rise (western Eglab shield, Algeria),” J. African Earth Sci., vol. 166, Jun. 2020, doi: 10.1016/J.JAFREARSCI.2015.04.003.
P. J. Ryan and R. B. Watson, “Research challenges for the internet of things: What role can or play?,” Systems, vol. 5, no. 1, Mar. 2017, doi: 10.3390/SYSTEMS5010024.
E. A. Kosmatos, N. D. Tselikas, and A. C. Boucouvalas, “Integrating RFIDs and Smart Objects into a UnifiedInternet of Things Architecture,” Adv. Internet Things, vol. 01, no. 01, pp. 5–12, 2011, doi: 10.4236/AIT.2011.11002.
P. Radanliev and D. De Roure, “Epistemological and bibliometric analysis of ethics and shared responsibility—health policy and IoT systems,” Sustain., vol. 13, no. 15, Aug. 2021, doi: 10.3390/SU13158355.
S. Rivard and S. L. Huff, “Factors of Success for End-User Computing,” Commun. ACM, vol. 31, no. 5, pp. 552–561, May 1988, doi: 10.1145/42411.42418.
B. R. Hayes-Gill, “Monica Healthcare: From the research laboratory to commercial reality—A real-life case study,” Healthc. Technol. Lett., vol. 8, no. 1, pp. 1–10, Feb. 2021, doi: 10.1049/HTL2.12004.
S. A. Kumar, T. Vealey, and H. Srivastava, “Security in internet of things: Challenges, solutions and future directions,” Proc. Annu. Hawaii Int. Conf. Syst. Sci., vol. 2016-March, pp. 5772–5781, Mar. 2016, doi: 10.1109/HICSS.2016.714.
W. V. B. de Souza et al., “Using Crowdstorm to Prospect Innovations in Federal Institutions of Education in Brazil to Reduce Its Consumption of Electric Energy,” 49th Hawaii Int. Conf. Syst. Sci. (HICSS 2016), pp. 2819–2828, 2016, doi: 10.1109/HICSS.2016.353.
C. Dobre, L. Bajenaru, I. A. Marinescu, and M. Tomescu, “Improving the quality of life for older people: From smart sensors to distributed platforms,” Proc. - 2019 22nd Int. Conf. Control Syst. Comput. Sci. CSCS 2019, pp. 636–642, May 2019, doi: 10.1109/CSCS.2019.00115.
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 50SEA

This work is licensed under a Creative Commons Attribution 4.0 International License.




















